
ThreatFabric analysts have uncovered a sophisticated new mobile malware family named “Brokewell,” characterized by its extensive device takeover capabilities. This malware poses a significant threat to the banking industry by enabling attackers to gain remote access to all assets available through mobile banking apps.
The discovery was made when ThreatFabric analysts stumbled upon a fake browser update page designed to install an Android application, a typical method used by cybercriminals to deploy malware. This seemingly benign update page is just the tip of the iceberg for Brokewell, which has shown prior campaigns targeting financial services and digital authentication applications.
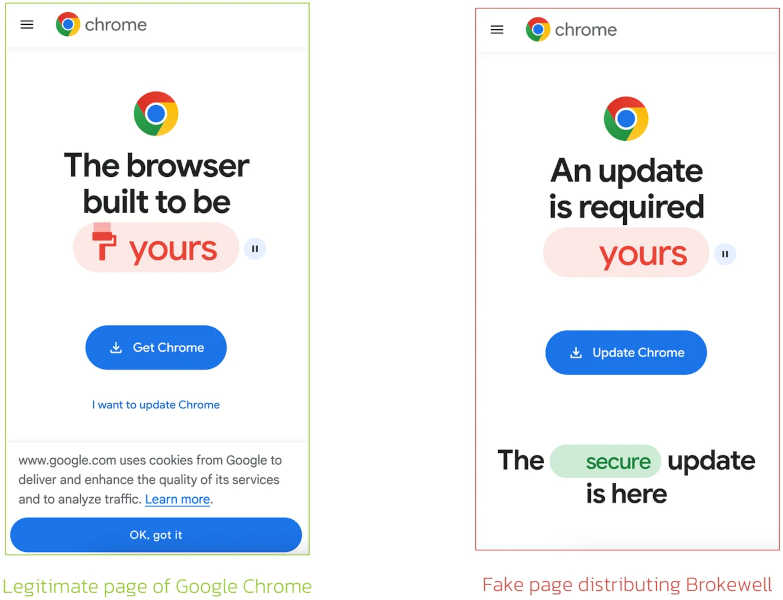
Brokewell capabilities
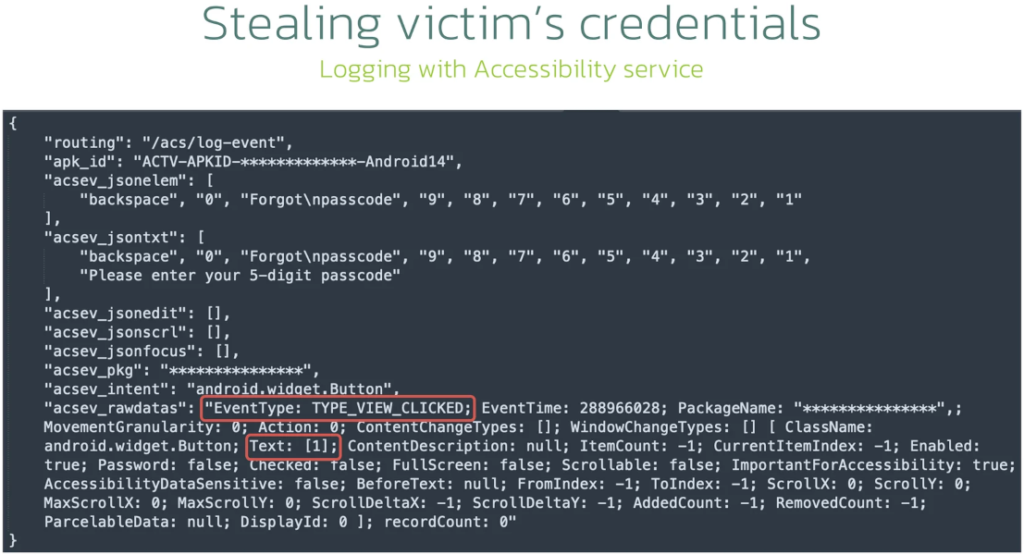
Brokewell is a textbook example of modern banking malware, equipped with data-stealing and remote-control functionalities. The malware uses overlay attacks to capture user credentials and can hijack session cookies, logging every interaction on the device to capture confidential data. Beyond stealing credentials, Brokewell offers a slew of remote control capabilities, including:
- Screen Streaming: Allows real-time observation and interaction with the victim's device.
- Device Actions: Perform clicks, swipes, and keystrokes, simulating user interaction.
- System Controls: Adjust settings such as brightness and volume, and even simulate physical button presses like Home or Back.
This broad range of commands provides cybercriminals with virtually full control over infected devices, facilitating fraud directly from the victims' devices.
Malware origin
Through their investigation, analysts identified a new actor in the mobile malware scene, known as “Baron Samedit.” This individual is associated with the “Brokewell Cyber Labs,” a repository hosting source code for various malware tools, including the “Brokewell Android Loader” designed to bypass new Android 13+ restrictions on Accessibility Service. The actor has been active for at least two years, shifting focus from account theft tools to sophisticated mobile malware, indicating a growing interest in this area among cybercriminals.
The emergence of Brokewell underlines the increasing sophistication of mobile malware, which poses significant challenges for fraud detection systems that rely on device identification. The malware's ability to bypass Android 13+ restrictions suggests that this might become a standard feature in future malware developments, potentially influencing the operations of other cybercriminal groups.
Android users can mitigate the risk of malware infections by remaining vigilant about the authenticity of software update alerts, avoiding downloads from outside the Google Play store, and paying attention to the permissions requested by the app during its installation and first launch on the device.







Leave a Reply