Elastic Security researchers have discovered a new infection technique named GrimResource, leveraging Microsoft Management Console (MMC) files to enable attackers to execute arbitrary code with minimal detection. This novel method, detected in the wild on June 6th, 2024, represents an evolving threat landscape as adversaries adapt to recent security changes by Microsoft.
Microsoft Management Console (MMC) is a vital component of Windows, providing system administrators with a unified interface to manage various system tools and snap-ins. The exploitation of MMC through GrimResource poses a significant risk due to its potential to bypass traditional security measures and gain unauthorized access.
Discovery and analysis
The GrimResource technique was uncovered by Elastic researchers amidst ongoing scrutiny of alternative infection vectors following Microsoft's decision to disable Office macros by default for internet-sourced documents. As attackers shift their focus to methods like JavaScript, MSI files, LNK objects, and ISOs, the GrimResource approach stands out due to its low detection rates and effective evasion mechanisms.
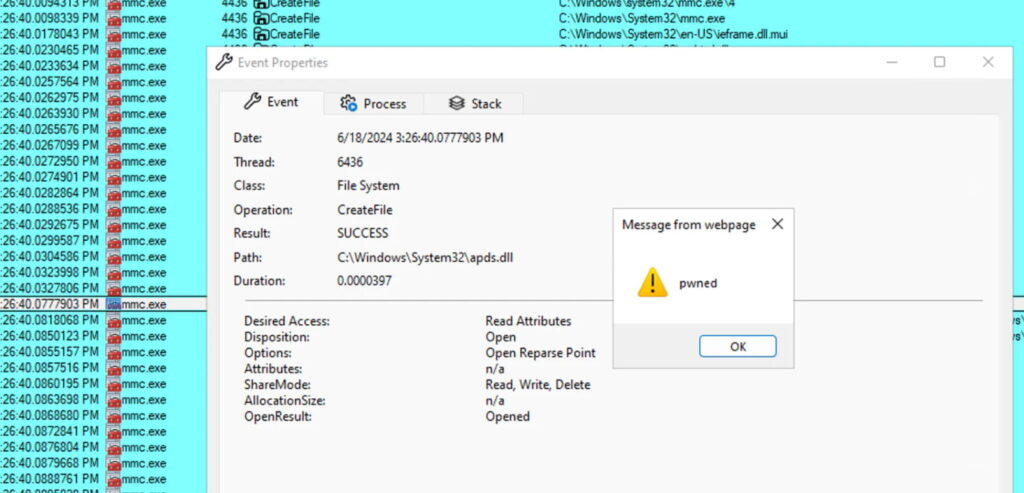
GrimResource exploits a known cross-site scripting (XSS) vulnerability in the apds.dll library. By referencing this vulnerable resource within the StringTable section of a specially crafted MSC file, attackers can execute arbitrary JavaScript in the context of mmc.exe. The technique further integrates DotNetToJScript to achieve arbitrary code execution, making it a formidable tool for initial access and defense evasion.
Infection chain
The infection starts with a transformNode obfuscation technique to evade ActiveX security warnings.
An obfuscated embedded VBScript sets the target payload in environment variables.
The VBScript uses DotNetToJScript to execute an embedded .NET loader, termed PASTALOADER.
PASTALOADER retrieves the payload from environment variables and injects it into a new dllhost.exe instance using the DirtyCLR technique and function unhooking.
In the observed sample, the final payload was Cobalt Strike, a popular post-exploitation tool.
Elastic Security
Detection and mitigation
Elastic Security has developed detection rules to identify the GrimResource technique and its associated behaviors. The primary detection focuses on suspicious execution patterns involving ‘mmc.exe' and the use of ‘apds.dll.'
Detection rules:
Suspicious Execution via Microsoft Common Console
process where event.action == "start" and
process.parent.executable : "?:\Windows\System32\mmc.exe" and process.parent.args : "*.msc".NET COM Object Creation in Non-Standard Windows Script Interpreter
api where process.code_signature.subject_name : "Microsoft" and process.Ext.api.name == "VirtualAlloc" and process.Ext.api.parameters.protection == "RWX" and process.thread.Ext.call_stack_summary : "|mscoree.dll|combase.dll|jscript.dll|*"Script Execution via MMC Console File
sequence by process.entity_id with maxspan=1m
[process where event.action == "start" and
process.executable : "?:\Windows\System32\mmc.exe" and process.args : "*.msc"]
[file where event.action == "open" and file.path : "?:\Windows\System32\apds.dll"]






Leave a Reply