
Silent Push has revealed a substantial resurgence of the notorious FIN7 cybercrime group, identifying over 4,000 domains and IPs linked to the group's operations. The discovery highlights ongoing phishing and malware campaigns targeting high-profile organizations such as the Louvre, Meta, and Reuters.
The findings were made by Silent Push threat analysts who meticulously traced the origins and infrastructure of FIN7, known for their financially-motivated cyber attacks. The group, also referred to as Sangria Tempest, ATK32, Carbon Spider, and several other aliases, has been active since at least 2013 and was previously believed to have been dismantled by the Department of Justice.
Tracking FIN7's resurgence
Silent Push's investigation began with the detection of a suspect domain exhibiting characteristics typical of FIN7 operations. Utilizing their advanced threat hunting platform, Silent Push analysts expanded their queries to uncover linked domains across shared hosts, subsequently verifying these as active phishing and malware sites through sandbox testing and executable analysis.
The research uncovered:
- Over 4,000 FIN7 shell/phishing domains and subdomains, nearly half of which were active in the past week.
- A diverse range of high-profile targets, including technology giants like Microsoft and Google, financial institutions like American Express and Regions Bank, media outlets such as CNN and the Wall Street Journal, and even academic entities like Harvard University.
Evolving tactics
FIN7's infrastructure comprises corporate shell domains that masquerade as legitimate businesses to deploy spear-phishing campaigns. These domains often morph into phishing websites targeting users of prominent brands. For instance, miidjourney[.]net transitioned from a fake corporate fashion site to a Meta phishing page, exemplifying the group's adaptive strategies.
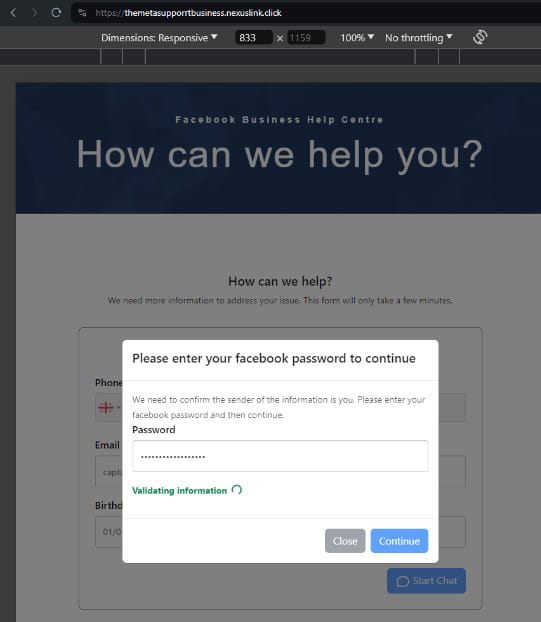
Silent Push also identified a fake cybersecurity company, cybercloudsec[.]com, used to facilitate FIN7 activities, mirroring tactics seen in earlier attacks involving fraudulent fronts like Combi Security.
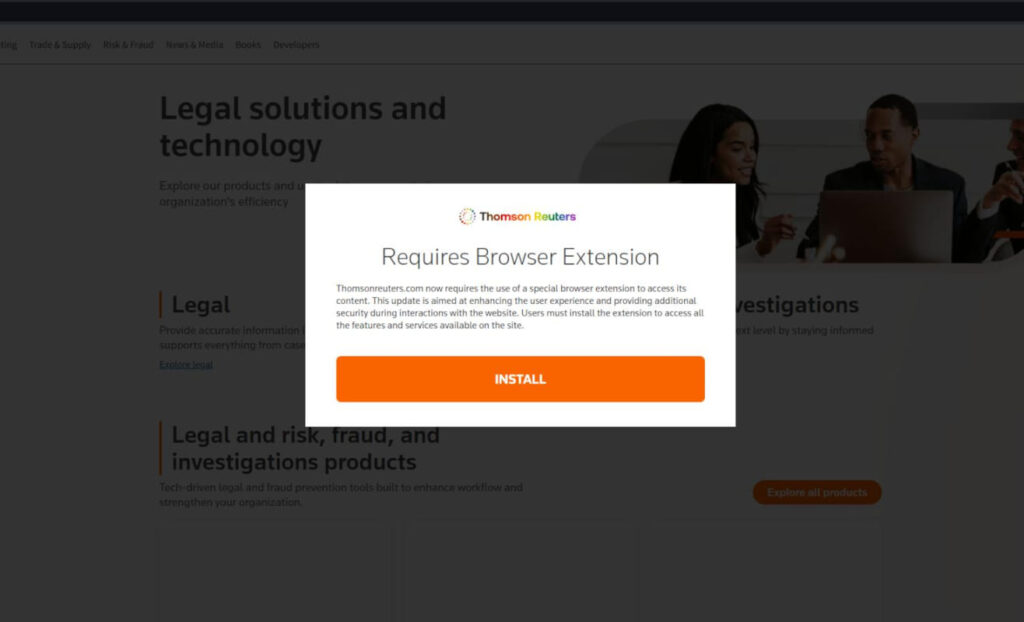
FIN7 employs sophisticated malware, including the resurgence of the “Requires Browser Extension” malware. Silent Push analysts discovered multiple MSIX files delivering malicious payloads, such as the NetSupport RAT, via spoofed pages of well-known software and services. The malware is designed to target domain-joined machines, seeking to escalate privileges and move laterally within networks to access sensitive corporate data.
Recommendations
To mitigate FIN7's activities, Silent Push recommends the following measures:
- Integrate threat intelligence feeds into security systems to block FIN7 infrastructure at the DNS level.
- Regular security awareness training should be conducted to help employees recognize phishing attempts.
- Implement multi-factor authentication (MFA) to protect sensitive accounts from credential-based attacks.
- Employ advanced endpoint protection solutions to detect and prevent malware execution.
The resurgence of FIN7 underscores the persistent and evolving threat posed by sophisticated cybercrime groups. Organizations are advised to stay vigilant and proactively enhance their cybersecurity defenses to mitigate the risks associated with these malicious actors.







Leave a Reply