
ESET's Israeli partner, Comsecure, recently suffered a breach that led to a phishing campaign targeting its customers with wiper malware.
The campaign leveraged compromised email infrastructure to distribute malicious downloads under the guise of ESET's Advanced Threat Defense Team. The emails, which passed authentication checks, lured recipients with claims of state-sponsored threats, directing them to download malware disguised as legitimate security tools.
The breach was revealed earlier today through an official statement from ESET Research on X. While ESET emphasized that the incident was contained within ten minutes and did not compromise its systems, the breach affected the company's Israeli partner.
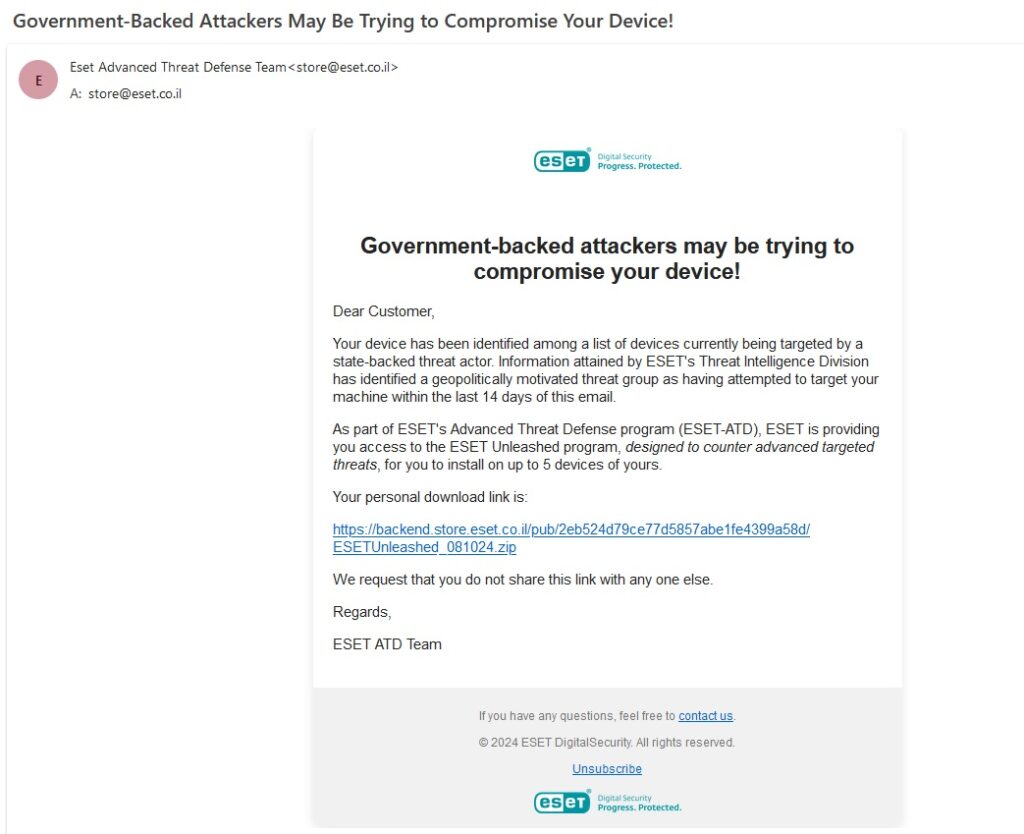
This allowed attackers to send phishing emails from legitimate-looking ESET domains, including store@eset.co.il. The emails alerted recipients that their devices had been targeted by government-backed actors and offered a download link to a supposed security tool called “ESET Unleashed.” However, this was a cover for distributing wiper malware.
Security researcher Costin Raiu, who analyzed the attack, shared details of the malware on social media. The malicious payload, identified as “EIW” (ESET Israel Wiper), was politically motivated. A message embedded in the malware warned ESET for “doing business with the occupiers.” The wiper's primary function is to irreversibly erase data, and there are no apparent recovery methods.
The phishing emails carried the subject line “Government-Backed Attackers May Be Trying to Compromise Your Device!” and were styled to appear like official communications from ESET's Advanced Threat Defense (ATD) team. These emails contained a download link to a ZIP file hosted on a subdomain of ESET Israel (backend.store.eset.co.il). Inside the ZIP file was an executable named setup.exe, which, upon execution, unleashed the wiper.
@JAMESWT_MHT | X
Kevin Beaumont, a prominent security researcher, analyzed the malware further and published his findings on his blog space. According to Beaumont, the attack specifically targeted cybersecurity professionals within Israel. The wiper also reached out to a legitimate Israeli organization, oref.org.il, as part of its execution chain, potentially as a technique to evade detection by mixing legitimate traffic with malicious behavior.
In its official statement, ESET reassured its global customer base that the breach was limited to its Israeli partner and that ESET's own systems were not compromised. The company emphasized that its technology is actively blocking the threat and that impacted customers are secure. ESET is working closely with its Israeli partner to investigate the breach further while monitoring for any additional malicious activity.
Although ESET downplayed the scale of the incident, third-party researchers like Beaumont and Raiu pointed out that the phishing emails successfully bypassed SPF and DKIM checks, making them appear legitimate. This suggests that the attackers had access to ESET Israel's mail server, raising concerns about the depth of the compromise.
Impact and recommendations
ESET Israel serves a significant number of customers, both individual users and corporate clients, across a wide range of industries. The fact that this phishing campaign targeted cybersecurity professionals is especially concerning, as these users typically hold sensitive positions within organizations that handle critical infrastructure and data.
To mitigate risks and prevent further damage, ESET customers, especially those in Israel, are advised to:
- Avoid opening any unsolicited emails claiming to be from ESET Israel or containing links to downloads, particularly if they reference ESET's ATD program.
- Verify any email communications by cross-checking with ESET directly through official channels.
- Avoid downloading unknown ZIP files or running unverified executables from links sent via email, especially if they originate from recently compromised domains.
- Run full system scans using updated security software to ensure there has been no malware infection.
- Update incident response procedures and backup strategies to prepare for potential wiper malware incidents, which can cause irreversible data loss.







Leave a Reply