
The People's Republic of China (PRC) state-sponsored cyber group, APT40, has been identified as a significant threat to Australian networks, according to a new advisory. The advisory, issued by a coalition of international cybersecurity agencies, outlines the tactics, techniques, and procedures (TTPs) employed by APT40 in their cyber operations, which are linked to the PRC's Ministry of State Security (MSS).
Background
This detailed advisory is a collaborative effort from multiple international cybersecurity agencies, highlighting APT40's ongoing threat to networks, particularly in Australia.
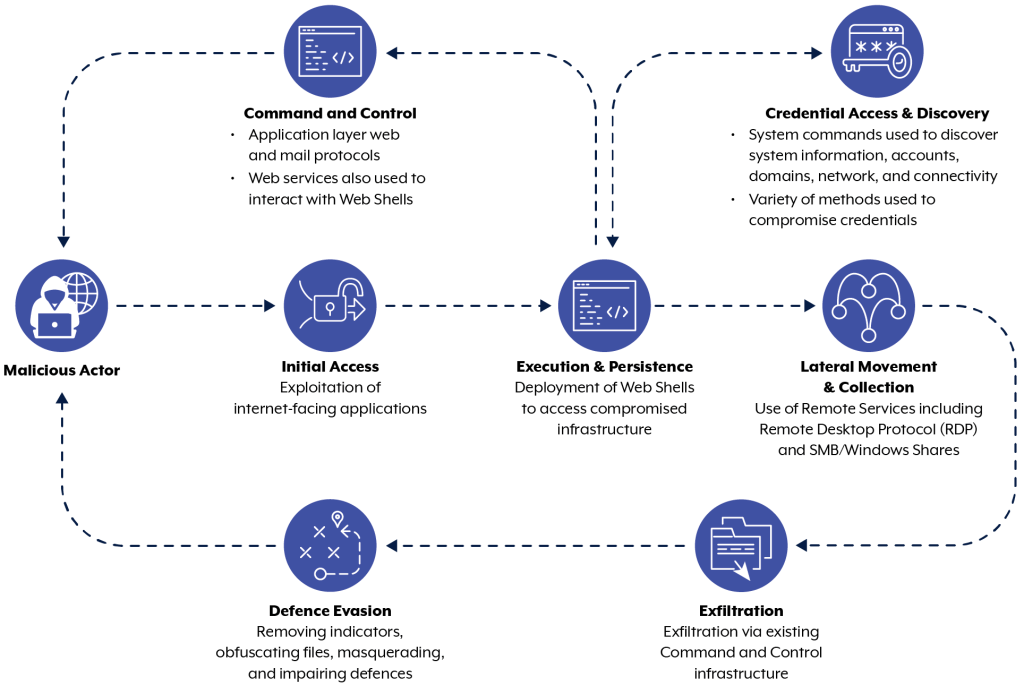
APT40, also known by aliases such as Kryptonite Panda and Leviathan, has a history of targeting organizations in various countries, including Australia and the United States. Their modus operandi involves exploiting public-facing infrastructure and rapidly adapting new vulnerabilities for their malicious operations.
APT40's recent activities include exploiting widely used software vulnerabilities such as Log4J (CVE-2021-44228), Atlassian Confluence (CVE-2021-26084), and Microsoft Exchange (CVE-2021-34523). The group prioritizes gaining valid credentials to maintain persistent access to their targets' networks, often utilizing web shells for initial access and persistence.
APT40 prefers exploiting vulnerable public-facing infrastructure over phishing techniques. They often use compromised devices, including small-office/home-office (SOHO) devices, as operational infrastructure. This technique, observed in Australia and globally, involves using end-of-life or unpatched devices for launching attacks, blending malicious traffic with legitimate network activity to evade detection.
CISA
APT40 attack case studies
The advisory includes two anonymized case studies illustrating APT40's techniques. In one case, the group compromised an Australian organization's network from July to September 2022. Key activities observed included host enumeration, web shell deployment, and lateral movement through the network. The investigation revealed the compromise was facilitated by multiple access vectors and insecure internally developed software. Sensitive data and privileged authentication credentials were exfiltrated, underscoring the group's capability to conduct sophisticated and sustained cyber operations.
In the second case, APT40 exploited a remote access login portal of another organization in April 2022. The attackers deployed web shells and escalated privileges to capture several hundred unique username and password pairs. These credentials allowed the attackers to create remote login sessions and access the internal corporate network, indicating the group's proficiency in exploiting remote access vulnerabilities.
Defense recommendations
To mitigate APT40's threats, the advisory recommends several measures, including:
- Patch management: Promptly patch all internet-exposed devices and services within 48 hours of vulnerability disclosure.
- Network segmentation: Implement network segmentation to limit lateral movement. Critical servers should be accessible only through well-secured intermediary servers.
- Multi-factor authentication (MFA): Enforce MFA on all internet-accessible remote access services, including web and cloud-based email, collaboration platforms, and VPN connections.
- Web aoplication firewalls (WAFs): Deploy well-tuned WAFs to protect web servers and applications.
- Replace End-of-Life (EoL) equipment: Ensure all devices are up-to-date and replace any end-of-life equipment to reduce vulnerabilities.
Additionally, organizations are encouraged to implement the ASD Essential Eight Controls and associated Strategies to Mitigate Cyber Security Incidents for comprehensive network defense.







Leave a Reply