
Mandiant has identified a sophisticated threat campaign by the financially motivated group UNC5537, targeting Snowflake customer database instances for data theft and extortion. This campaign, which leverages stolen customer credentials, poses a significant risk to all Snowflake users.
Previously, various data breach disclosures we reported on concerning Tickemaster, Santander bank, and Advanced Auto Parts, pointed at a breach on Snowflake, which the firm denied. However, not many details about the attacks, initial access methods, point of breach, and who conducted them were made available.
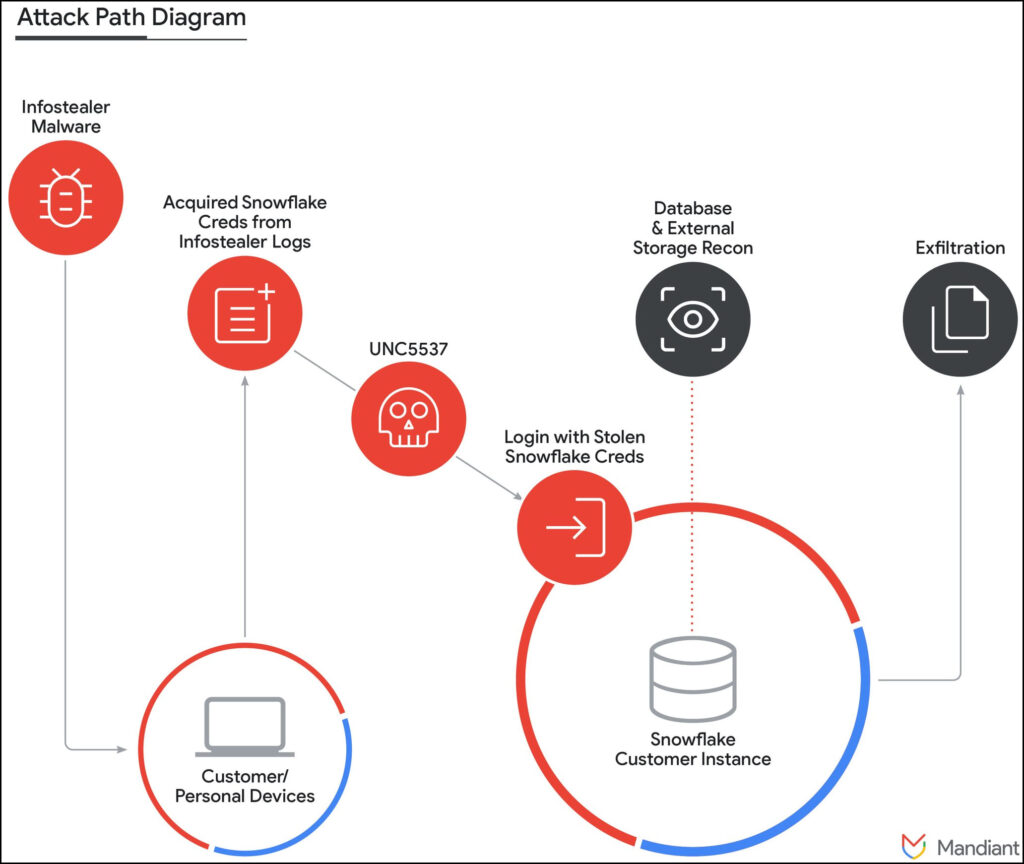
Mandiant's researchers now uncovered that UNC5537 is exploiting compromised customer credentials, often obtained through infostealer malware. The group uses these credentials to gain unauthorized access to Snowflake instances, exfiltrating valuable data which they then attempt to sell on cybercrime forums or use for extortion.
Notably, there is no evidence suggesting that the compromise stemmed from a breach within Snowflake's enterprise environment; rather, it is due to stolen customer credentials.
165 Snowflake customers impacted
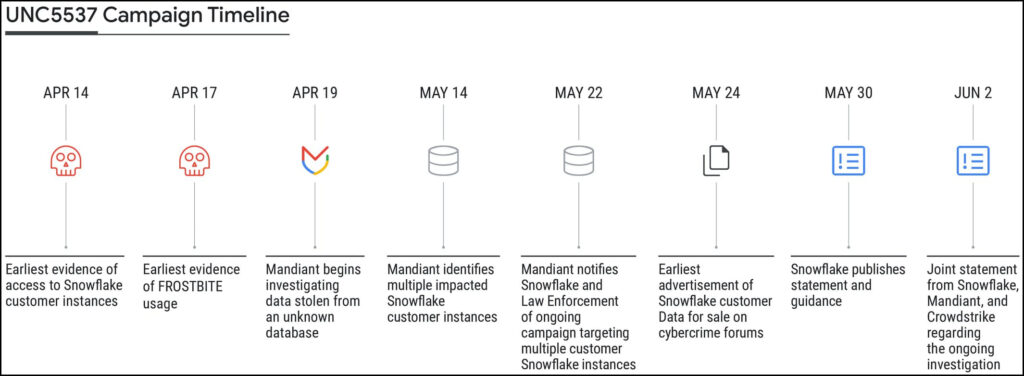
In April 2024, Mandiant first became aware of this threat after analyzing stolen database records from a compromised Snowflake instance. The victim organization engaged Mandiant for a thorough investigation, which revealed that their instance was accessed using credentials stolen by infostealer malware.
Crucially, this account lacked multi-factor authentication (MFA), a security measure that could have potentially prevented the breach. By late May 2024, Mandiant identified a broader campaign affecting numerous Snowflake customers and began notifying approximately 165 potentially exposed organizations through their Victim Notification Program.
Snowflake’s Customer Support has been actively engaged with these customers to secure their accounts and data.
Mandiant
Snowflake, a leading multi-cloud data warehousing platform, is widely used for storing and analyzing vast amounts of structured and unstructured data. The scale and sensitivity of the data stored in Snowflake instances make it a lucrative target for threat actors like UNC5537.
UNC5537 profile and tactics
This group has been active since at least November 2020, primarily using credentials exposed by various infostealer malware, including VIDAR, RISEPRO, REDLINE, RACOON STEALER, LUMMA, and META. Mandiant’s analysis revealed that a significant portion of the credentials exploited by UNC5537 were from historical infostealer infections, highlighting the importance of regular credential updates and robust security practices.
UNC5537's success in compromising Snowflake customer instances can be attributed to several key factors such as:
- Lack of MFA on affected accounts, allowing access with just a valid username and password.
- Long-standing validity of stolen credentials, sometimes remaining unchanged for years.
- Absence of network allow lists, which could restrict access to trusted locations only.
The threat actor uses various tools and methods to access and exfiltrate data from Snowflake instances. This includes native Snowflake tools like the web-based UI (SnowSight) and command-line interface (SnowSQL), as well as a custom utility named “rapeflake,” tracked by Mandiant as FROSTBITE. This utility performs reconnaissance on target instances, listing users, roles, IPs, session IDs, and organization names. Additionally, UNC5537 employs DBeaver Ultimate, a publicly available database management utility, to run queries across Snowflake instances.
Mandiant
Mandiant's ongoing investigation, in collaboration with Snowflake and relevant law enforcement agencies, aims to mitigate this threat and protect affected organizations. As part of their response, Snowflake published detailed detection and hardening guidance for their customers on May 30, 2024.
Defense recommendations include:
- Ensure all Snowflake accounts require MFA to add an extra layer of security.
- Regularly update and rotate credentials, especially for accounts with elevated privileges.
- Restrict access to trusted IP ranges to prevent unauthorized access.
- Set up alerts for unusual access patterns or failed login attempts.
- Train employees and contractors on safe computing practices to avoid infostealer infections.







Leave a Reply