
New research from Positive Technologies has attributed the Operation ForumTroll campaign, which exploited Google Chrome's CVE-2025-2783 zero-day earlier this year, to an advanced persistent threat group tracked as Team46, previously known under the alias TaxOff.
While the vulnerability itself has been patched since March, this latest analysis sheds light on the full infection chain and reveals the extent to which Chrome's sandbox escape was only the beginning of a much deeper compromise.
The campaign, originally uncovered by Kaspersky, targeted Russian academic, governmental, and media organizations through personalized phishing emails impersonating the Primakov Readings forum. Clicking the link silently exploited the CVE-2025-2783 flaw in Chrome, allowing attackers to escape the browser's sandbox and execute malicious code without user interaction. At the time, the identity of the attackers and their objectives remained unclear.
According to Positive Technologies, the post-exploitation payloads and command structures used in Operation ForumTroll match earlier campaigns by Team46, including unique loader behavior, domain infrastructure, and malware deployment patterns. Their investigation reexamines the campaign from March and connects it with phishing operations dating back to late 2024, revealing that the same actor has been active for months under two separate names.
Dropping the Trinper backdoor
The Chrome vulnerability, caused by a mishandled object in Mojo on Windows, allowed attackers to break out of the browser's security sandbox and trigger a PowerShell command to fetch a remote script. This script downloaded a decoy PDF mimicking forum documents, and a second-stage payload using domain names engineered to appear legitimate, such as ms-appdata-query.global.ssl.fastly.net.

Positive Technologies
That payload turned out to be a loader for Trinper, a custom backdoor designed for persistence, surveillance, and data exfiltration. The loader decrypts its payload in multiple stages using keys derived from machine-specific data like the system's firmware UUID and process names, ensuring the malware only executes on preselected targets.
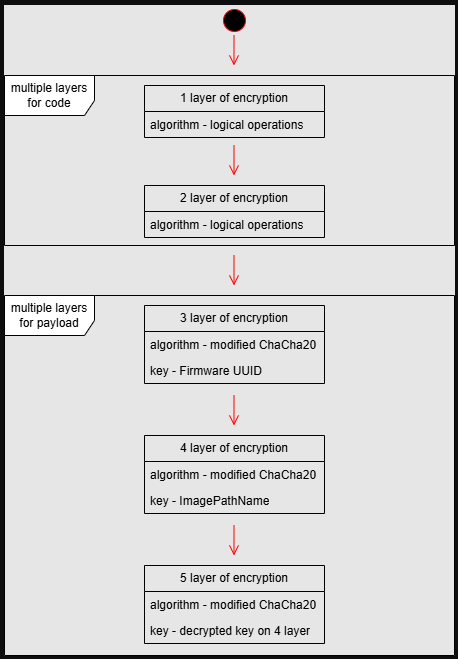
Positive Technologies
Once installed, Trinper grants attackers long-term access to the compromised system, enabling keylogging, clipboard monitoring, file enumeration, and encrypted command-and-control via HTTPS. In some variations, Cobalt Strike is delivered instead of Trinper, using similar loader logic.
Attribution to Team46
Positive Technologies concluded that Team46 and the previously named TaxOff group are the same actor, based on overlapping PowerShell command structures, matching loader functionality, and identical obfuscation techniques. The group's operational infrastructure also shows consistency in using hyphenated domain names on CDN-like services to disguise traffic, with several related to RDP and telemetry themes.
The malware's behavior, particularly the environment-bound decryption chain, suggests a high level of pre-attack reconnaissance. Domains used in ForumTroll were short-lived and taken offline shortly after deployment, adding to the campaign's stealth.
This is not the first time Team46 has exploited a browser vulnerability. In late 2024, they leveraged a DLL hijacking flaw in the Yandex Browser (CVE-2024-6473) using similar phishing tactics. However, CVE-2025-2783 marks their first known use of a zero-click browser escape, significantly raising the threat profile of the group.







Leave a Reply