
Recent investigations by Wladimir Palant reveal that many Chrome Web Store extensions exploit a loophole to manipulate search rankings by using misleading descriptions and irrelevant keywords. This tactic clutters search results with unrelated or dubious extensions, leaving legitimate ones buried under unrelated listings.
The language loophole
The manipulation hinges on Chrome Web Store's multilingual support. Developers can specify localized descriptions for their extensions in any of Chrome's 55 supported languages. Some exploit this by cramming less-used language fields—like Swahili or Estonian—with keywords targeting competitors or popular terms. These keywords then affect search results globally, even in unrelated languages like English.
palant.info
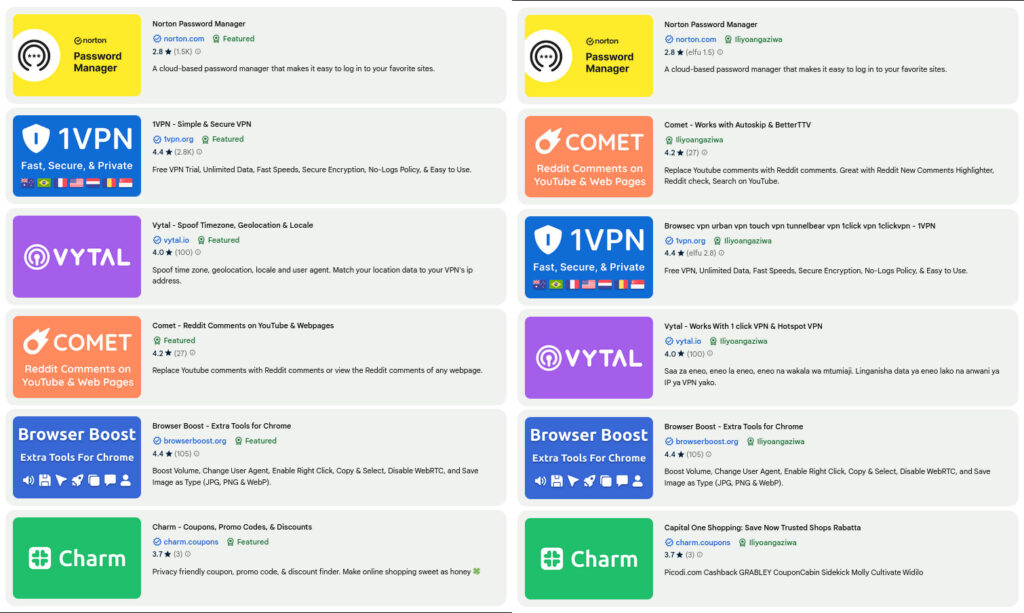
For instance, a search for “Norton Password Manager” initially displayed unrelated extensions at the top, such as VPNs and discount finders, with the legitimate Norton extension buried last.
Extensions employ various approaches to manipulate Chrome Web Store's search results:
- Extensions alter their names across languages to include popular or competing terms.
- Long lists of unrelated keywords are added to descriptions in specific languages.
- Using incomplete or nonsensical translations, often featuring blocks of unrelated English text.
- Using competing product names to hijack search visibility.
Although Google's policy explicitly prohibits spam and abuse, enforcement has been lax. Some of these abuses were reported as early as 2023, and Google has made some adjustments, yet the problems persist.
palant.info
Chrome Web Store abusers
An analysis of over 920 suspect extensions revealed distinct clusters of developers employing this strategy:
- Kodice LLC/Karbon Project LP/BroCode LTD: Known for spamming the Chrome Web Store since 2023, these Russian-speaking developers use misleading names, descriptions, and keywords. Several of their extensions have been linked to spyware and affiliate fraud.
- PDF Toolbox Cluster: Initially flagged in 2023 for hijacking searches and redirecting users, this group continues similar operations with obfuscated code in new extensions.
- ZingFront Software/ZingDeck/BigMData: Supported by Baidu Ventures, this Chinese-based operation boasts over 223 extensions. It leverages AI for monetization through subscription-based premium features.
- Other Groups: Clusters like ExtensionsBox, Lazytech, and Yue Apps operate similarly, often linked to Chinese-speaking developers.
Researcher Wladimir Palant suggests restricting searches to the user's selected language to neutralize keyword stuffing, performing regular audits of known clusters, and penalizing developers who are repeatedly exploiting loopholes.
Regarding what users can do to stay safe in the current landscape, it is recommended to verify developers and read user reviews before installing Chrome add-ons, avoid granting excessive permissions, and notify Google of suspicious extensions.







Leave a Reply