
A joint operation between the Royal Thai Police and the Singapore Police Force, supported by cybersecurity firm Group-IB, has led to the arrest of a notorious cybercriminal responsible for more than 90 data leaks worldwide.
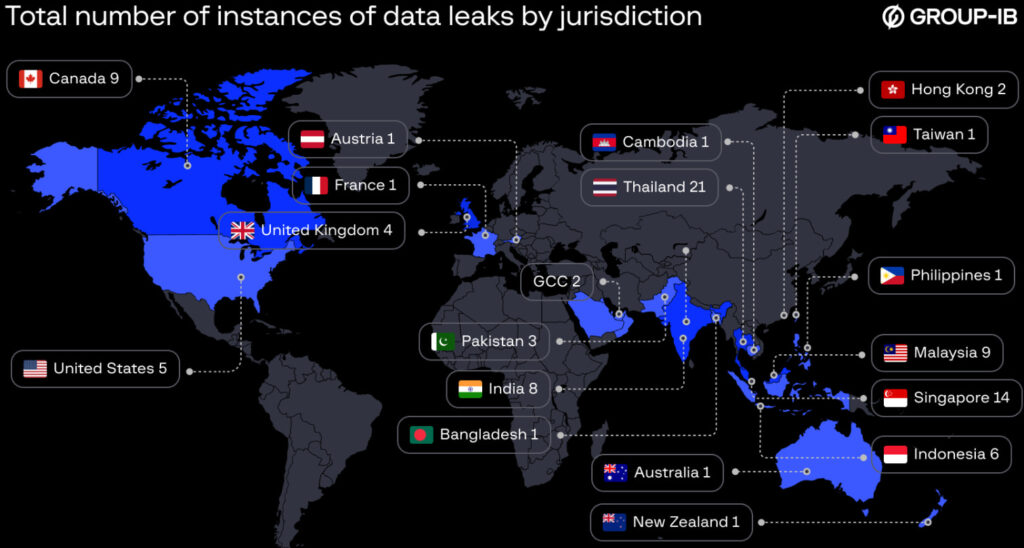
Identified as a 39-year-old Singaporean man named Chia, the suspect operated under multiple aliases, including ALTDOS, DESORDEN, GHOSTR, and 0mid16B, and had been actively targeting companies across Asia-Pacific, North America, the Middle East, and Europe since 2020. His cyberattacks led to the exposure and sale of over 13TB of sensitive personal and corporate data on dark web forums.
Group-IB
Four-year investigation
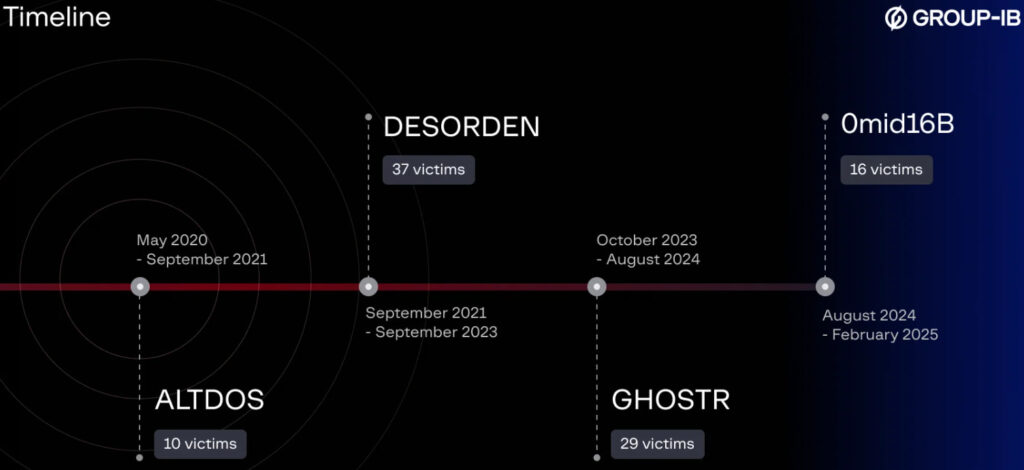
Group-IB's Threat Intelligence and High-Tech Crime Investigation teams, operating from their Digital Crime Resistance Centers (DCRCs) in Thailand and Singapore, had been tracking the suspect since 2020. He initially emerged under the alias ALTDOS, primarily attacking companies in Thailand before expanding his reach. His modus operandi involved hacking into corporate databases, stealing sensitive data, and demanding ransoms. If victims refused to pay, he notified media outlets or data protection regulators instead of leaking the data on the dark web, thereby intensifying reputational damage for his targets.
Over time, the suspect evolved his tactics, adopting new aliases to avoid detection. Under DESORDEN, he gained notoriety for targeting companies in healthcare, finance, e-commerce, logistics, and retail sectors across multiple countries, including Singapore, Malaysia, Indonesia, India, and Thailand. Later, operating as GHOSTR and 0mid16B, he extended his cybercriminal activities to the United Kingdom, the Middle East, Canada, and the United States.
Group-IB
Authorities confirmed that he used SQL injection tools like sqlmap and exploited vulnerable Remote Desktop Protocol (RDP) servers to gain unauthorized access. Once inside, he deployed a cracked version of Cobalt Strike to maintain control over compromised systems. Unlike many ransomware operators, he rarely engaged in lateral movement within breached networks, instead immediately exfiltrating data to rented cloud servers for blackmail purposes.
Arrest and seizure
Thai authorities, led by Pol Col Panupat Kittipan, commander of the Technology Crime Suppression Subdivision 1, tracked Chia's location to a residence in Bangkok's Gusto Grand Ramkhamhaeng housing estate. Acting on a search warrant, law enforcement raided the property, seizing laptops, storage devices, and luxury goods worth an estimated 10 million baht ($280,000), allegedly purchased with profits from his cybercrime activities.

Group-IB
Investigators revealed that Chia used X (formerly Twitter) accounts linked to Omid16B Group to post ransom demands. He allegedly intimidated victims by directly contacting their customers through email and messaging platforms, warning them about leaked data to increase pressure on businesses. He later admitted to hacking over 70 companies, including 20 in Thailand. Among his known Thai victims was Black Canyon, a prominent coffee shop chain, whose systems were compromised in late 2024.
The suspect faces multiple cybercrime-related charges, including:
- Unauthorized access to protected computer systems and data
- Attempted extortion
- Illegal residence in Thailand
Given the transnational nature of his crimes, authorities in Singapore and other affected countries may seek his extradition for further prosecution.







Leave a Reply