
Google has announced a significant enhancement to Chrome's security on Windows, aimed at combating the persistent threat of info-stealing malware.
With the introduction of App-Bound Encryption in Chrome 127, Google aims to make it much harder for cybercriminals to steal cookies and other sensitive data from the world's most popular and widely used web browser.
App-bound encryption
Chrome already utilizes several protective strategies, including Safe Browsing download protection, Device Bound Session Credentials, and account-based threat detection to flag the use of stolen cookies. However, these strategies have not fully mitigated the risk posed by malware capable of executing code as the logged-in user.
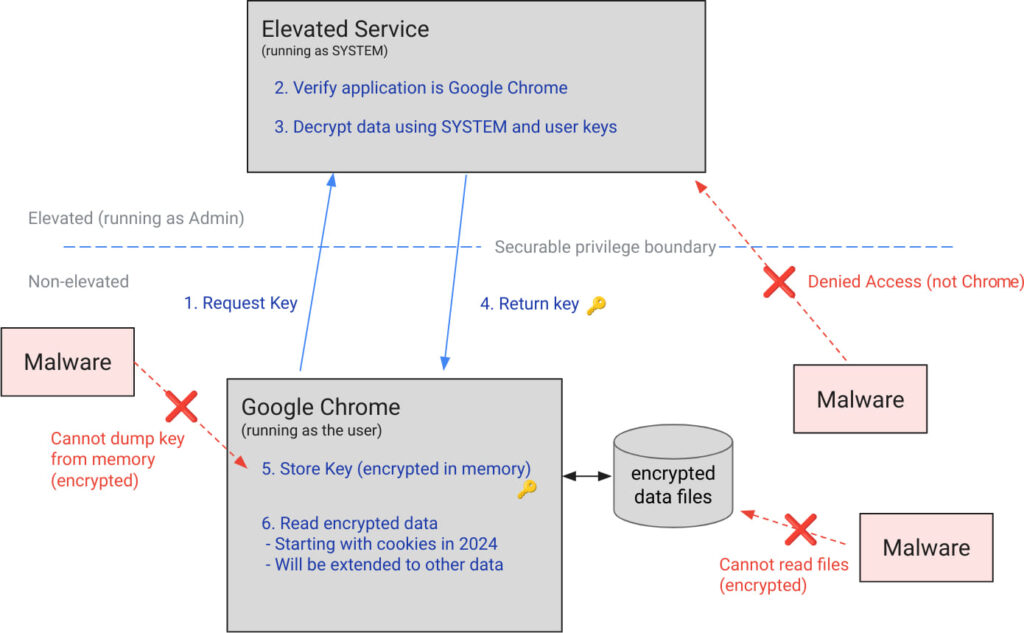
Chrome 127 introduces App-Bound Encryption to improve the Data Protection API (DPAPI) currently used on Windows. While DPAPI effectively protects data from unauthorized access by other users and defends against cold boot attacks, it is vulnerable to malware running as the logged-in user. This is where App-Bound Encryption comes into play, offering a more robust solution by tying the encryption of sensitive data directly to the identity of Chrome itself, much like macOS's Keychain.
The mechanism involves a privileged service that verifies the application's identity both during the encryption and decryption processes. This means that only Chrome, or applications verified as Chrome, can access the encrypted data. If any other application attempts to decrypt the data, the process will fail, making it significantly harder for malware to access sensitive information without being detected.
Implementation and future plans
Starting with Chrome 127, App-Bound Encryption will first secure cookies, with plans to extend this protection to passwords, payment data, and other persistent authentication tokens in future updates. This phased approach ensures that all sensitive user data will eventually benefit from this enhanced security measure.
By generating event logs for cookie decryption activities, Chrome further bolsters its detection capabilities. Malware now requires elevated system privileges or must inject code into Chrome to bypass these protections, actions that are more likely to be flagged by antivirus software due to their suspicious nature.
The introduction of the new feature is particularly beneficial for enterprise environments that restrict users from running downloaded files as administrators. In these settings, malware cannot simply request elevated privileges, forcing it to use more detectable techniques like code injection.
However, App-Bound Encryption's reliance on machine-bound encryption keys may pose challenges for environments utilizing roaming Chrome profiles across multiple machines. Enterprises should follow best practices for roaming profiles and can configure App-Bound Encryption through the new ApplicationBoundEncryptionEnabled policy. Chrome will also log failed verification attempts (Event ID 257) in the Application log to assist in detecting incompatibilities.
The introduction of App-Bound Encryption significantly strengthens Chrome's defenses against info-stealing malware, increases the complexity for attackers, and forces them to perform noisier actions that may expose their operations to monitoring tools.







Leave a Reply