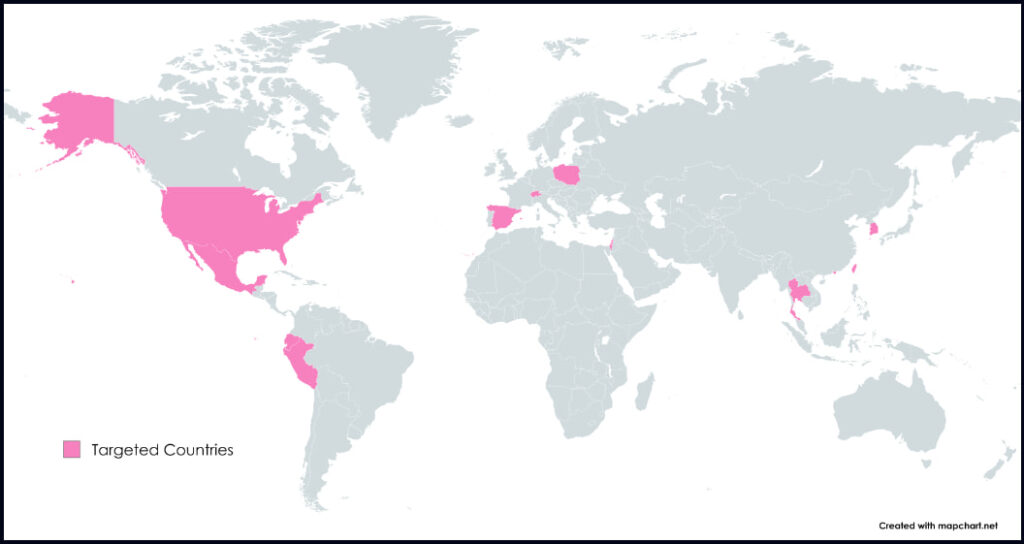
Check Point Research (CPR) has uncovered a large-scale phishing campaign dubbed “CopyRh(ight)adamantys,” using copyright infringement themes to deceive victims into installing Rhadamanthys version 0.7 — a powerful info-stealer. Active since July 2024, this campaign has targeted organizations worldwide across diverse industries, particularly in regions like the United States, Europe, East Asia, and South America.
Unlike previous incidents linking Rhadamanthys to nation-state actors, such as Iran's Void Manticore group, this campaign targets a wide array of industries with no apparent strategic ties, reinforcing its likely criminal and financially motivated nature.
Check Point Research
Campaign overview
The attackers impersonate well-known companies from sectors with high copyright activity, including entertainment, media, and technology, which enhances the credibility of their deceptive emails. Each email accuses the recipient of copyright violations, allegedly for unauthorized use of the impersonated company's content on social media platforms.
The emails, sent from a rotating array of Gmail accounts, vary in language and sender identity based on the targeted region. Check Point's analysis indicates that the attackers likely leverage automation, possibly powered by basic machine learning techniques, to customize these emails at scale.
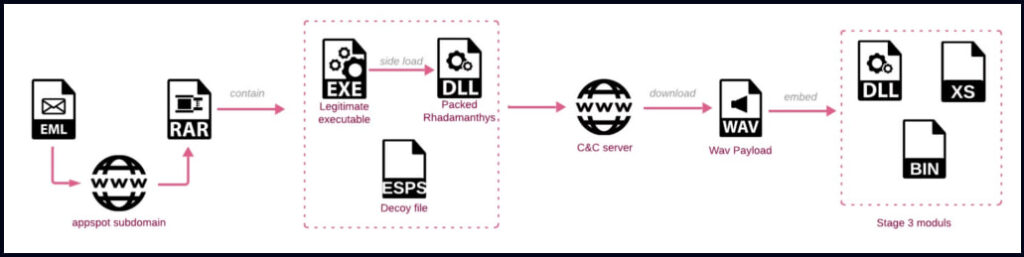
A critical aspect of this attack is the use of malicious archives, which are downloadable through links in the phishing emails. The archive files contain a password-protected ZIP, purportedly holding removal instructions, but actually host Rhadamanthys malware via DLL sideloading. Victims who download and execute these files initiate the infection process, allowing Rhadamanthys to implant itself on their systems.
Infection mechanics
The infection chain begins with spear-phishing emails directing users to cloud storage services such as Dropbox or Discord to download a malicious file. Once downloaded, the file contains three components:
- A legitimate executable.
- A sideloaded DLL containing the Rhadamanthys malware.
- A decoy document, often mimicking an Adobe or PDF file.
When the executable is launched, it loads the malicious DLL through DLL sideloading, initiating Rhadamanthys' installation. The malware then creates a persistent foothold on the compromised system by modifying registry keys and masquerading as a Firefox component (FirefoxData.dll) within the user's Documents folder.
Check Point Research
Rhadamanthys 0.7 and OCR capabilities
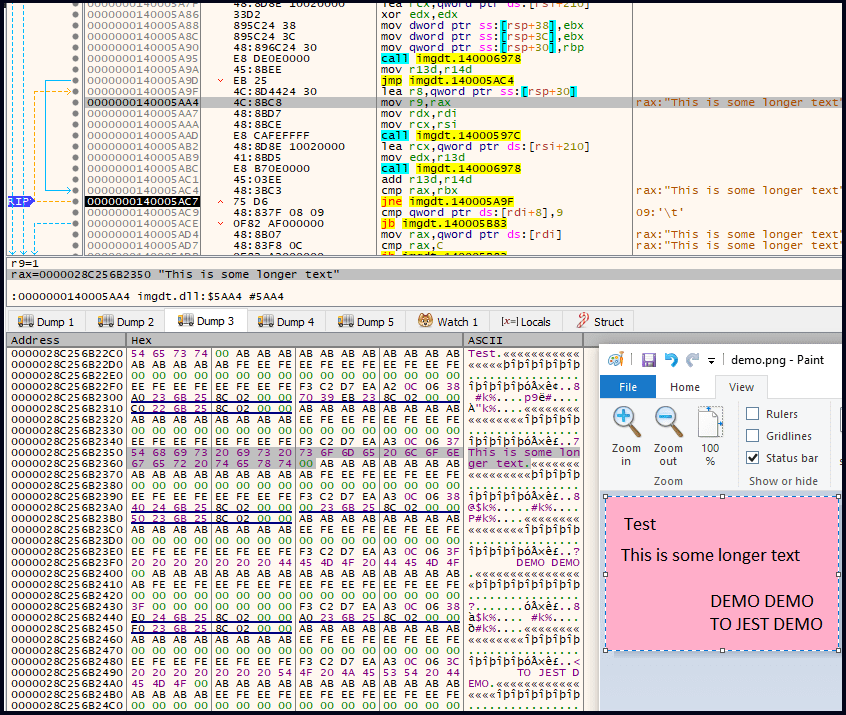
The latest Rhadamanthys version 0.7 brings updated functionality, most notably an optical character recognition (OCR) module called “ImgDat.” The malware's developer claims this component uses AI for enhanced text recognition. However, Check Point's analysis reveals that the OCR relies on outdated machine learning models, which are likely classic OCR approaches that lack modern AI capabilities.
Check Point Research
The OCR module is configured to search infected systems for specific phrases, including those related to Bitcoin wallet recovery. The malware retrieves text from popular image formats such as BMP, JPEG, and PNG, scanning for keywords that align with the Bitcoin Improvement Proposal 39 (BIP-39) wordlist.
The attackers' focus on Bitcoin recovery phrases reveals a potential interest in cryptocurrency theft, indicating a financially motivated campaign rather than state-sponsored espionage.







Leave a Reply