
Last year we published a guide that highlighted the most alarming cybersecurity statistics and trends unfolding at that time. But things move fast in the tech world, and cybersecurity is a high-threat war with billions of dollars at stake. It is time to take another look at the battleground as of today.
The world is even more dependent on technology and the Internet as it was the last time we looked at this subject. Combine this with increased international tensions, even larger databases (government and private) just waiting to be targeted, and more bad guys with experience and resources.
The result is an impending cybersecurity disaster.
To understand the important factors and cybersecurity trends for 2020, we'll begin by discussing data breaches.
Large-scale data breaches are increasingly common

Since the last Restore Privacy report on this subject, there have been several king-sized data breaches reported, including:
- Capital One, where the hacker or hackers got their hands on over 100 million credit card related records. They used the information to access around 80,000 bank accounts, as well as huge quantities of additional personal information. In response to this “cyber incident,” the company provided affected individuals with free credit monitoring and identity protection services. (We also have a guide on identity theft and fraud.)
- Adobe discovered a massive breach in their Creative Cloud suite. The data for over 7 million users was exposed.
- DoorDash discovered that someone had breached their system and gotten access to the data for approximately 4.9 million people.
The average cost of data breaches keeps growing, too. A 2018 report by IBM showed a global average cost of a data breach as $3.86 million dollars. The 2019 report lists a global average cost of $3.92 million per breach.
And despite the best efforts of an army of engineers, technicians, and scientists, dangerous vulnerabilities continue to be discovered, even in “ancient” systems like Bluetooth that have been in use for decades. Don't believe me? Check out this article from The Hacker News.
It discusses SweynTooth, a set of a dozen potentially severe vulnerabilities affecting millions of Bluetooth-equipped devices. The vulnerabilities could allow hackers to disable devices or even read user data from them. Reportedly, at least 480 distinct products are affected by the problems.
With this as background, let's look in a bit more detail at some of the biggest cybersecurity problem areas right now.
Phishing attacks are the dominant attack vector for cybercriminals
For years now, the dominant attack vector for cybercriminals has been email. Specifically the various types of phishing attack (phishing, spearfishing, whaling, clone phishing).
The number of phishing attacks apparently started dropping between 2017 and 2018 – but the sophistication of the attacks, and their potency seems to be growing. Two increasingly popular message types are fake browser updates and activist-targeted messages.
According to a January report by Proofpoint, nearly 90% of organizations internationally experienced targeted phishing attacks in 2019. The report also highlighted that many employees fail to apply basic security techniques, in particular reusing passwords, and using their business devices for personal purposes, often on their unprotected home networks.
Fortunately, there is a silver lining to the dark cloud of phishing attacks. Because they have been going on for so long, people have developed useful guidelines to defend against them. The simple steps we list below, if followed by everyone in the organization, should go far toward eliminating the damage these kinds of attacks can cause. When working with your email:
- Never open attachments you weren't expecting to receive. Attackers can embed malware in these attachments, potentially giving them control over your device. If in doubt, you can also scan attachments using VirusTotal before opening.
- Avoid clicking links in email messages. A link in a phishing message may look legitimate, but could lead you to a website that will try to trick you into giving up personal information, or will try to inject malware into your system. Hover the mouse pointer over the link to see where it goes. Assuming it points to a legitimate destination, you can manually type the address into the browser yourself.
- Legitimate organizations will never ask you to send them your username and password. If a message asks for those, you can be sure it is a phishing attempt.
When the bad guys send phishing messages that try to get malicious software onto your system, one of their favorite payloads is ransomware…
Ransomware is bigger and badder than ever
As we pointed out last time around, ransomware is a huge and growing problem.
Individuals and businesses have always been ransomware targets. Last year, the creeps who send this stuff started hitting bigger targets as well. Dozens of cities became targets, contributing much of the estimated $11 billion that ransomware attacks cost the world last year.
This focus on bigger targets may help explain why Coveware recently reported this terrifying bit of news:
In Q4 of 2019, the average ransom payment increased by 104% to $84,116, up from $41,198 in Q3 of 2019. While the median ransomware payment in Q4 was $41,179, the doubling of the average reflects diversity of the threat actors that are actively attacking companies. Some variants such as Ryuk and Sodinokibi have moved into the large enterprise space and are focusing their attacks on large companies where they can attempt to extort the organization for a seven-figure payout…
The analysts at BeyondTrust suggest that ransomware crooks might move onto even bigger targets, including local and national infrastructure. Unfortunately, it appears this prediction from last year was spot on.
Early in February 2020, a ransomware attack took out the control and communication assets on the operational technology (OT) network of a natural gas compression facility. According to authorities at the United States Cybersecurity and Infrastructure Security Agency (CISA), the attackers were unable to gain control of the operational systems. However, they were able to prevent the facility from reading real-time data needed to continue operations, forcing them to shut down for two days.
The fact that the attackers were able to force the facility to shut down is disturbing, but not the worst of it. According to the CISA alert, the software used by the attackers was commodity ransomware. In other words, it wasn't some incredible hack job by geniuses in some secret lab somewhere. The deed was done with standard software delivered by a spearfishing email message.
I\'m not sure what they call this particular type of software. But according to this Technology Review story, one such ransomware program is named EKANS.
Note: There have also been non-ransomware attacks on US infrastructure. In September of last year we learned details of a March attack on an undisclosed electric utility in the Western part of the United States. The attacker exploited a known vulnerability in firewall software to cause intermittent denial of service (DoS) type shutdowns of communication for various devices. This was reportedly the first time a remote hacker successfully interfered with the US power grid.
Protecting global supply chains is a top priority
At this writing, it is unclear whether the current coronavirus (a.k.a. COVID-19) will turn into a major pandemic or will somehow be brought under control before it is too late. One thing that the virus has made clear, however, is that world economies are highly dependent upon their global supply chains. Companies around the world are already shutting down production as they run out of parts that are sourced from China.
But the physical function of global supply chains isn\'t the only risk. Global supply chains are a huge cybersecurity risk as well. So much so that later this year companies looking to secure contracts with the US Department of Defense will need to obtain Cybersecurity Maturity Model Certification (CMMC) to prove that their cybersecurity meets federal requirements.
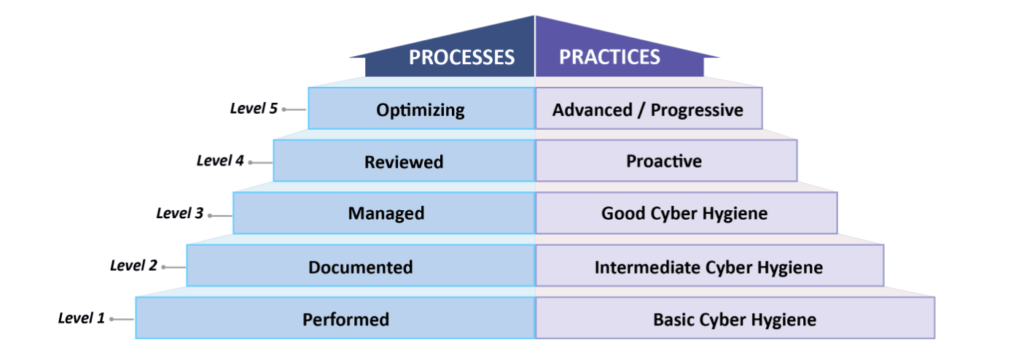
Source: Cybersecurity Maturity Model Certification, Version 1.0
Delays and disruptions can easily result in millions of dollars in costs. With the just-in-time nature of global logistics, the stakes remain very high.
Biometric database attacks present frightening possibilities
Governments and private companies are in love with biometric identity systems. Fingerprints, voiceprints, and especially facial recognition systems are showing up everywhere. Leaving aside the “Big Brother” implications of ubiquitous machine surveillance, there is another problem that gives me nightmares.
What happens when cyberattackers crack the databases that hold our biometric data?
When some creep hacks a traditional database and gets my username and password, changing them is a headache. But what will we do when bad guys get their hands on our biometric data?
It's not like you can just change your voice and fingerprints and face every time your data is exposed. Don't think it can't happen to you? The UK has already had the Suprema disaster, and so has India's Aadhaar system. Hopefully someone will put some limits on these kinds of systems before hackers can gain the biometric data for most of humanity.
The AIs are increasingly manning the front lines
The use of automation to protect systems from cyber attacks has been growing for a few years now. The 2020 edition of Staffing the IT Security Function in the Age of Automation noted that,
The majority of companies (77 percent) continue to use or plan to use automation in the next three years. The biggest takeaway in this year’s study is that the majority of respondents (51 percent) now believe that automation will decrease headcount in the IT security function, an increase from 30 percent in last year’s study.
The use of automated tools will surely help. But that's not what we're talking about here.
Numerous resources advise that both attackers and defenders will be using Artificial Intelligence (AI) systems to give them an edge in the cybersecurity war. While we aren't likely to see T-800 (or any other flavor) Terminators assaulting corporate IT departments any time soon, the online systems that could be deployed any time now are scary enough.

Perhaps you are wondering how this technology could be used against regular people like you and me…
AIs on the attack
AIs manning the defenses
When it comes to defending our systems against attack, AI systems have great potential. One of the most important ways to ensure that a system is secure is to bring in a third-party penetration testing (pentest) company to probe your system for vulnerabilities. While pentesting is highly effective, it requires skilled and experienced penetration testers to get the job done. There is currently a growing shortage of people who are qualified to do this work.
Interestingly, the work done by penetration testers is very similar to the work done by the attackers they are trying to stop. Only the goal is different. So it shouldn't be a surprise that people are working on AI penetration testing systems. As Javier Avila, a cybersecurity analyst for AGS Alpama Global Services, explains in this article at RiskSense,
Standard penetration tests consist of seven phases. AI and ML can assist in vulnerability analysis and exploitation by extracting information from services running on target systems.
While AI is unlikely to completely replace humans in the pentest space, it is highly likely that these intelligent systems will soon be helping boost the security of critical networks and infrastructure.
The Internet of Things remains an open door for cyberattacks
As noted last time, the Internet of Things is expanding at an incredible rate – and this comes with risks.
For example, in a report for the healthcare industry, MarketsandMarkets Research predicted that the size of the Global IoT healthcare market will expand at a compound annual growth rate of 27.6% from 2019 through 2024. That translates to the value of IoT devices just in healthcare growing from $55.5 billion in 2019, to $188.0 billion in 2024.
I have no idea how many discrete IoT healthcare devices that translates to. Opening up the field a bit, I'm seeing estimates of between 41.6 and 64 billion IoT devices that are expected to be deployed worldwide by 2025. This includes everything from the latest 5G smartphones, to Internet-connected household appliances, to your kid\'s toys. What are the chances that this vast horde of IoT devices will make it to market in the next few years without its fair share of exploitable vulnerabilities? I would guess about zero.
Remember that the internet-connected portion of IoT devices is usually low-powered and slow, with few resources available for “secondary” features like cybersecurity. Even worse, large multinational companies that make “smart” appliances, for example, will surely fall behind with firmware and security updates. Keeping an ever-growing assortment of devices updated and secure is basically an impossible task, particularly as older models are phased out.
With every “smart” device being a potential vector to attack and exploit your network, this puts you at serious risk.
IoT devices will continue to be a cybersecurity nightmare for the foreseeable future, especially with the continual expansion of “smart” devices in all facets of our lives.
The possibility of more cyberattacks aimed at destroying your business
Last year we talked about cyberattacks that aimed not to steal data, but to destroy it. While the cost of recovering from a cyberattack may be enough to drive a business under, that isn't the primary goal of most attacks. However, this year we may see a large increase in the number of attacks specifically aiming to damage or destroy businesses through the destruction of their data.
The likelihood of being a target of such an attack jumped after the United States killed Iranian Quds Force commander Qasem Soleimani. Iran vowed revenge for the attack, and many expect that they will retaliate through targeted cyberattacks, as they have done in the past.
The threat is serious enough that CISA, the Cybersecurity and Infrastructure Security Agency, has published an alert warning of the possibility of cyber retaliation, and includes a list of actions an organization can take to mitigate the risk.
To get a better sense of what could happen, and whether your particular business is likely to be a target, check out this interview with cybersecurity consultant, Mark Rasch, or this Forbes article by Wayne Rash.
Public WiFi networks are at risk; your home WiFi is too
Our last report talked about how dangerous public WiFi can be, thanks to the ease with which hackers can break into them. The report also discussed how cyberattackers were looking for bigger targets by hacking into hotel WiFi networks. The bad guys also like to set up “Evil Twins.” That is, they set up an access point that is designed to trick you into logging into that instead of the hotel or coffee shop's router. Once your device is connected to the fake router, the hacker will be able to read any unencrypted communication between your device and the Internet at large.
While awareness of these issues has grown, the core problems have not gone away. If anything, they have grown.
But you shouldn't feel smug if you avoid public WiFi and only connect using your home WiFi router. There are lots of ways to hack into home WiFi networks. Many home routers are still using the original password set at the factory. The old WEP encryption that many home routers were installed with is now easy to crack. The MAC address filtering that you can enable on your home router is vulnerable to any self-respecting hacker with a wireless packet sniffer.
Beyond these basics, there are lots of other tricks. So many in fact that you can take courses on WiFi Hacking!
Any WiFi access point is at risk in these hazardous times. There are also cases where hackers will check into hotels to attack the network and guests staying there. This is also a growing issue at cafes and airports.
Once again, let us stress the value of using a VPN, all the time, on all your devices. VPNs are critical tools for securing your traffic when using public WiFi. All traffic will remain encrypted between your device and the VPN server, further protecting you on questionable networks. See our guide on the best VPN services for 2020 to get started.
And while it may be a hassle, using a wired ethernet connection and completely ditching wireless is a very smart idea – for both security and speed. (And also check out our guide on Controlling Communication Channels.)
Key takeaways and solutions for staying safe in 2020
That\'s enough of the gloom and doom of cybersecurity. Fortunately, there's a lot you can do to stay safe. I'll assume you aren't ready to ditch all your electronics and move to a remote wilderness cabin, so let's finish this up by talking about what you can do to mitigate risks in your personal and professional life.
1. Be smart and vigilant when dealing with email.
First and foremost, don't click links or open attachments in strange messages. Don't respond to any messages that ask you to log into your account to resolve a problem or send personal information to some anonymous tech support guy. And for heaven's sake, don't reply to that Nigerian prince who needs your help moving money out of his country!
Our Secure Email guide discusses providers that do well with both privacy and security. Many of them incorporate security features that go above and beyond your average email service.
2. Update all your devices.
And keep them up to date with the latest software and security patches. Anything that connects to the Internet has vulnerabilities that are regularly being identified and patched. As annoying as it may be, you'll want to double check to see whether updates are installed automatically or whether you need to do it manually.
4. Limit vulnerabilities.
Since anything that connects to the Internet is a cyberattack target, think long and hard before you connect more stuff. Do you really need a home coffee maker you can turn on from the office? What about one of those popular “assistants” that listens to every sound in your kitchen (or heaven forbid your bedroom) and sends who knows what back to the corporate mothership 24/7? For that matter, do you really need all 5 of your computers powered up and connected to the Internet at all times?
Take a security tip from the cryptocurrency community and only have things powered up and connected to the Net when you need them to be. It doesn't matter how good a hacker is; you can't exploit a vulnerability in a device that is powered down and disconnected from the Internet.
5. Limit WiFi use.
Wireless connectivity is wonderful. Few of us could do without it these days. But wireless connections are easier targets for cyberattacks than wired ones. That's one reason I've gone back to a wired (ethernet) connection. It is much more secure than WiFi, and faster too.
6. Consider replacing old tech.
Today, it seems most people are quick to replace their phones and computers when the next model arrives. But some of us still hang on to older stuff as long as it works. (How many people do you know who are still running Windows 7?). The problem with this is that a day comes when the manufacturer declares the old product obsolete (like Windows 7) and stops supporting it. At this point, your old tech becomes a security risk. If a new vulnerability gets discovered, there is no one to patch it, thus giving attackers a permanently open door.
Consider replacing obsolete tech before some creepy hacker or AI Hackbot uses it to penetrate your defenses.
7. Install a good antivirus / antimalware product.
Make sure you choose one that also respects your privacy. While none of these products can protect against 100% of possible attacks, they can certainly help mitigate risk.
8. Use a VPN for more security and privacy.
A good VPN will encrypt and secure your internet connection on the devices you use. It will also hide your IP address and location, greatly increasing your online privacy. I strongly recommend that you install VPN software on all your computers, smartphones, and tablets, since any one of them can be targeted in a cyberattack. Our guide on the best VPN services for 2020 highlights the best options, with ExpressVPN being our current favorite (and check out this 49% discount coupon).
A VPN is a crucial tool if you want to really be anonymous online, although there are many other precautions to take as well.
9. Use strong passwords.
Using a unique, strong password for each device and application makes life infinitely more difficult for cyberattackers. This also makes it virtually impossible to remember your passwords. The answer is to use a reliable and secure password manager to do the remembering for you. My current favorite is Bitwarden. It is a free and open source password manager, that includes secure extensions for most popular browsers.
10. Limit the data you share!
Given the growing trend of data breaches and the fact that companies are working hard to collect more of your data (for marketing and ads), the safest solution is to limit the data you share with third parties. Large corporate databases will continue to be hacked, which you cannot control. But you can limit the amount of data you share or use various personas online (see How to Really Be Anonymous Online).
This site is all about protecting your personal data and providing you with the tools and solutions you need – and there are many facets to this issue:
- Using a secure and private browser that doesn\'t collect every website you visit for targeted ads.
- A private and secure email that uses strong encryption while also keeping ads out of your inbox.
- Private search engines that don\'t collect your data for advertisers.
- Ad blockers that block tracking and ads that monitor your online browsing habits.
- The Google Alternatives guide is also a good overview to get you going in the right direction.
And of course, our main homepage has direct links to many of our other guides and resources to get you up to speed for 2020 and beyond.
That’s all for this cybersecurity trends report. Stay safe and secure in 2020!







Leave a Reply