
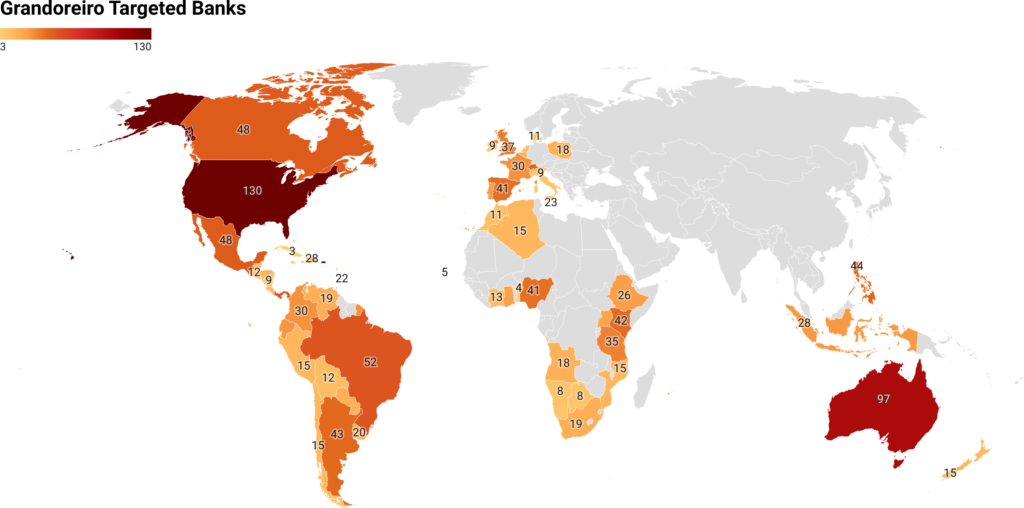
IBM X-Force has been monitoring an extensive series of phishing campaigns spreading the Grandoreiro banking trojan. These campaigns have expanded globally, impersonating government entities to target over 1,500 banks across 60 countries.
This re-emergence in activity happened after police in Brazil, working together with Interpol, Caixa Bank, ESET, and the police in Spain, arrested five individuals and disrupted the malware operation in January 2024.
The Grandoreiro banking trojan, likely operated as a Malware-as-a-Service (MaaS) now, has been tracked by IBM's X-Force team since March 2024. Researchers Golo Mühr and Melissa Frydrych have identified large-scale phishing campaigns utilizing this malware, noting significant updates and expanded targeting.
Latest campaigns
The latest Grandoreiro variant includes improvements in string decryption and the domain generating algorithm (DGA), allowing it to generate at least 12 command-and-control (C2) domains daily. Initially focused on Latin America, campaigns now target regions including Central/South America, Africa, Europe, and the Indo-Pacific.
Phishing emails often impersonate official entities, such as Mexico's Tax Administration Service (SAT), Mexico's Federal Electricity Commission (CFE), and the South African Revenue Service (SARS). Emails contain links leading to malware-laden ZIP files.
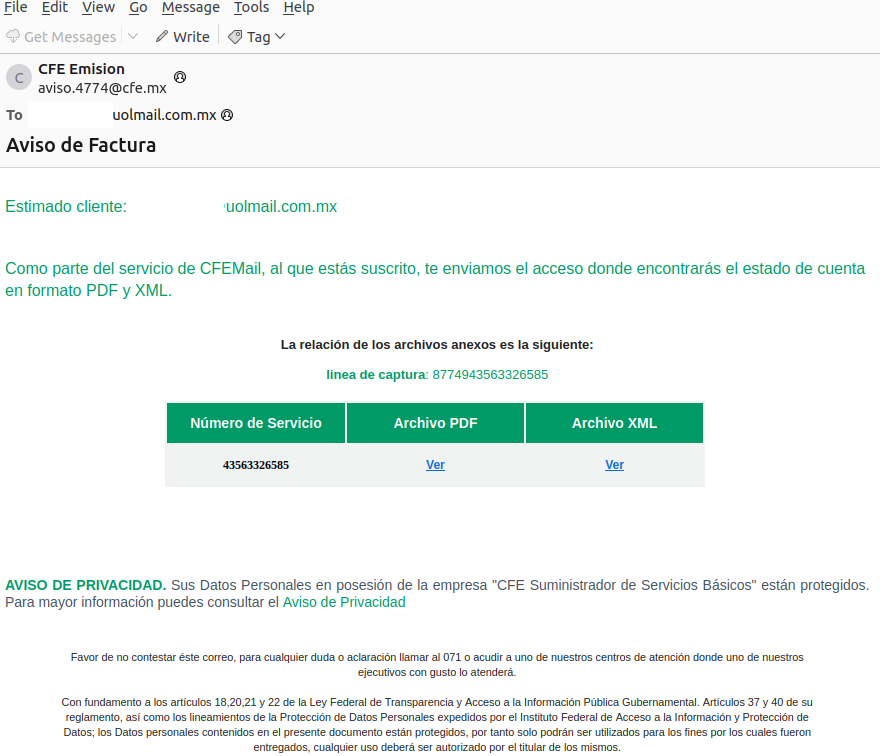
In Latin American campaigns, emails from entities like SAT and CFE prompt users to view invoices or account statements, leading to the download of ZIP files containing executable malware disguised as PDFs. Recent campaigns have targeted users in South Africa, impersonating SARS with emails that download a malware loader executable when links are clicked.
Malware capabilities
The malware's custom loader verifies the victim's legitimacy, gathers basic data, and executes the Grandoreiro trojan. It uses a CAPTCHA pop-up to bypass automated scanning and evades detection by bloating the executable size. The malware employs a complex decryption process involving multiple encryption layers and custom algorithms to retrieve the plaintext strings necessary for operation.
The malware collects extensive information from infected machines, including IP data, operating system details, and installed software, which is then sent to the C2 server. Grandoreiro uses DNS over HTTPS to avoid DNS-based blocking and employs a DGA for calculating active C2 domains. It sends encrypted requests to the C2 server for the final payload.
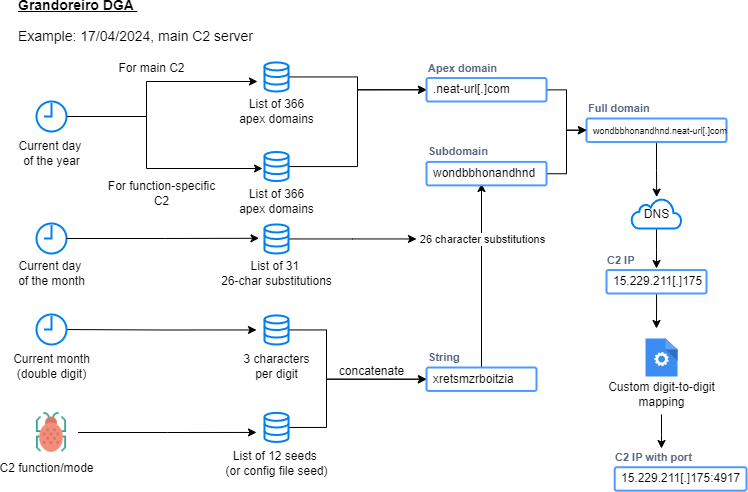
Grandoreiro establishes persistence via Windows registry keys, ensuring it runs on user login. The malware targets over 1,500 global banking applications, performing searches based on the victim's region to facilitate banking fraud. It harvests email addresses from infected hosts and uses Microsoft Outlook to propagate further phishing emails, contributing to its widespread reach.
Defense recommendations
To mitigate the risk posed by Grandoreiro, it is crucial to exercise caution with emails from root@yhsp.rufnag.com and avoid clicking on links or downloading attachments from unsolicited messages. Monitoring network traffic for multiple consecutive requests to http://ip-api.com/json can help identify potential infections.
Also, consider blocking domains generated by the malware's DGA and regularly check for unusual entries in Windows registry run keys. Ensure endpoint security software is installed and properly configured, and educate staff about phishing threats and safe email practices.







Leave a Reply