
Hackers are actively targeting the Progress WhatsUp Gold network monitoring software, leveraging a recently disclosed SQL injection vulnerability (CVE-2024-6670) to breach systems. The exploit, which has been circulating as a public Proof-of-Concept (PoC), was observed by the Shadowserver Foundation, which detected the malicious activity on their honeypots on September 3, 2024. The vulnerability is considered critical, with a CVSS score of 9.8, underscoring the urgent need for users to update their systems.
The issue, which affects all versions of WhatsUp Gold released before version 2024.0.0, was disclosed by Sina Kheirkhah of the Summoning Team in collaboration with the Trend Micro Zero Day Initiative (ZDI). According to Kheirkhah's report, the vulnerability allows unauthenticated attackers to exploit a SQL injection in the ‘/NmConsole/Platform/PerformanceMonitorErrors/HasErrors' endpoint, potentially leading to authentication bypass and even remote code execution (RCE).
Discovery and impact
WhatsUp Gold is widely used by organizations to monitor the status and performance of network devices, servers, and applications, both on-premises and in the cloud. The software’s extensive capabilities, including the management of sensitive credentials for various network devices, make it a high-value target for attackers. A successful breach could give attackers control over an organization’s network, enabling them to launch further attacks or exfiltrate sensitive data.
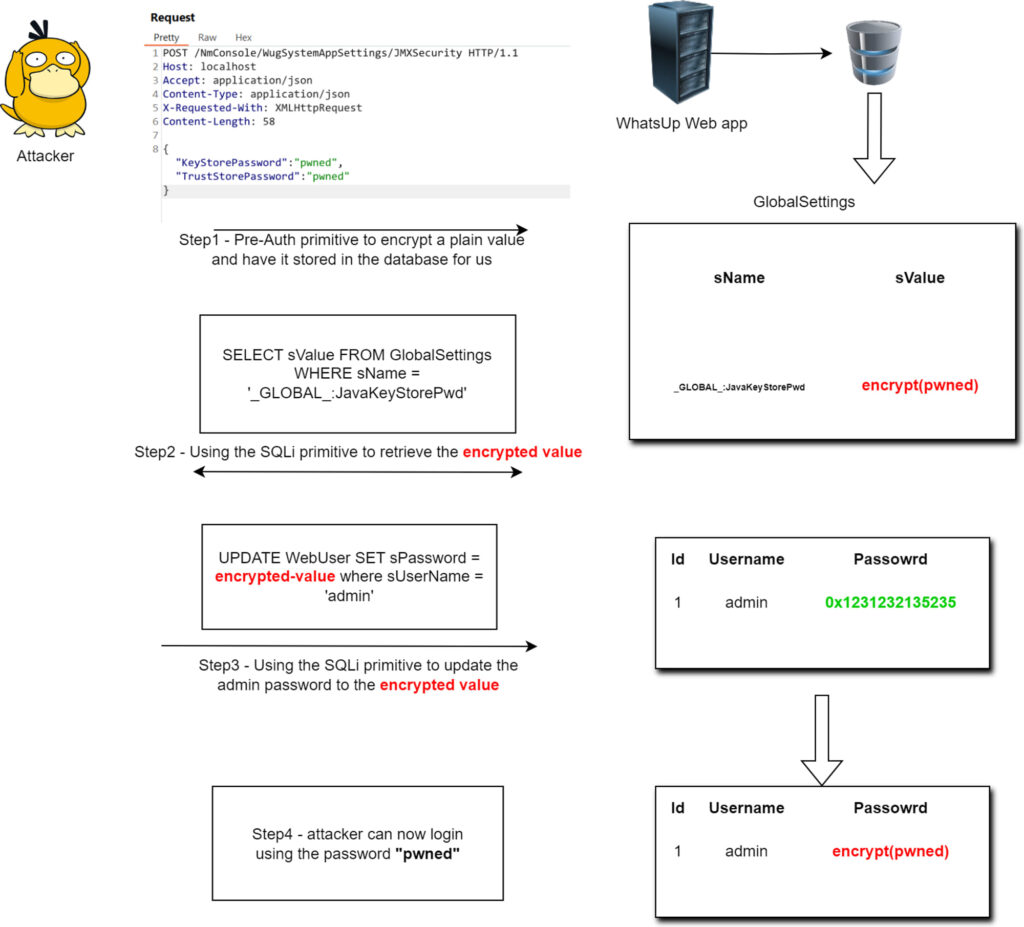
The vulnerability was first reported to the Zero Day Initiative on May 22, 2024, by Kheirkhah. It allows an attacker to retrieve or overwrite encrypted passwords stored in the database, using the vulnerability to gain privileged access to the WhatsUp Gold instance. The exploitation process involves crafting specific SQL queries that bypass the authentication mechanism, enabling attackers to control the application and potentially the entire network infrastructure managed by WhatsUp Gold.
summoning.team
Progress Software issued an advisory on August 16, 2024, urging users to update to version 2024.0.0 to mitigate the risk. The advisory highlighted that although no successful attacks had been reported at the time of the bulletin, the vulnerability could have severe implications if exploited.
Exploitation and response
The Shadowserver Foundation’s detection of active exploitation attempts indicates that attackers are now capitalizing on the public PoC. These attempts involve executing SQL queries that retrieve encrypted passwords from the database, which are then decrypted and used to gain administrative access to the system.
To mitigate the risk posed by CVE-2024-6670, users should:
- Upgrade to WhatsUp Gold version 2024.0.0 or later to close the vulnerability.
- Check logs for unusual activity, especially related to the /NmConsole/Platform/PerformanceMonitorErrors/HasErrors endpoint.
- Ensure that database permissions are configured with the principle of least privilege to limit the impact of potential SQL injection attacks.
- Segment networks to limit the spread of any breach originating from a compromised WhatsUp Gold instance.






Leave a Reply