
A new campaign orchestrated by the Stargazers Ghost Network is targeting Minecraft players with malicious mods that deploy multistage malware stealers.
The attack uses Java-based loaders disguised as cheat tools and relies on GitHub for distribution, evading detection by traditional security tools.
The discovery was made by Check Point Research analysts Jaromír Hořejší and Antonis Terefos, who began tracking the campaign in March 2025. The operation abuses GitHub as part of a Distribution-as-a-Service (DaaS) framework, masquerading as popular Minecraft cheat tools like Oringo and Taunahi. These tools are well-known among the modding community for automating gameplay and providing in-game advantages, which makes them attractive targets for malware impersonation.
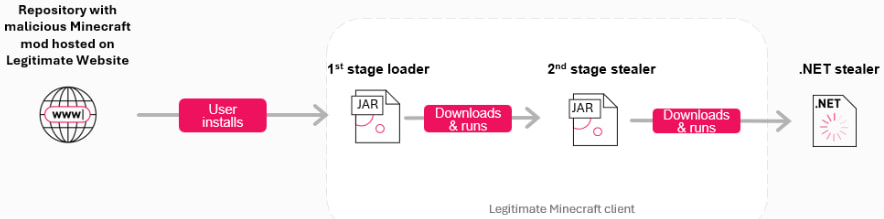
The attack chain begins with a first-stage Java-based loader embedded in a fake Minecraft mod hosted on seemingly legitimate GitHub repositories. These repositories are supported by fake “stargazer” accounts that lend artificial credibility to the files. Once the mod is installed by an unsuspecting user and the game is launched, the malware initiates a second-stage Java stealer before deploying a third-stage .NET-based stealer with broad data exfiltration capabilities.
Check Point
The mod only executes on systems where Minecraft is installed, helping it evade detection in security sandboxes that lack the Minecraft runtime. In addition, the loader employs anti-analysis techniques, terminating itself if it detects virtualization software or forensic tools such as Wireshark, TCPView, or VirtualBox services. If these checks are passed, the loader fetches a Base64-encoded payload from a Pastebin URL, which leads to the download of a Java stealer named MixinLoader-v2.4.jar.
This stealer aggressively collects authentication tokens and account credentials from various Minecraft clients, including Feather, Essential, and Lunar, as well as Discord and Telegram tokens. The data is exfiltrated via HTTP POST requests to attacker-controlled infrastructure, with endpoints embedded in Pastebin links.
In the third stage, a .NET-based stealer named “44 CALIBER” is downloaded. This payload significantly expands the malware's reach, targeting credentials stored in browsers, desktop files, cryptocurrency wallets (e.g., Electrum, Exodus, Zcash), VPN configurations (e.g., NordVPN, ProtonVPN), Steam accounts, and more. It also captures screenshots, clipboard contents, and system metadata before uploading the information to a Discord webhook.
Check Point
This campaign marks the latest evolution of the Stargazers Ghost Network, previously exposed by Check Point in July 2024. Operating as a DaaS model, Stargazers enables threat actors to distribute malware through a sprawling infrastructure of fake GitHub accounts. Past campaigns included distribution of malware families like Atlantida Stealer and GodLoader, with victims lured via phishing templates, Discord links, and fake modding tools. Stargazers' infrastructure includes thousands of GitHub accounts, frequently reconstituted to evade bans and sustain operations.
The use of Java in this campaign is particularly notable. Minecraft's modding ecosystem relies heavily on Java, yet many endpoint detection solutions fail to scrutinize Java archives effectively. This blind spot allows the malware to slip past antivirus engines.
Evidence suggests the attacker is Russian-speaking, based on embedded language artifacts and GitHub commit timestamps in the UTC+3 timezone. The same usernames and developer aliases (e.g., “JoeBidenMama”) were observed creating multiple Pastebin payloads and distributing them via repositories tied to the Stargazers Ghost Network.
Minecraft players are recommended to avoid downloading Minecraft mods from GitHub repositories with low contributor counts or suspicious activity, and use official modding platforms like CurseForge or Modrinth when installing third-party content instead.







Leave a Reply