
The Clop ransomware gang has claimed responsibility for the November cyberattack against Blue Yonder, a major supply chain management software provider. In an update on their dark web leak site, Clop listed Blue Yonder among several new victims of their ongoing “Cleo campaign,” which involved the exploitation of vulnerabilities in Cleo's managed file transfer (MFT) software. Other companies named in the update include Linfox, Covestro, Nissin Foods, Hertz, and Arrow Electronics.
The “Cleo campaign” refers to a series of cyberattacks leveraging two zero-day vulnerabilities — CVE-2024-50623 and CVE-2024-55956 — in Cleo's MFT platforms. These flaws, which were exploited to gain unauthorized access to corporate networks, allowed Clop to steal sensitive data from targeted organizations. Clop confirmed their involvement in these attacks in December 2024, stating that they had been behind both the initial exploitation of Cleo software and the follow-up breaches.
The latest update from Clop suggests that their attack campaign is ongoing and expanding. However, none of the newly named companies — including Blue Yonder — have publicly acknowledged being compromised via Cleo vulnerabilities. Blue Yonder previously confirmed a ransomware attack on November 21, 2024, which disrupted its managed services environment. At the time, the company did not attribute the attack to Clop or mention any connection to the Cleo exploits.
Blue Yonder, headquartered in Arizona, specializes in cloud-based supply chain, manufacturing, and retail planning solutions used by enterprises worldwide. Its platforms help businesses optimize inventory, forecast demand, and streamline logistics. A ransomware attack against such a company poses significant risks, as service disruptions could have widespread effects on its corporate clients.
The other named companies — Linfox (a logistics firm), Covestro (a chemical manufacturer), Nissin Foods (a major food producer), Hertz (a global car rental company), and Arrow Electronics (a technology distributor) — operate in diverse industries, suggesting that Clop is targeting a broad range of organizations rather than focusing on a specific sector.
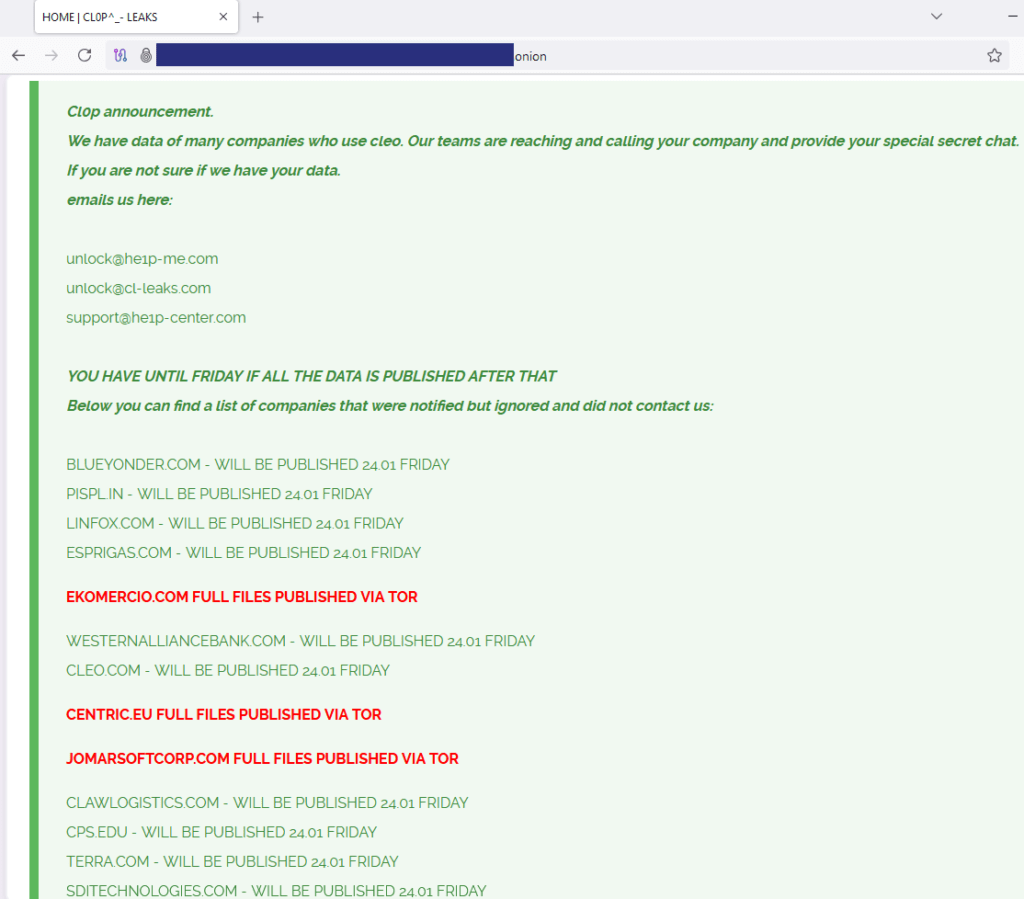
As of now, none of the companies listed by Clop have issued public statements confirming or denying a breach. Blue Yonder remains the only firm to have acknowledged a ransomware incident, but they have not confirmed Clop's involvement. The lack of official disclosures leaves open questions about the extent of the breaches and whether Clop's claims are entirely accurate.
In any case, organizations using Cleo's MFT solutions should ensure they have applied the latest patches—version 5.8.0.24, which addresses CVE-2024-55956. Additionally, it is recommended that network traffic be monitored for unauthorized file transfers, system logs be reviewed for unusual activity related to Cleo Harmony, VLTrader, or LexiCom, and multi-factor authentication (MFA) be implemented on all accounts.







Leave a Reply