
A high-severity vulnerability (CVE-2024-39717) in Versa Director, a key component of Versa Networks' SD-WAN solutions, has been actively exploited by the Chinese state-sponsored threat group Volt Typhoon.
The flaw, which allows for the dangerous upload of malicious files disguised as .png images, has impacted multiple managed service providers (MSPs) and internet service providers (ISPs) since mid-June 2024, with at least five known victims.
The vulnerability in Versa Director was first identified by Black Lotus Labs, the threat intelligence unit of Lumen Technologies, who discovered ongoing exploitation in early August 2024. Versa Director servers, crucial for managing network configurations and security for clients, became a prime target due to their strategic importance in managing large-scale IT infrastructures.
Attackers gained initial access through exposed management ports, exploiting the flaw to deploy a custom web shell, named “VersaMem,” designed to harvest credentials and run additional malicious Java code directly in memory.
Technical breakdown
The vulnerability stems from the “Change Favicon” feature within Versa Director's GUI, where administrators with specific privileges could upload .png files. This feature was exploited by threat actors to upload files with a .png extension that contained malicious Java code. Once uploaded, the attackers could inject this code into the Apache Tomcat web server process running on the Versa Director, enabling them to execute further attacks while avoiding detection.
The custom web shell, VersaMem, operates by hooking into the Versa Director's authentication system to intercept and encrypt plaintext credentials, storing them in a hidden file on the server. Additionally, it hooks into the web server's request processing functions, allowing the attackers to execute arbitrary code in-memory, further obscuring their activities from traditional file-based detection methods.
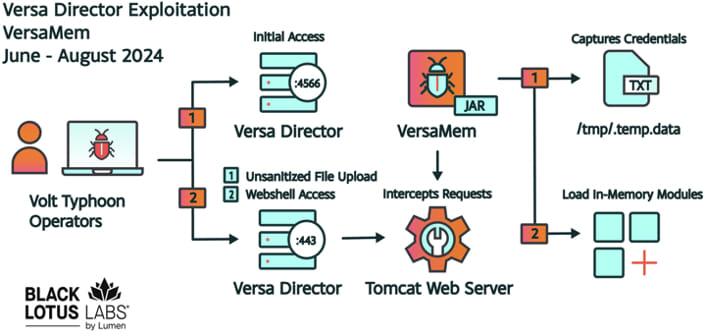
Black Lotus Labs
Impact and attribution
The exploitation campaign primarily targeted U.S.-based ISPs and MSPs, with some international victims. Black Lotus Labs linked the campaign with moderate confidence to Volt Typhoon, a well-known Chinese APT group, using compromised small-office/home-office (SOHO) devices to gain initial access to vulnerable Versa Director servers.
Volt Typhoon has a history of targeting critical infrastructure, and this campaign aligns with their known tactics, techniques, and procedures (TTPs), including the use of sophisticated in-memory malware and credential theft for lateral movement within networks.
Response and mitigation
Versa Networks has since released patches for affected versions of Versa Director (21.2.3, 22.1.2, and 22.1.3) and strongly recommends customers upgrade to version 22.1.4 or later. The company has also emphasized the importance of implementing their long-standing system hardening and firewall guidelines, which many impacted customers had neglected, resulting in their systems' vulnerability.
Customers are advised to:
- Immediate upgrade to Versa Director version 22.1.4 or later is critical.
- Check the /var/versa/vnms/web/custom_logo/ directory for any suspicious .png files and verify their authenticity.
- Implement the recommended firewall and system hardening guidelines to prevent exposure of management ports.
- Review system logs for suspicious activity, audit user accounts, and rotate credentials as a precaution.
The Cybersecurity and Infrastructure Security Agency (CISA) has added this vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, underscoring the urgent need for organizations using Versa Director to take immediate action. Given the potential for ongoing exploitation, organizations are urged to prioritize these mitigations to safeguard their network infrastructure against this sophisticated threat.







Leave a Reply