
Aqua Nautilus researchers have uncovered a campaign targeting misconfigured Jupyter servers to facilitate illegal sports streaming. During a recent threat-hunting operation, attackers were observed leveraging the JupyterLab and Jupyter Notebook environments to deploy the popular multimedia tool ffmpeg for live-stream capture and broadcasting unauthorized streams.
Aqua Nautilus discovered the campaign while analyzing events collected from their honeypot infrastructure, which mimics real-world development environments to attract malicious actors. The researchers detected unusual activity involving the ffmpeg tool, commonly used for audio and video streaming. While benign on its own, ffmpeg was deployed to capture and redistribute live sports broadcasts via compromised servers.
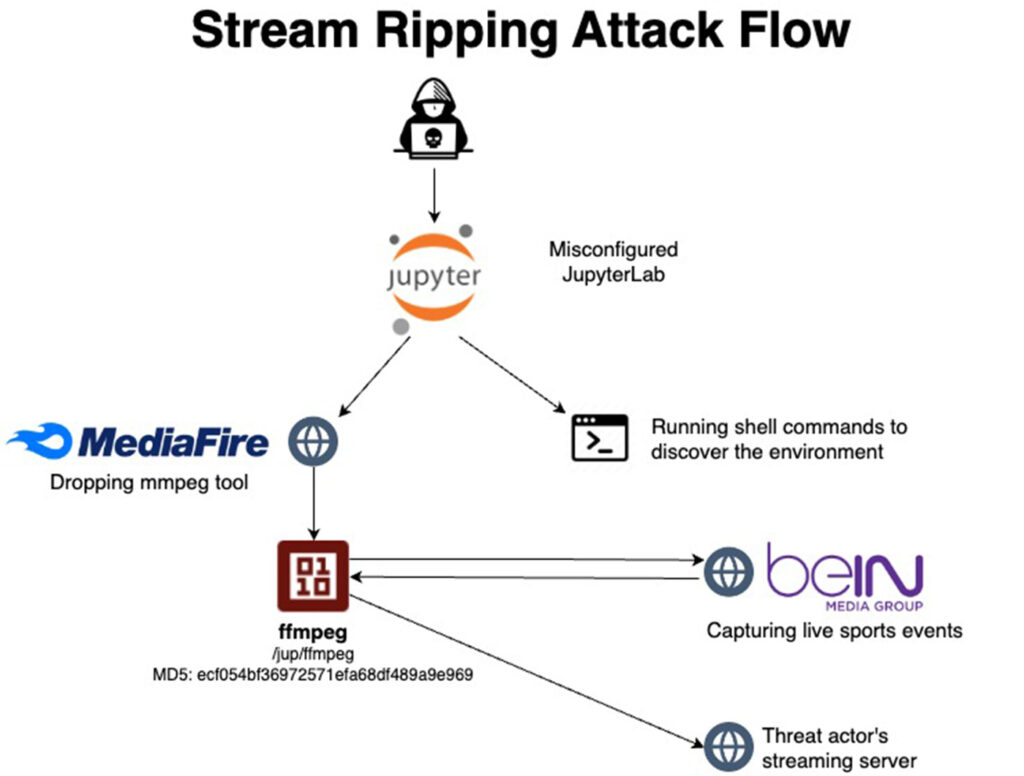
The researchers observed the exploitation of unsecured JupyterLab servers, which had been left exposed to the internet without proper authentication. This misconfiguration allowed attackers to execute commands remotely, download ffmpeg from an unverified source, and redirect streams to external platforms for unauthorized distribution.
The attack followed a straightforward sequence:
- Gain initial access by exploiting unsecured Jupyter servers, often left open by practitioners unfamiliar with security best practices.
- Using Jupyter’s command interface, install ffmpeg and configure it for live-stream capture.
- Redirect captured streams to external platforms, like Ustream.tv, for illicit monetization.
The attackers specifically targeted high-profile broadcasts, including a UEFA Champions League match aired by beIN Sports. Evidence pointed to servers associated with Algerian IPs, suggesting potential Arabic-speaking origins.
Aqua Security
Broader impact and potential risks
This attack highlights the risks of leaving Jupyter environments misconfigured. Widely used by data scientists and researchers, JupyterLab and Jupyter Notebook are powerful tools that, when exposed without proper safeguards, become easy targets for exploitation. Shodan data reveals approximately 15,000 Jupyter servers are internet-accessible, with about 1% configured to allow remote code execution.
Such misuse poses broader dangers beyond illegal streaming, with some damaging scenarios including:
- Attackers access sensitive information stored on the compromised servers.
- Organizations’ bandwidth is consumed by unauthorized streaming, potentially incurring significant costs.
- Exploited servers suffer from performance degradation, denial-of-service, or lateral movement within corporate networks.







Leave a Reply