
Volexity identified a sophisticated cyber-espionage campaign targeting Indian government entities, utilizing malware dubbed Disgomoji. The campaign, attributed to a Pakistan-based threat actor known as UTA0137, highlights the growing use of advanced stealth tactics in state-sponsored cyber attacks.
UTA0137 is known for its espionage objectives, particularly targeting Indian government entities. Volexity's high-confidence assessment is based on multiple factors, including the Pakistani time zone hardcoded in the malware, infrastructure links to the Pakistan-based threat actor SideCopy, and consistent targeting of Indian government organizations.
Disgomoji details
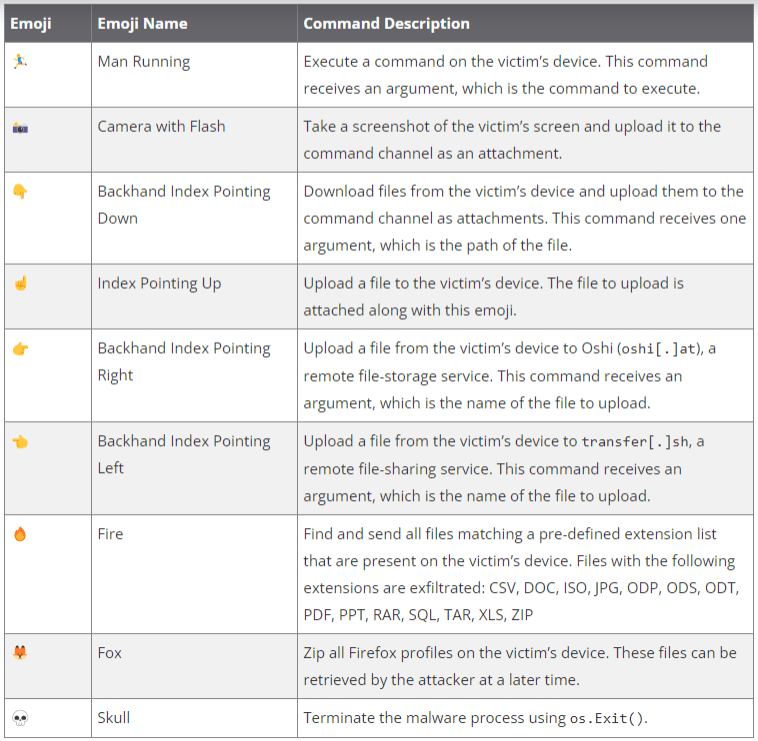
Disgomoji, written in Golang and compiled for Linux systems, is a modified version of the public project discord-c2. It uses the messaging service Discord for command and control (C2), leveraging emojis for C2 communication. This malware's unique trait is its focus on Linux systems, particularly those running the custom Indian government Linux distribution, BOSS.
The infection chain begins with a UPX-packed ELF file delivered in a ZIP archive. This ELF file downloads a benign lure document, DSOP.pdf, representing India's Defence Service Officer Provident Fund, to deceive the victim. The primary payload, Disgomoji, is then fetched from a remote server and installed in a hidden directory on the user's system.
Disgomoji maintains a robust persistence mechanism using cron jobs. It survives reboots by adding entries to the crontab and employs a script, uevent_seqnum.sh, to monitor and copy files from connected USB devices. The malware also uses an emoji-based protocol for C2 communication, reacting with emojis like “Clock” and “Check Mark Button” to indicate command processing status and completion.
The malware can execute commands, take screenshots, download and upload files, exfiltrate specific file types, and even terminate its own process. It also features a mechanism to avoid running multiple instances simultaneously and dynamically retrieves its Discord credentials from an attacker-controlled server, enhancing its resilience against disruption.
Volexity
Post-infection activity
Volexity's analysis revealed UTA0137's use of various tactics and tools post-infection. These include network scanning with Nmap, tunneling with Chisel and Ligolo, and staging and exfiltrating data using file-sharing services like oshi[.]at. Additionally, UTA0137 employs the DirtyPipe (CVE-2022-0847) privilege escalation exploit to gain root access to vulnerable systems, demonstrating their deep understanding of the targeted operating systems.
The Indian government's reliance on the BOSS Linux distribution makes this campaign particularly concerning. BOSS, or Bharat Operating System Solutions, is a custom Linux distribution used widely within Indian government departments, making it a prime target for UTA0137's campaigns.
Volexity has reported the findings to CERT at the National Informatics Centre (NIC) in India, prompting an alert and response to mitigate the impact of these attacks.
Defense recommendations
To defend against such sophisticated threats, Volexity recommends the following measures:
- Ensure all systems are updated with the latest security patches, especially for known vulnerabilities like DirtyPipe.
- Conduct regular training to help users recognize phishing attempts and suspicious activities.
- Implement advanced monitoring solutions to detect unusual activities, such as the presence of unexpected cron jobs or network traffic to unfamiliar servers.
- Restrict administrative privileges to limit the potential impact of compromised accounts.







Leave a Reply