
A newly uncovered cyberattack shows how a hacking group known as UNC2891 used a small, off-the-shelf Raspberry Pi computer and obscure Linux tricks to break into a bank’s internal network.
Their goal was to silently hijack the system that controls ATM transactions and trigger fraudulent withdrawals.
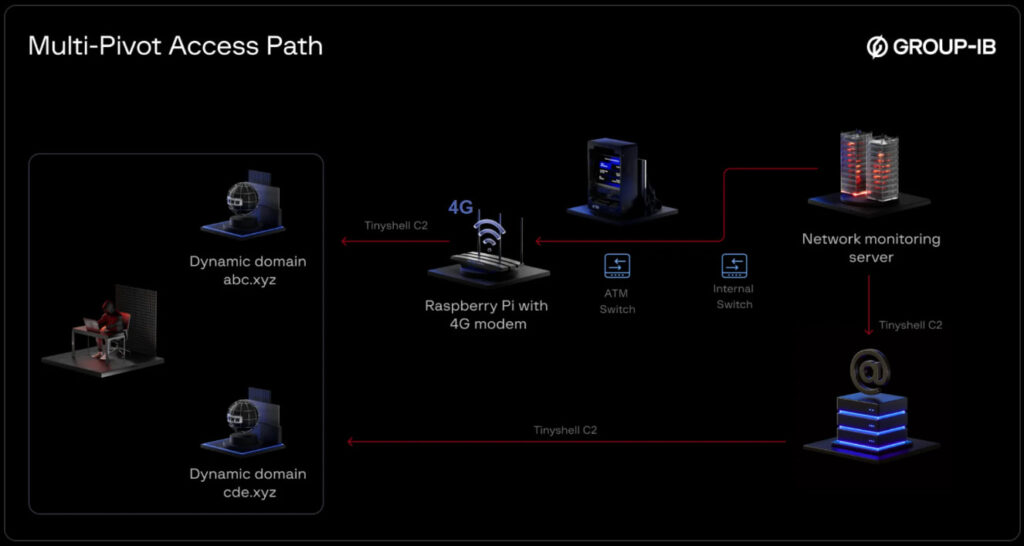
The incident, discovered by cybersecurity firm Group-IB, combined physical access to banking infrastructure with digital stealth techniques rarely seen outside of high-level espionage. According to investigators, the attackers installed the Raspberry Pi, a versatile single-board computer roughly the size of a credit card, inside the bank’s network by physically connecting it to the same switch as an ATM. Equipped with a 4G modem, the device allowed the attackers to remotely control systems over mobile networks, completely bypassing traditional network firewalls.
Group-IB discovered the breach while investigating unusual network activity. The attackers used a lightweight backdoor tool called TINYSHELL to keep in touch with the implant using a Dynamic DNS domain, an approach that helped them hide their server’s location and rotate addresses quickly if detected.
The target was a bank with regional ATM infrastructure, where internal servers like the mail system and a network monitoring server became key stepping stones. Once the attackers gained access, they moved laterally across the bank’s systems and planted backdoors that remained hidden even from standard security tools.
Group-IB
The real innovation came in how the hackers evaded detection. Traditional tools that scan running programs or analyze disk contents came up empty. Investigators were puzzled when they saw that the server was clearly sending data to suspicious destinations every 10 minutes, but no malicious processes showed up in the process list.
That’s because the attackers had used a rarely seen Linux feature called bind mounts to hide their tracks. This technique effectively made the malware processes invisible by redirecting parts of the operating system used for inspection.
A deeper memory analysis finally uncovered the disguised backdoors. They were named after legitimate software like lightdm, a legitimate Linux login manager, but were running from unusual directories like /tmp and .snapd, which are often exploited by attackers. These fake processes were quietly maintaining connections to both the implanted Raspberry Pi and an internal mail server.
Group-IB says the attackers intended to deploy a powerful rootkit known as CAKETAP, designed to manipulate responses from Hardware Security Modules (HSMs), specialized devices banks use to authorize financial transactions. By spoofing those responses, the attackers could have tricked ATMs into spitting out cash without triggering alerts, but the operation was caught before they could pull off the heist.







Leave a Reply