
Researchers at Citizen Lab have identified critical network security vulnerabilities in RedNote, a popular Chinese social media app with over 300 million users.
Their findings reveal that RedNote transmits user data with insufficient encryption, leaving browsing activity, device metadata, and even personal files exposed to network attackers. The security flaws stem from weaknesses in RedNote itself as well as vulnerabilities introduced by third-party software development kits (SDKs) from NEXTDATA and MobTech. Despite responsible disclosure, none of the involved companies have responded or implemented fixes.
This latest Citizen Lab report comes as a confirmation of a report by Corrata security researchers, who warned last month about RedNote’s abysmal data handling practices that left user communications and data exposed to man-in-the-middle attacks.
Citizen Lab’s research focused on network security risks in RedNote’s Android and iOS applications. Their analysis uncovered three major issues:
Unencrypted Multimedia Traffic
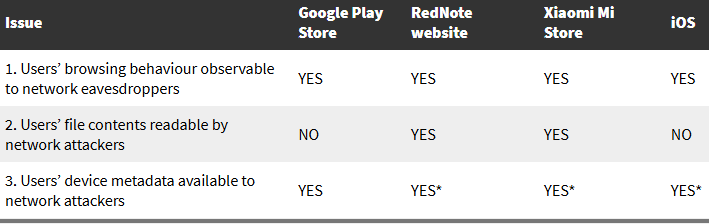
All versions of RedNote fetch images and videos over unencrypted HTTP connections. This allows network eavesdroppers—such as internet service providers (ISPs), virtual private networks (VPNs), or malicious actors—to determine exactly what content a user is browsing.
File Exposure on Certain Android Versions
Some versions of RedNote for Android—specifically those downloaded from RedNote’s official website and the Xiaomi Mi Store—contain a vulnerability that allows attackers to read any file the app has permission to access. This flaw originates from the NEXTDATA SDK, which is used for fraud prevention. The issue is not present in the Google Play Store version or on iOS.
Device Metadata Leaks
All tested versions of RedNote transmit sensitive device metadata—including screen size, RAM, mobile carrier, and manufacturer—using weak encryption. Some versions use TLS without certificate validation, making it possible for an attacker with a man-in-the-middle (MITM) position to intercept this data. This issue is introduced by the MobTech analytics SDK.
Citizen Lab
RedNote, also known as XiaoHongShu, is a Chinese social media platform often described as a mix of Instagram and Pinterest. While it has long been popular in China and among the Chinese diaspora, the app recently gained millions of new users in the United States after a proposed ban on TikTok. The newfound international interest has also brought increased scrutiny of RedNote’s security and data handling practices.
Disclosure timeline and lack of response
Citizen Lab’s research involved static and dynamic analysis methods, including reverse engineering the app’s code, monitoring network traffic, and testing proof-of-concept exploits. The vulnerabilities were confirmed across multiple versions of RedNote, including those from the Apple App Store, Google Play Store, Xiaomi Mi Store, and RedNote’s official website.
- November 2024 – Citizen Lab discovered vulnerabilities in the NEXTDATA and MobTech SDKs and disclosed them to their respective vendors on November 13 and 26, respectively.
- January 2025 – Researchers re-tested the app and found the vulnerabilities still present. On January 16, they disclosed the issues to RedNote.
- February 12, 2025 – With no response from RedNote, NEXTDATA, or MobTech, Citizen Lab published its findings publicly.
These vulnerabilities present a significant risk, particularly for users in foreign countries. The security flaws expose Chinese tourists, expatriates, and the growing U.S. user base to surveillance by ISPs and governments outside China. Unlike concerns about potential Chinese government data access, these issues make RedNote users vulnerable to monitoring by any network attacker, including those in the United States and Five Eyes intelligence alliance countries.
RedNote users should use a trusted VPN to encrypt network traffic and reduce exposure to ISPs and attackers. Ideally, using RedNote on unsecured networks such as public Wi-Fi, where attackers can easily intercept data, should be completely avoided. Until RedNote and its SDK providers address these vulnerabilities, users should remain cautious about the privacy and security risks associated with the app, and consider alternative platforms.







Leave a Reply