
A hacker group has claimed responsibility for a significant data breach at Russian cybersecurity company Doctor Web, alleging they have stolen over 10 terabytes of sensitive data.
The group made the announcement on Telegram, claiming to have accessed various internal systems and databases. However, Doctor Web has publicly denied the extent of the hackers' claims, asserting that no user data was compromised during the attack.
In a statement published on Doctor Web's official Telegram channel today, the company acknowledged that it had indeed suffered a targeted cyberattack in September. This aligns with a previous disclosure the company made, where they reported detecting and containing an attempted breach on September 14.
Doctor Web reiterated that they took immediate action by disconnecting all affected resources from the network and conducting thorough security checks. Despite the hackers' claims, the firm emphasized that the majority of the information being circulated does not reflect reality.
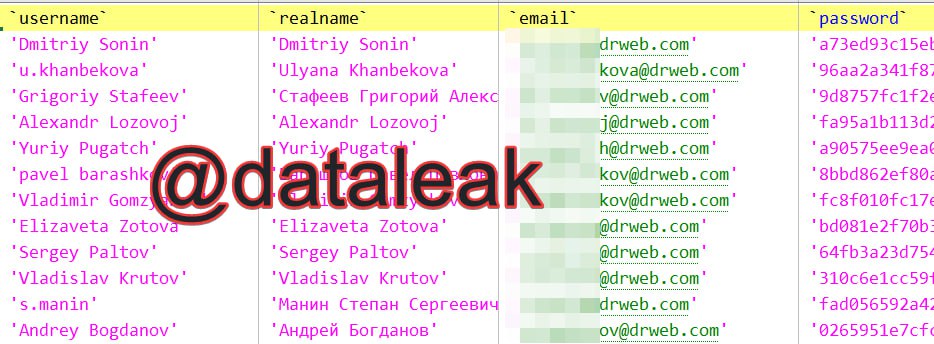
The hacker group, which remains unnamed, alleges they infiltrated Doctor Web’s internal network for over a month and stole data from several systems, including the company’s GitLab server, Confluence, and Jenkins. They claim to have compromised critical systems that hold internal development data and customer information.
Specifically, the attackers claim to have accessed internal databases such as ldap.dev.drweb[.]com and vxcube.drweb[.]com. According to their posts, the attack’s primary objective was to extort a ransom from the company — a demand that Doctor Web categorically refused to entertain.
CyberInsider
Doctor Web, founded in 1992, is a prominent Russian cybersecurity firm known for its Dr.Web antivirus software. The company provides services to millions of users worldwide, making it a key player in the cybersecurity industry. The reported breach, if fully confirmed, would be a major blow to its reputation and credibility as a protector of online security.
Russian site xakep.ru claims that a former Dr. Web employee confirmed to them anonymously that the leaked data is authentic. CyberInsider has contacted the antivirus company for a statement on this, but we are still waiting for their response.







Leave a Reply