
Cybersecurity researchers discovered severe vulnerabilities in Kia vehicles, enabling attackers to remotely control vital car functions using just the license plate information.
The flaws also exposed personal details of the car owner and allowed malicious actors to add themselves as a hidden user on the vehicle, all in under 30 seconds. While these vulnerabilities have been remediated by Kia and were most likely never exploited maliciously, they underscore the potential dangers in modern vehicle connectivity.
Discovery and exploitation
The vulnerabilities were uncovered by a group of researchers, including Neiko Rivera, Sam Curry, Justin Rhinehart, and Ian Carroll. Their investigation initially focused on Kia’s “owners.kia.com” website and the “Kia Connect” iOS app (com.myuvo.link). These applications have internet-to-vehicle commands that could execute remote functions like unlocking the car, starting it, and locating it. The Kia owners’ website utilized a backend reverse proxy to execute these commands, while the app communicated directly with the same API.
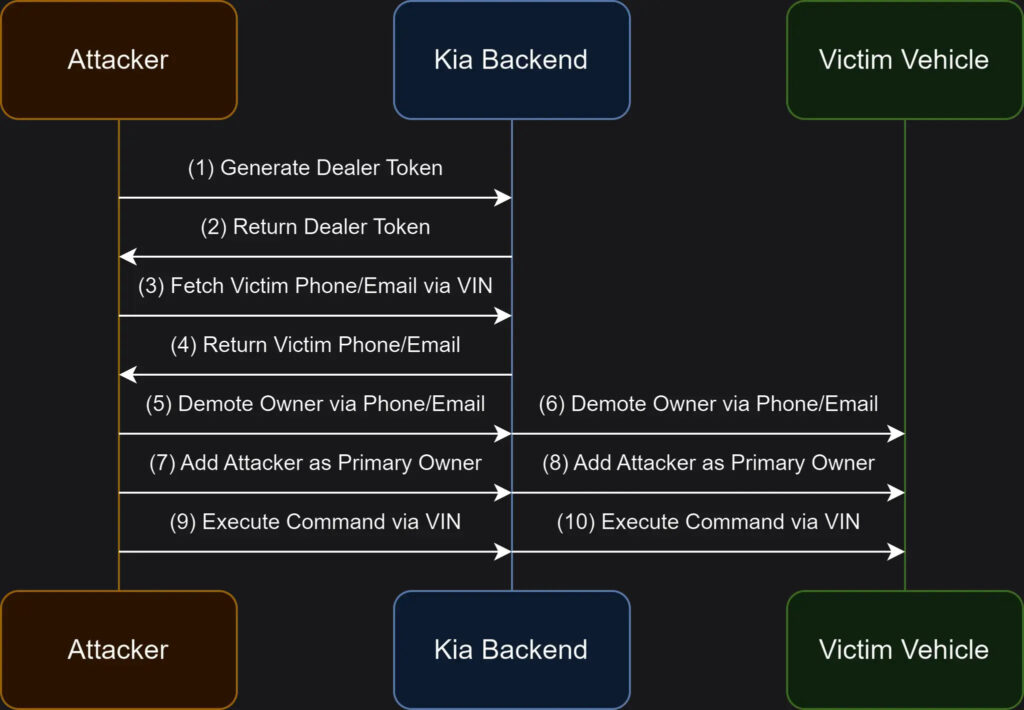
During their testing, the researchers uncovered an alarming exploitation pathway through Kia’s dealer infrastructure, particularly the domain “kiaconnect.kdealer.com.” They were able to register as a “dealer” account, generate an access token, and gain access to backend dealer APIs. With this access, they could retrieve sensitive owner details like name, email address, phone number, and physical address by simply knowing the vehicle's license plate and converting it to its Vehicle Identification Number (VIN).

The researchers developed a proof-of-concept tool to demonstrate how quickly and effortlessly the vulnerabilities could be exploited. By entering a Kia’s license plate into this tool, they could issue commands to the vehicle within 30 seconds. Although this tool was never released publicly, the demonstration showed how an attacker could remotely unlock/lock, start/stop, and even locate the vehicle.

The following sequence allowed full control over a target vehicle:
- The attacker registers as a “dealer” on the Kia platform to receive a session token.
- Using the VIN (derived from the license plate), the attacker retrieves the victim’s name, email, and phone number via dealer-specific API calls.
- The attacker uses the victim’s email and VIN to demote the original owner's access permissions on the vehicle.
- Finally, the attacker adds their own account as the primary user of the vehicle, granting them full access to send commands remotely.
samcurry.net
From the victim's perspective, no alerts or notifications were sent to indicate that their vehicle had been compromised or that an additional user had been added.
Affected Kia models
The vulnerabilities impacted a wide range of Kia vehicles manufactured between 2014 and 2025. Models from the Carnival, K5, Seltos, Sorento, Soul, Sportage, EV6, and Telluride series were affected. Some vehicles also had more advanced vulnerabilities, such as access to remote camera feeds. The vulnerability details included the ability to:
- Geolocate the vehicle
- Remotely lock/unlock
- Remotely start/stop the engine
- Trigger the horn or lights
- Access the remote camera in certain models
Most of these vulnerabilities applied to both regular models and hybrids, covering nearly the entire Kia vehicle lineup.
Kia’s response and remediation
The vulnerability was reported to Kia on June 11, 2024, after an initial inquiry sent on June 7, 2024. The researchers emphasized the criticality of the flaw multiple times in follow-up communications. Kia confirmed they were investigating by June 14 and continued to work on resolving the issue throughout the summer. By August 14, Kia indicated that the vulnerabilities were remediated and being tested. On September 26, 2024, the research team publicly disclosed the issue, ensuring that it had been fully addressed before threat actors had the chance to leverage it.
While Kia has patched the vulnerabilities, vehicle owners and manufacturers can take the following proactive measures to safeguard against similar risks:
Always keep your vehicle’s software up to date to benefit from the latest security patches.
Use strong, unique passwords for any vehicle-related applications or dealer accounts, and regularly review any linked accounts or users.
Be vigilant for unusual alerts or behavior from your vehicle, such as unexplained remote access attempts.







Leave a Reply