
Google's Threat Intelligence Group (GTIG) revealed that financially motivated threat actors are exploiting Mullvad VPN to mask data exfiltration operations targeting Salesforce environments.
The attackers, tracked under the cluster UNC6040, have successfully compromised multiple organizations by leveraging voice phishing (vishing) tactics to gain unauthorized access to sensitive cloud data.
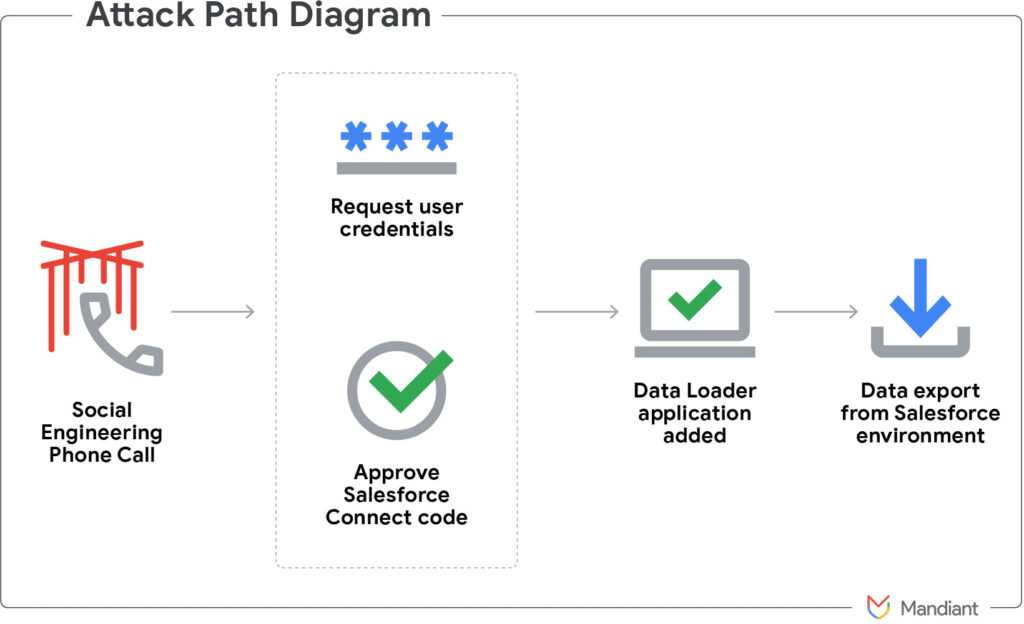
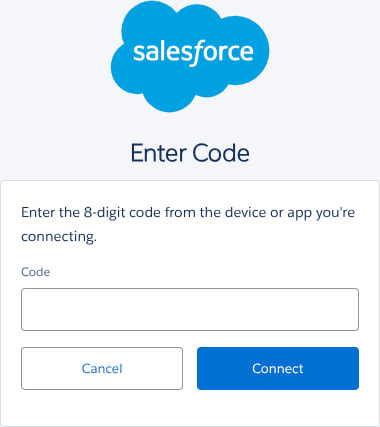
UNC6040's campaigns have been active for several months, primarily targeting English-speaking employees in multinational corporations. The attacks begin with vishing calls in which adversaries impersonate IT support staff, coaxing victims into authorizing a malicious connected application inside their organization's Salesforce instance. This rogue app, often a tampered version of Salesforce's Data Loader tool, enables the attackers to access and exfiltrate substantial volumes of enterprise data without exploiting any Salesforce software vulnerability.
Mullvad VPN, a privacy-focused virtual private network service that does not log user activity, was used extensively to obfuscate the source of the data exfiltration. The threat group's infrastructure included IP addresses from Mullvad to remotely access the victim organizations' Salesforce systems and conduct lateral movement across other cloud services, including Okta, Microsoft 365, and Meta's Workplace platform. Mullvad's commitment to anonymity has made it a preferred tool among privacy advocates, but also a vector for threat actors aiming to cover their tracks during cyber intrusions.
Salesforce, a leading cloud-based CRM platform used by businesses globally, provides tools such as Data Loader for bulk data operations. In this campaign, attackers abused this tool by instructing victims to approve a “connected app” that resembled the legitimate Data Loader but operated under misleading names like “My Ticket Portal.” Once authorized, the tool granted adversaries extensive access via OAuth tokens. In some cases, the attackers tested small data transfers before scaling up to full-table extractions, with varying success depending on the organization's monitoring capabilities.
The sophistication of the Data Loader abuse varied across incidents, indicating either a range of skill levels within UNC6040 or collaboration with other cybercriminals. Google notes that extortion often followed weeks or months after the breach, sometimes accompanied by claims of affiliation with ShinyHunters, a known data extortion and leak group, likely as a pressure tactic rather than evidence of a direct partnership.
GTIG also identified infrastructure overlap between UNC6040 and other groups suspected to be part of the loosely affiliated cybercriminal collective known as “The Com.” Common elements include targeting Okta credentials, leveraging IT support impersonation, and focusing on multinational firms.







Leave a Reply