
Rapid7 has uncovered a critical vulnerability in Brother multifunction printers that allows unauthenticated attackers to remotely generate administrative passwords using leaked serial numbers, an issue that cannot be fully mitigated with firmware updates alone.
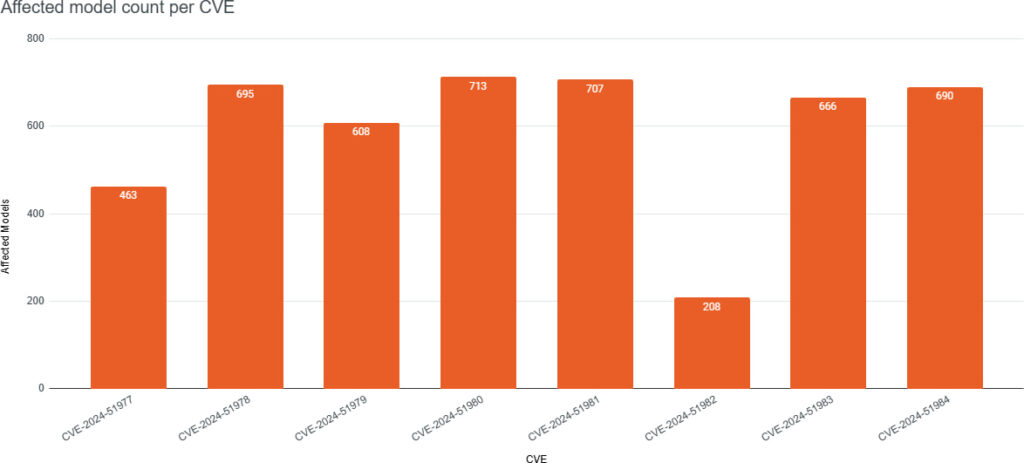
The vulnerability, tracked as CVE-2024-51978, affects hundreds of Brother devices and is also present to varying degrees across models from FUJIFILM Business Innovation, Ricoh, Toshiba Tec Corporation, and Konica Minolta.
The vulnerability was discovered by Stephen Fewer at Rapid7, as part of a year-long zero-day research project into Brother’s range of printers, scanners, and label makers. In total, 748 models across five vendors are affected by one or more of the eight vulnerabilities disclosed, with CVE-2024-51978 standing out due to its persistent nature.
Rapid7
The flaw stems from the default password generation mechanism used in Brother devices, which deterministically derives an administrator password from the device’s serial number during manufacturing. Once an attacker obtains the serial number, either via HTTP, HTTPS, IPP endpoints (CVE-2024-51977), PJL commands on port 9100, or SNMP queries, they can use a publicly disclosed algorithm to calculate the corresponding default admin password. If this password remains unchanged by the user, the attacker gains full control of the device without authentication.
According to Rapid7’s technical analysis, the password-generation routine uses a salted SHA-256 hash of the serial number, applies base64 encoding, and then substitutes certain characters. Despite its complexity, this method offers no real cryptographic protection and is easily replicated by attackers using provided proof-of-concept scripts.
Brother acknowledged that CVE-2024-51978 cannot be fully resolved via firmware updates and has instead introduced a fix that requires changes at the manufacturing level. Devices produced prior to this adjustment remain vulnerable and must rely on documented workarounds. In contrast, the other seven vulnerabilities, ranging from buffer overflows and denial-of-service flaws to SSRF and credential leakage, have been addressed via firmware updates.
Brother Industries, Ltd. is a major player in the global printing market, providing devices for both home and enterprise environments. The wide model impact, 689 Brother devices alone, means that the risk footprint is significant, particularly in organizations with unmanaged or internet-exposed printers. Rapid7 observed over 5,700 Brother printer management interfaces accessible via the public internet as of May 2025.
Of the other affected vendors, 46 models from FUJIFILM Business Innovation, five from Ricoh, two from Toshiba Tec Corporation, and six from Konica Minolta were confirmed vulnerable. All vendors coordinated with Rapid7 and JPCERT/CC in a thirteen-month disclosure process that culminated in a public release on June 25, 2025.
To mitigate risk, users should:
- Immediately change the default administrator password on all affected devices.
- Apply firmware updates where available, as issued by Brother, FUJIFILM, Ricoh, Toshiba, and Konica Minolta.
- Disable unnecessary network services such as SNMP or PJL if not required.
- Restrict access to printer interfaces using firewall rules or network segmentation.
- Monitor printer configurations for unauthorized changes or unexpected behavior.







Leave a Reply