
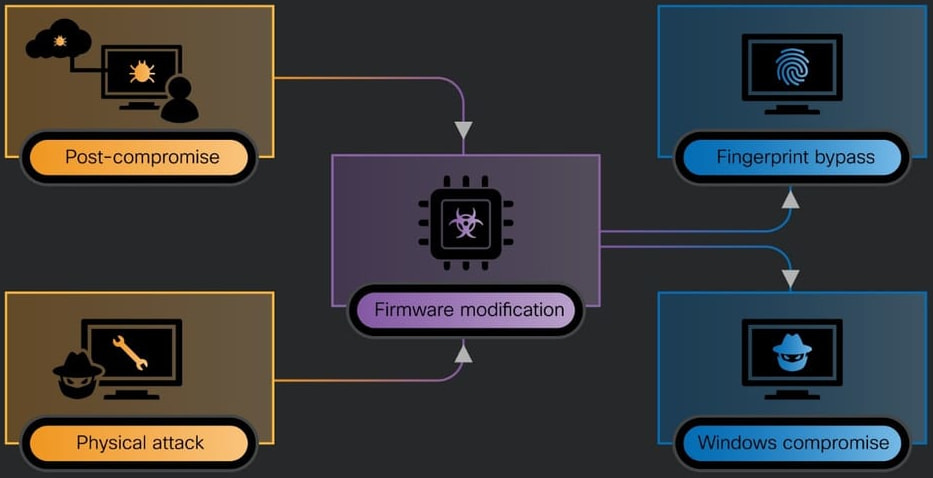
A set of five severe vulnerabilities collectively dubbed “ReVault” has been discovered in Dell’s ControlVault3 firmware and associated Windows APIs.
The flaws, affecting over 100 models of Dell Latitude and Precision laptops, enable attackers to gain persistent system-level access, even surviving operating system reinstalls, or bypass Windows login protections through physical tampering.
The vulnerabilities were discovered by Cisco Talos researchers and disclosed to Dell and Broadcom prior to public release. The Talos report details multiple exploitable bugs: two out-of-bounds vulnerabilities (CVE-2025-24311, CVE-2025-25050), a stack overflow (CVE-2025-24922), an arbitrary free (CVE-2025-25215), and an unsafe deserialization vulnerability in the Windows API layer (CVE-2025-24919). Together, these flaws create a dangerous combination of remote post-compromise persistence and local physical exploitation opportunities.
Dell’s ControlVault is a hardware-based security platform embedded in a dedicated daughterboard called the Unified Security Hub (USH). This module is used to isolate sensitive authentication operations, storing biometric templates, passwords, and security codes in secure firmware. The ControlVault3 and ControlVault3+ versions are prevalent in Dell’s Latitude and Precision laptops, particularly those deployed in high-security environments such as government, enterprise, and rugged field operations.
The first major attack scenario involves a post-compromise technique where a non-privileged Windows user can exploit the unsafe deserialization flaw to inject code into the ControlVault firmware via official APIs. Once compromised, the attacker can implant persistent code into the firmware, extract sensitive key material, and silently maintain access even after a full Windows reinstall. This makes ReVault a potent foothold for long-term espionage or backdoor access in high-value environments.
The second scenario describes a physical attack where an adversary with hands-on access to the device can interface with the USH board directly via USB. This allows firmware manipulation without login credentials or disk encryption passwords. Notably, this could enable fingerprint spoofing, reprogramming the device to accept any fingerprint for login, bypassing one of the laptop’s key biometric protections.
Cisco Talos
Compounding the severity of ReVault is the lack of standard mitigations within the firmware, leaving the vulnerabilities easier to exploit. Talos notes that unless protective features like chassis intrusion detection or Windows’ Enhanced Sign-In Security (ESS) are proactively enabled, such tampering could go unnoticed.
To mitigate the threat, Talos recommends:
- Firmware updates: Ensure the latest ControlVault firmware is installed. Updates may be available through Dell’s website before reaching Windows Update channels.
- Disable unused features: If fingerprint, smart card, or NFC authentication is unused, disable ControlVault via Windows Device or Service Manager.
- Harden access controls: Avoid leaving laptops unattended in unsecured environments and consider disabling biometric login when risk is elevated.
- Chassis intrusion detection: Enable this in BIOS if supported by your model to detect hardware tampering.
- Log monitoring: Watch for abnormal crashes in biometric services or suspicious activity involving bcmbipdll.dll.
Dell has not issued a public advisory at the time of writing, though firmware packages and driver updates for ControlVault are typically available through Dell SupportAssist or directly from the support site. The update process includes a driver package that contains firmware, biometric, and smart card drivers.






Leave a Reply