
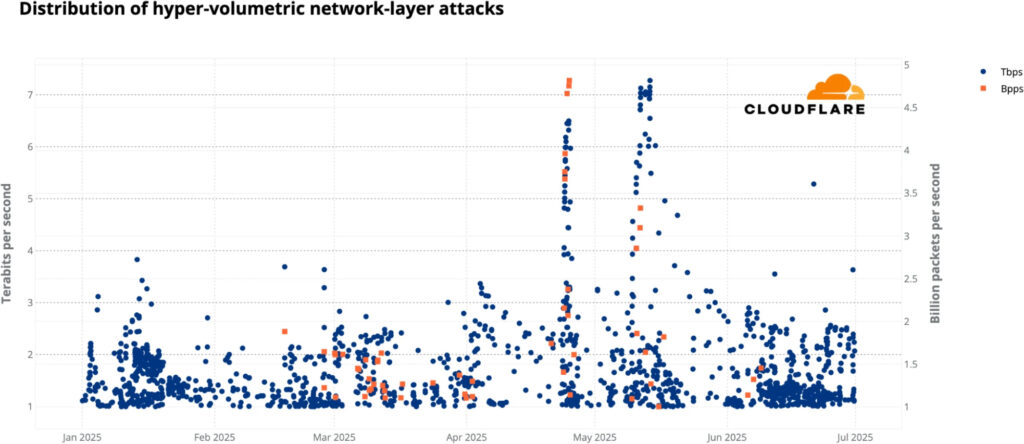
Cloudflare's Q2 2025 DDoS threat report reveals a dramatic surge in hyper-volumetric attacks, with over 6,500 incidents recorded in just three months, representing a staggering 65-fold year-over-year increase.
These attacks, which exceed 1 Tbps or 1 billion packets per second (Bpps), now occur at a rate of 71 per day, highlighting a shift toward shorter, more intense bursts of traffic aimed at overwhelming targets in seconds.
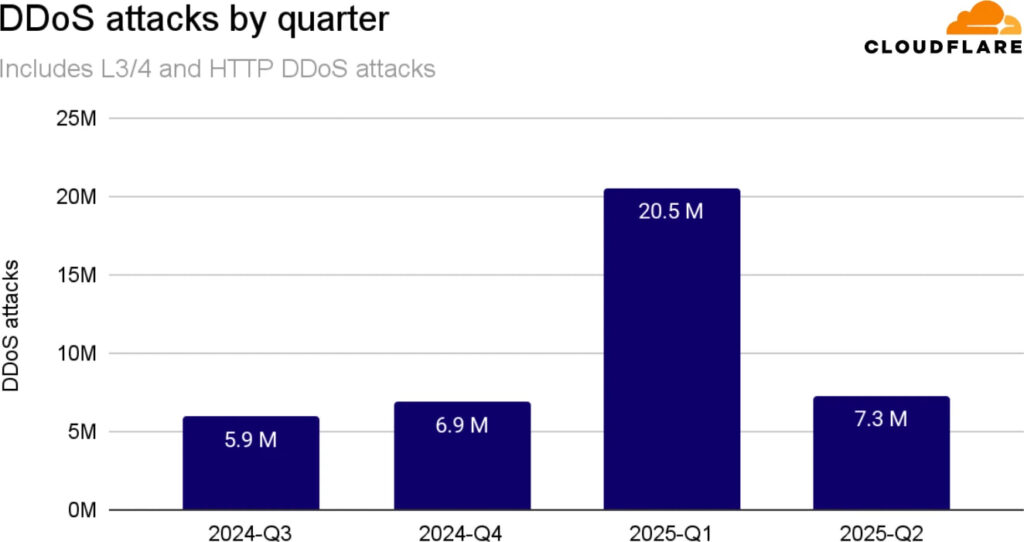
While the total number of DDoS attacks dropped to 7.3 million, down from Q1's anomalous 20.5 million, the proportion of hyper-volumetric attacks has sharply increased, signaling an escalation in the severity and sophistication of the threat landscape.
One key incident underscoring this trend was the record-breaking 7.3 Tbps DDoS attack in May 2025. That incident targeted a hosting provider and was mitigated in under a minute using Cloudflare's autonomous systems. The attack utilized legacy amplification protocols such as QOTD, Echo, NTP, and RIPv1, and was launched from over 122,000 source IPs across 5,433 networks in 161 countries.
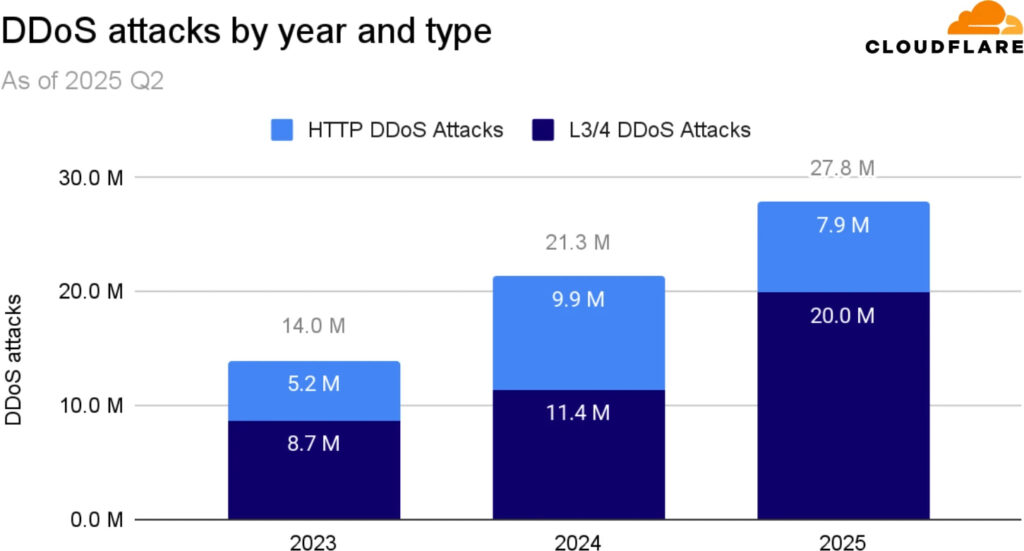
Cloudflare defines hyper-volumetric DDoS attacks as Layer 3/4 floods exceeding 1 Tbps or 1 Bpps, or HTTP attacks above 1 million requests per second (Mrps). In Q2 2025 alone, Cloudflare mitigated double the number of attacks crossing the 1 Tbps or 1 Bpps threshold compared to the previous quarter. The volume of attacks exceeding 100 million pps also skyrocketed by 592%.
Cloudflare, a San Francisco-based security and web performance company with over 330 data center locations, protects a diverse range of entities, including independent media outlets and telecommunications giants. One notable target in Q2 was an Eastern European news outlet that came under attack shortly after reporting on a local Pride parade, a reminder that politically or socially sensitive content continues to attract targeted DDoS campaigns.
Telecommunications firms, ISPs, and service providers reclaimed their spot as the most attacked industry this quarter, followed by the Internet sector and IT services. On a geographic basis, China, Brazil, and Germany accounted for the most targeted customer locations, while Indonesia, Singapore, and Hong Kong were the top source countries for DDoS traffic, though Cloudflare notes these represent where attack traffic entered their network, not necessarily where attackers reside.
A significant portion of the threat is now driven by VM-based botnets hosted in cloud environments, which Cloudflare reports to be up to 5,000 times more potent than traditional IoT botnets. The company identified Austria-based Drei (AS200373), DigitalOcean (AS14061), and Germany's Hetzner (AS24940) as the top autonomous systems linked to HTTP-based DDoS activity. Over 70% of HTTP DDoS attacks were attributed to known botnets, which Cloudflare's real-time detection systems now fingerprint and block globally within seconds of identification.
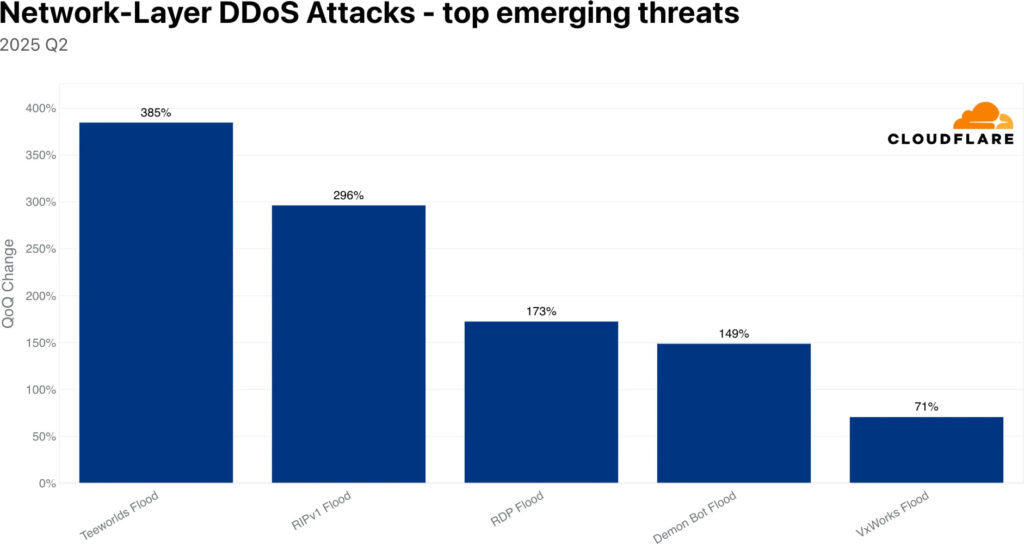
Layer 3/4 attack vectors in Q2 were dominated by DNS floods, SYN floods, and UDP floods, while emerging threats saw massive upticks in obscure and legacy protocol abuses such as Teeworlds floods (+385%), RIPv1 floods (+296%), and RDP reflection attacks (+173%). These shifts highlight attackers' efforts to evade conventional defenses by recycling lesser-known or outdated protocols.
Despite the rise in hyper-volumetric events, most DDoS attacks remain under 500 Mbps or 50,000 pps, but even these “small” attacks can knock unprotected infrastructure offline. Cloudflare emphasizes that short-duration bursts, like the 45-second 7.3 Tbps incident, are increasingly being used to overwhelm targets before defenses activate.
Organizations are recommended to implement layered, always-on DDoS mitigation. Cloud-based solutions capable of real-time fingerprinting and autonomous response are crucial for defending against both large-scale floods and application-layer attacks, while legacy protocols such as NTP, RIPv1, and QOTD should be disabled or properly secured.







Leave a Reply