
GitHub, the premier platform for open-source software collaboration, faces a growing issue of fake star campaigns, which artificially inflate repository popularity metrics. A recent study conducted by researchers from Carnegie Mellon University and North Carolina State University reveals how this trend misleads developers and opens pathways for malware proliferation.
Dangers of fake GitHub stars
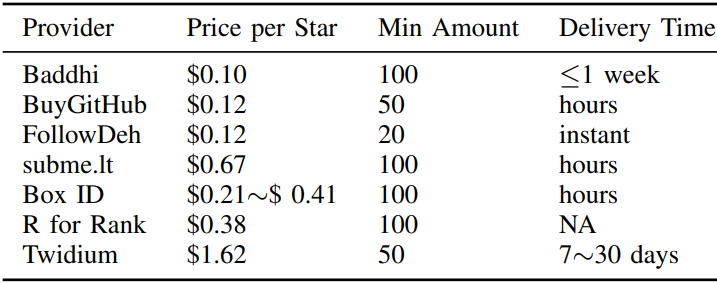
Stars on GitHub serve as a primary signal of a repository's popularity and quality. However, they can be artificially boosted via services that sell fake stars for as little as $0.10 each. These stars mislead developers and organizations into trusting projects that may harbor malicious code or lack genuine community support.
Arxiv.org
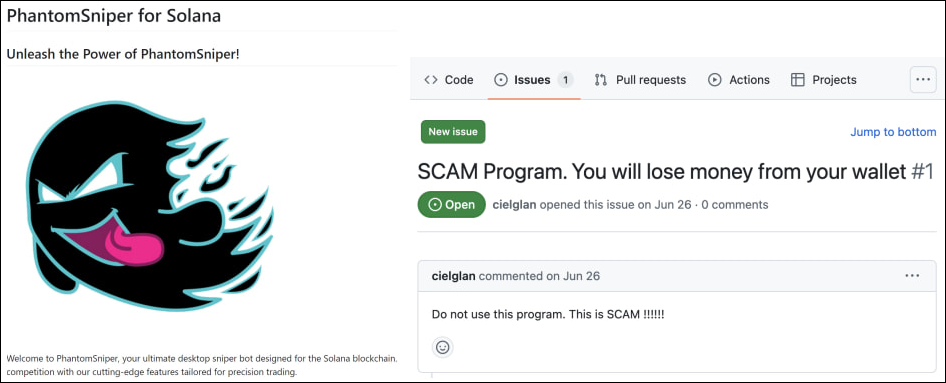
The study highlights how malicious actors use fake stars to promote repositories masquerading as useful tools like game cheats or cryptocurrency bots. These repositories often contain obfuscated malware, enabling attackers to compromise systems or steal data.
Although the practice of malicious GitHub project popularity inflation isn't new, as highlighted by a recent Check Point report looking into the Stargazers Ghost Network that industrialized this tactic, the university study showed that the problem is far more extensive than previously anticipated.
Arxiv.org
Counting stars
The researchers developed “StarScout,” a tool that detects anomalies in GitHub activity. StarScout analyzes billions of GitHub events to identify patterns indicative of fake starring campaigns, such as accounts with minimal activity other than starring repositories and groups of accounts starring repositories in a synchronized, burst-like manner.
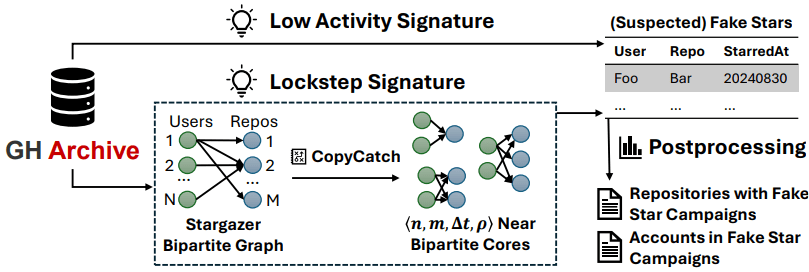
Arxiv.org
The study analyzed data from 2019 to 2024, revealing that over 4.5 million fake stars and 15,835 repositories were involved in such campaigns. Malicious repositories often saw their stars vanish after GitHub deleted fake accounts, but not before misleading users.
The study's most notable findings are summarized as follows:
- A sharp increase in fake star campaigns was observed in 2024, with nearly 16% of repositories with 50 or more stars in July 2024 being linked to such campaigns.
- Over 70% of these repositories were either phishing scams or disguised malware, highlighting a direct security risk to the software supply chain.
- While fake stars can temporarily attract real attention, their long-term impact is negative, often deterring genuine users from engaging with a repository.
Risks and mitigation
Developers and organizations often rely on star counts to evaluate software quality. This reliance can encourage the adoption of insecure software, jeopardizing organizational security and distorting the software ecosystem, making genuine projects less visible.
That being said, it is recommended that repository activity be verified beyond star counts. Look for meaningful contributions like issues, pull requests, and active discussions. Additionally, reputation metrics, such as OpenSSF Scorecards, should be considered, as they provide a holistic evaluation of software security.
GitHub is also responsible for tackling this problem. The paper suggests the implementation of weighted popularity metrics that account for account authenticity and activity diversity. Also, it is recommended that the platform enhances moderation systems to correlate fake star activity with malicious repositories for timely takedowns.
Fake stars pose a serious challenge to the software supply chain, undermining trust in GitHub's popularity metrics. By staying vigilant and leveraging detection tools, developers and organizations can mitigate the risks posed by these deceptive campaigns.







Leave a Reply