
ReliaQuest has identified a novel method in the ClearFake campaign, involving users manually executing malicious PowerShell code, thereby bypassing existing security controls.
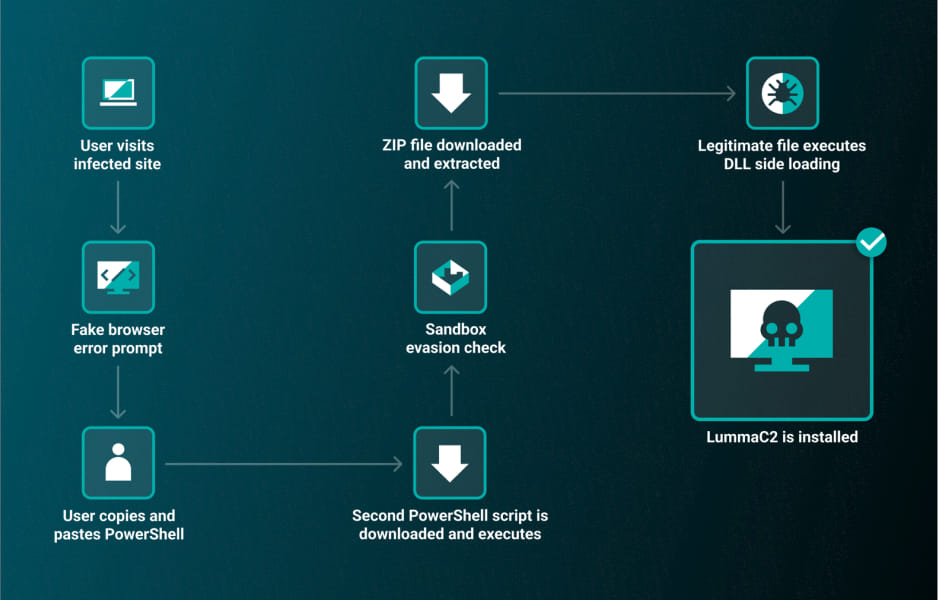
On May 26, 2024, the ReliaQuest Threat Research Team discovered a new attack vector used by the ClearFake JavaScript framework. Unlike traditional drive-by downloads associated with ClearFake, this campaign tricks users into manually copying and pasting malicious PowerShell code, circumventing automatic detection mechanisms. Upon execution, the PowerShell script clears the DNS cache, displays a message box, downloads additional code, and installs the LummaC2 malware.
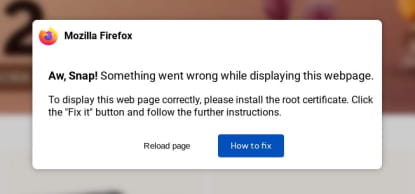
ClearFake, known for its social engineering tactics, typically lures victims to fake browser update pages. In this latest campaign, users visiting compromised legitimate websites are presented with a fake error prompt instructing them to install a root certificate. Following these instructions leads users to manually execute obfuscated PowerShell commands, which then install LummaC2, an information-stealing malware.
New ClearFake attack flow
The attack begins when a user visits a compromised site, displaying a prompt to install a root certificate to fix a displayed error.
ReliaQuest
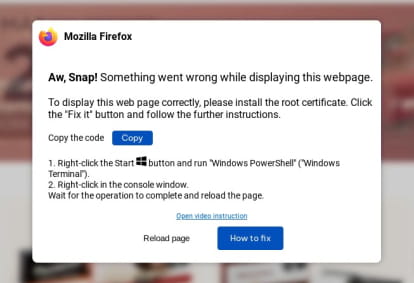
Upon clicking the “Fix it” button, users are directed to copy a block of PowerShell code. This code is obfuscated using base64 encoding to evade detection.
ReliaQuest
When executed, it performs several functions:
- Flushes the DNS cache.
- Displays a success message using the Windows .NET MessageBox class.
- Downloads further malicious PowerShell code from the domain “rtattack.baqebei1[dot]online.”
- Clears the user's clipboard and PowerShell screen to hide traces.
A significant aspect of this campaign is its evasion of sandbox environments. The malicious PowerShell script checks the infected device's CPU temperature. If it returns null (as it would in a virtual environment), execution halts. Otherwise, it proceeds to download a ZIP file from “cdnforfiles[dot]xyz,” containing both a legitimate executable and a malicious DLL, exploiting DLL sideloading to install LummaC2.
ReliaQuest
Case studies
Case Study 1: A user visited a compromised website, leading to the execution of the initial PowerShell script. The second stage download attempt was blocked by existing controls, preventing further infection.
Case Study 2: Another user followed the instructions, successfully executing the PowerShell script and downloading additional malware. The infection was detected by ReliaQuest, which blocked the malicious domains and recommended a full system re-image.
Defensive Measures and Recommendations
To mitigate this threat, organizations should implement the following measures:
- Restrict PowerShell execution to only necessary users.
- Block access to newly registered or suspicious domains, especially those with .xyz TLDs.
- Configure Windows Defender Application Control (WDAC) to enforce constrained language mode for PowerShell.
- Integrate endpoint detection tools with Windows Antimalware Scan Interface (AMSI) to analyze script commands before execution.







Leave a Reply