
A newly disclosed vulnerability in OpenAI's ChatGPT API allows attackers to trigger Distributed Denial-of-Service (DDoS) attacks against arbitrary websites using OpenAI's own infrastructure. The flaw enables an unauthenticated attacker to overwhelm a target website with HTTP requests originating from OpenAI's Microsoft Azure-hosted servers.
OpenAI, a leading artificial intelligence research organization, operates ChatGPT, one of the most widely used AI-powered chatbots, serving millions of users globally. Its infrastructure runs on Microsoft Azure, leveraging a large cloud-based backend to process user queries and handle API requests.
Using ChatGPT API for powerful DDoS attacks
The vulnerability was discovered earlier this month by cybersecurity researcher Benjamin Flesch, who attempted to report the issue to OpenAI and Microsoft but received no response. His findings reveal that OpenAI's API, specifically the https://chatgpt.com/backend-api/attributions endpoint, contains a fundamental design flaw that allows attackers to exploit it for reflective DDoS attacks.
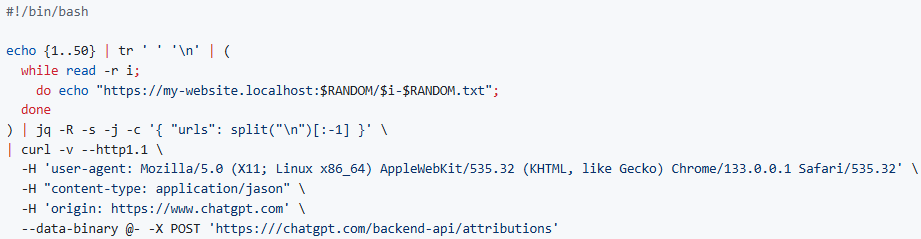
The API accepts a list of hyperlinks in the urls parameter, which is intended for attribution tracking. However, OpenAI does not validate duplicate URLs nor impose a reasonable limit on the number of hyperlinks submitted. As a result, attackers can send thousands of duplicate URLs in a single HTTP POST request. Upon processing, OpenAI's servers generate an equal number of outbound HTTP requests to those URLs—effectively launching a large-scale DDoS attack against the target website.
Flesch demonstrated the flaw with a proof-of-concept (PoC) exploit, where he submitted 50 URLs pointing to my-website.localhost. This triggered an immediate flood of GET requests from multiple Microsoft Azure IP addresses associated with OpenAI's infrastructure. Server logs from the target website confirmed a burst of simultaneous requests, indicating that OpenAI's system did not throttle or prevent excessive traffic to a single domain.
GitHub | bf
The defect creates a significant attack amplification factor and could be leveraged by malicious actors to incapacitate websites with minimal effort. Because the attack is executed from legitimate OpenAI servers, it is more difficult for traditional DDoS mitigation services to block.
After weeks of attempts through various official channels, neither OpenAI nor Microsoft acknowledged the vulnerability or took any mitigation steps.
Impact and defending
This design flaw represents a major security risk. Malicious actors could exploit it to DDoS any website or online service and bypass traditional DDoS protection mechanisms, as the traffic originates from legitimate cloud servers.
Until OpenAI addresses this risk, organizations can take the following steps to mitigate the risk:
- Rate-limit or block requests from known OpenAI Azure IP ranges using firewall rules or a web application firewall (WAF).
- Monitor and analyze incoming traffic for sudden spikes originating from OpenAI's servers.
- Work with DDoS protection providers that offer real-time filtering to detect and mitigate reflective attacks.
- Use CAPTCHA and other bot mitigation techniques to filter out automated traffic surges.







Leave a Reply