
A new campaign redirects users from gaming sites, social media, and even sponsored ads to fake Booking.com websites designed to infect devices with the dangerous AsyncRAT malware.
First spotted by Malwarebytes in mid-May, the campaign exploits travelers searching for hotel deals, using deceptive tactics like fake CAPTCHA forms and clipboard hijacking to convince victims to run malicious commands on their own computers.
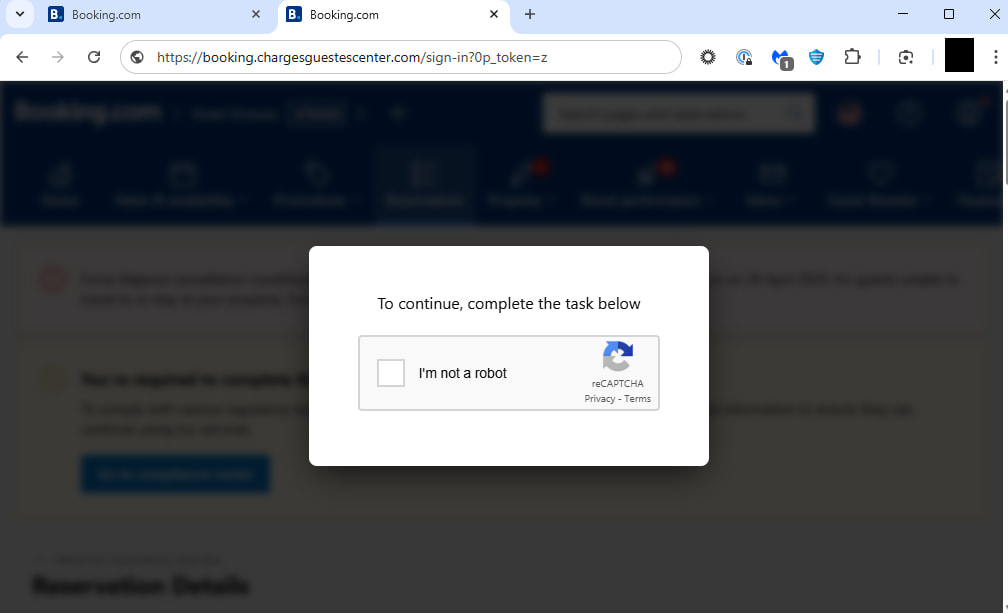
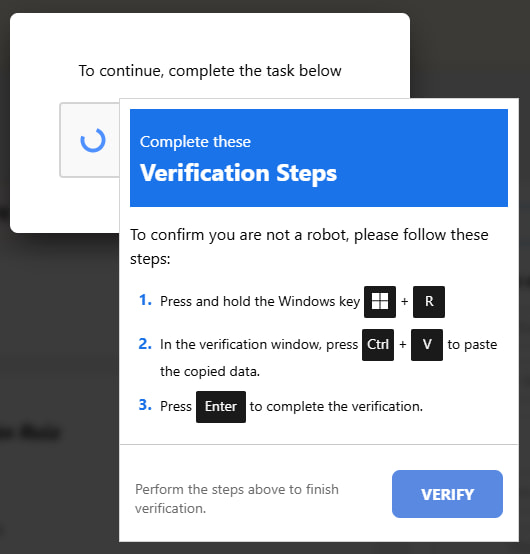
The attackers use constantly changing redirect chains, switching destination URLs every two to three days, to stay ahead of blacklists. The attack chain begins when a user clicks a malicious link, landing on a fake Booking.com page that prompts them to complete a CAPTCHA. This CAPTCHA isn't real; it secretly hijacks the user's clipboard and inserts an obfuscated PowerShell command designed to download and run further malware when pasted into the Windows Run dialog.
Malwarebytes
The PowerShell command, once cleaned of its obfuscation tricks like mixed casing and interrupted quotes, contacts a domain (bkngnet.com) to download a payload named ckjg.exe, which then fetches and executes Stub.exe. Malwarebytes' security suite detects this as Backdoor.AsyncRAT, a powerful Remote Access Tool (RAT) that allows attackers to fully monitor and control an infected system. Once installed, AsyncRAT can harvest sensitive information, including login credentials and financial data, paving the way for identity theft, fraud, or broader network compromises.
Malwarebytes
Booking.com, a global travel reservation giant with millions of users worldwide, has become an appealing target for impersonation attacks due to the sheer volume of online bookings made through general searches. Malwarebytes cites research showing that 25% of users book travel this way, often trusting the first few results they see, an opening that scammers are eager to exploit.
The infrastructure behind this campaign is fluid, with domains cycling rapidly to avoid detection. Recently active malicious domains include:
- chargesguestescenter[.]com
- badgustrewivers[.]com
- property-paids[.]com
- extranet-listing[.]com
- bkngnet[.]com (payload delivery site)
To defend against this kind of attack, Malwarebytes recommends never following unexpected Run dialog or terminal instructions from websites, using an active anti-malware solution that blocks known malicious domains and payloads, and setting your browser to block scripts.
The clipboard hijack relies on JavaScript's document.execCommand(‘copy'), which can silently copy commands for later execution. Disabling JavaScript on unknown or untrusted websites is a measure that would block this attack, though this could break site functionality in some cases.







Leave a Reply