
A bogus AnyDesk website created to look just like the authentic one is distributing a custom malware named “Mitsu Stealer”, which specializes in snatching valuable user data.
AnyDesk is a popular remote desktop application for Windows, Linux, and macOS, used by millions of users for secure remote connectivity, control, and file actions via VPN and proxies.
The fake website is most likely promoted via malspam, SMS, or posts on social networks, but it doesn’t appear to involve malvertizing at the moment.
As a report by Cyble Research and Intelligence Labs details, the campaign is of unknown origin and uncertain scale, but its creators appear diligent, with attention to detail and interest in establishing a distinct malware brand.
AnyDesk site
The fake AnyDesk website is a clone of the original, even featuring subscription tier pricing details and a space where new job openings are posted. This is to create a false sense of legitimacy and trick the visitor into believing they landed on the real site.

Source: Cyble
Clicking on the “Download Now” button delivers a file named “Anydesk.exe”, supposedly an installer for the popular remote desktop app, but in reality, it’s a copy of the Mitsu Stealer.
Upon running the downloaded executable on their systems, the unsuspecting victims are infecting themselves with a powerful information stealer.
Mitsu Stealer
Mitsu is a custom-made 64-bit malware that Cyble found is based on freely available code on GitHub. However, its author has given it a distinctive name and logo, indicating that it’s destined for MaaS (malware as a service) operations.
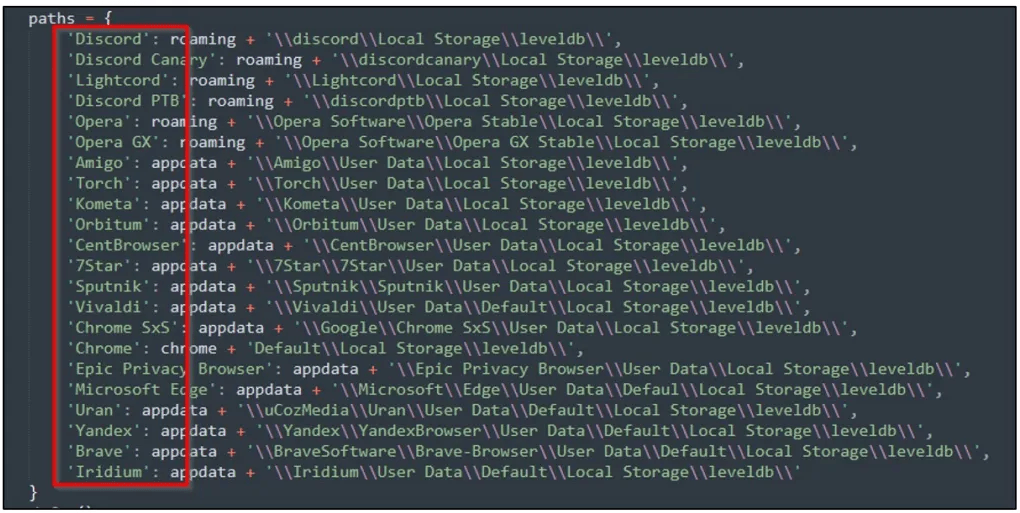
The malware abuses Discord webhooks for communications and data exfiltration, and it targets sensitive information the user has stored on Google Chrome, Microsoft Edge, Opera, and Mozilla Firefox browsers.
Source: Cyble
The information includes account credentials (usernames and passwords), credit card data, Discord tokens, and even cookies that can be used to hijack valid sessions and take control of accounts.
Additionally, Mitsu also targets an extensive collection of cryptocurrency wallets, including Binance, Coinbase, and PayPal.
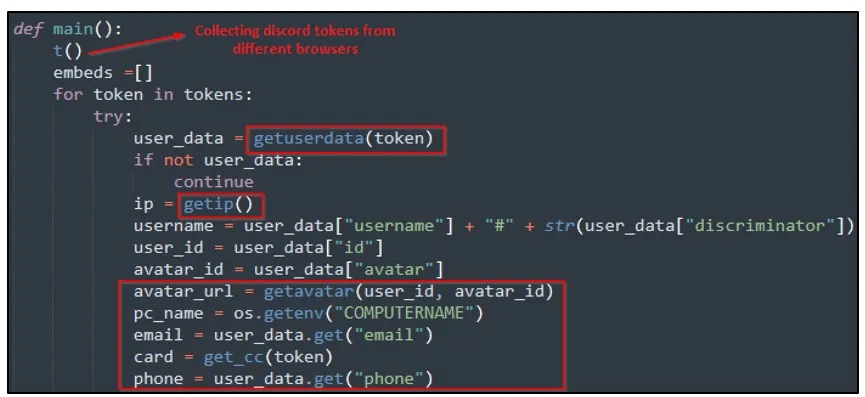
If a Discord token is available for grabs, Mitsu will use it to get user details like name, ID, and avatar, parse the badges, and steal the information saved in the platform’s payment sources section.
Source: Cyble
Finally, the local Discord app on the victim’s system is hijacked through file replacement, planting a permanent backdoor that helps the attackers further propagate the malware.
Avoid direct links
To keep threats like Mitsu Stealer away from your system, avoid clicking on links sent to you via unsolicited email, SMS, or direct messages on social media.
If you’re looking for AnyDesk or any other software, locate the official website using an internet search engine, and skip any entries marked with “Ad” that could be promoted by malvertizing campaigns.
Finally, always check downloaded files on your anti-virus tool before executing them, even if they were sourced from a seemingly trustworthy site.







This is the stuff that makes you shiver.
Thank goodness I have no idea what the AnyDesk Website is.