
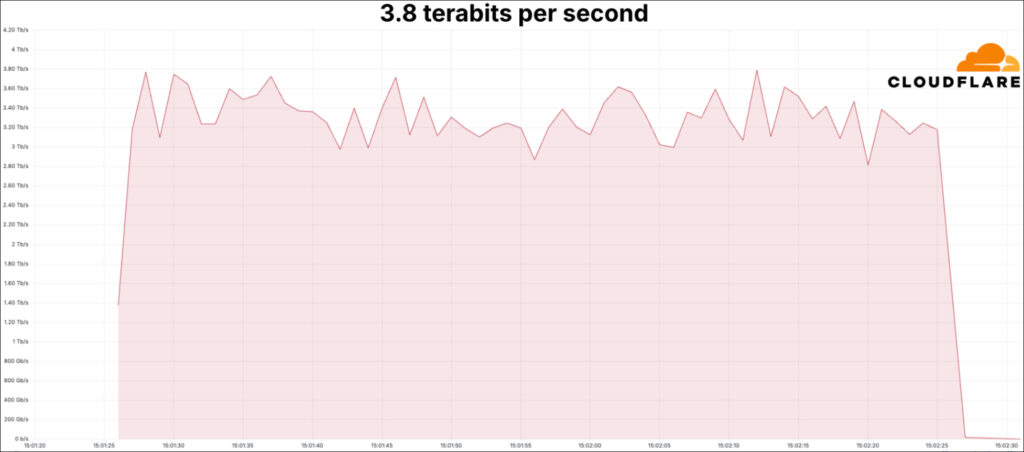
Cloudflare's DDoS protection systems have successfully mitigated a massive campaign of Layer 3/4 DDoS attacks that started in early September 2024. Among these, the company faced and mitigated the largest recorded attack in internet history, peaking at 3.8 Tbps, alongside many others exceeding 2 billion packets per second (Bpps) and 3 Tbps.
The mitigation process was fully autonomous, according to Cloudflare, demonstrating its advanced capability to handle hyper-volumetric attacks without disrupting legitimate traffic.
Breakdown of the DDoS attacks
The attacks that Cloudflare mitigated throughout September were primarily aimed at saturating bandwidth and exhausting CPU resources in targeted networks. They affected customers in diverse industries, including financial services, internet service providers, and telecommunications.
While Cloudflare's customers were shielded from harm, the magnitude and scale of the attacks highlight a rising trend of volumetric DDoS campaigns that can cripple unprotected or inadequately protected internet properties.
Cloudflare
The attacks predominantly leveraged User Datagram Protocol (UDP) on a fixed port and originated from a wide array of sources worldwide, with notable activity traced back to Vietnam, Russia, Brazil, Spain, and the United States. Two key components drove the attacks:
- High packet rates: These were traced to various compromised devices, such as MikroTik routers, DVRs, and web servers, orchestrated to flood the target with massive traffic.
- High bitrates: These originated mainly from compromised ASUS home routers, likely through exploitation of a critical CVE 9.8 vulnerability discovered by Censys, enabling attackers to control and direct these routers in the DDoS campaign.
Potential objectives
DDoS (Distributed Denial of Service) attacks aim to deny access to legitimate users by overloading a target's resources. The primary goal of these Layer 3/4 attacks was to exhaust CPU cycles and overwhelm network bandwidth.
When a network receives packets, each packet needs to be processed and routed to its destination. DDoS attacks exploit this by sending a high rate of packets, which can saturate CPU resources and prevent legitimate requests from being processed.
DDoS attacks also work by saturating the available bandwidth of a server, effectively choking the network's capacity to handle legitimate traffic. When attackers flood a network with more data than it can handle, both good and bad traffic are discarded, leading to denial of service.
Cloudflare's defense strategies
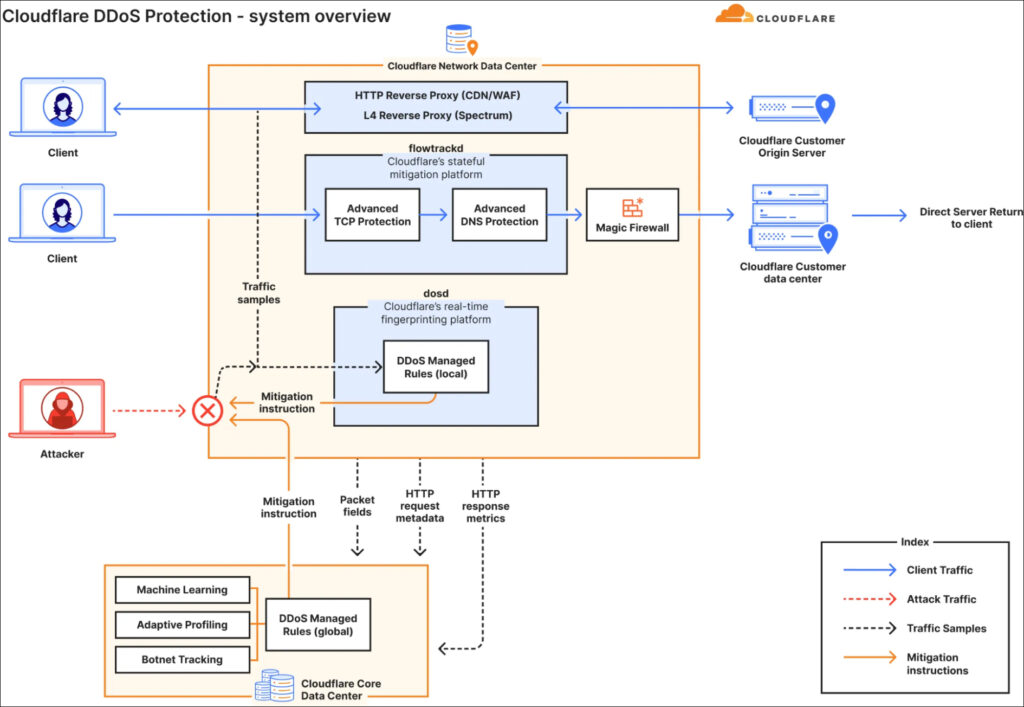
Cloudflare's defense is built on a global network architecture and a variety of autonomous detection and mitigation techniques:
By utilizing an anycast network model, Cloudflare can distribute incoming attack traffic across a wide array of data centers globally. This helps dilute the volume of malicious traffic, ensuring no single data center is overwhelmed. Attack traffic is thus handled closer to its point of origin — an infected device in Dallas, Texas, would be mitigated by a Cloudflare server in Dallas and similarly for other global locations.
Cloudflare uses eXpress Data Path (XDP) and extended Berkeley Packet Filter (eBPF) technology to sample traffic, analyze it for anomalies, and quickly create signatures to identify and block attack traffic. This is facilitated by their denial of service daemon (dosd), which can push out mitigation rules in real time as attack patterns are recognized. This occurs at the individual server, data center, and global level, all within Cloudflare's autonomous software-defined network.
In addition to dynamic fingerprinting, Cloudflare employs multiple layers of protection, including Advanced TCP and DNS Protection systems to detect sophisticated attack patterns and machine learning for adaptive traffic profiling. The defenses utilize statistical analysis and real-time threat intelligence to respond to evolving attack vectors.
Cloudflare
Attacks at that scale can easily overwhelm traditional defense mechanisms, says Cloudflare, particularly for entities relying on on-premise equipment or cloud providers lacking global network capacity. With attacks reaching as high as 3.8 Tbps and 2.14 Bpps, only networks with extensive resources and global distribution can handle the massive scale and rate of such attacks without also dropping legitimate traffic.







Leave a Reply