
Researchers from the University of Maryland have uncovered a significant privacy vulnerability in Apple's Wi-Fi-based Positioning System (WPS). This vulnerability enables attackers to track devices globally by exploiting the way Apple's WPS operates, raising serious privacy concerns.
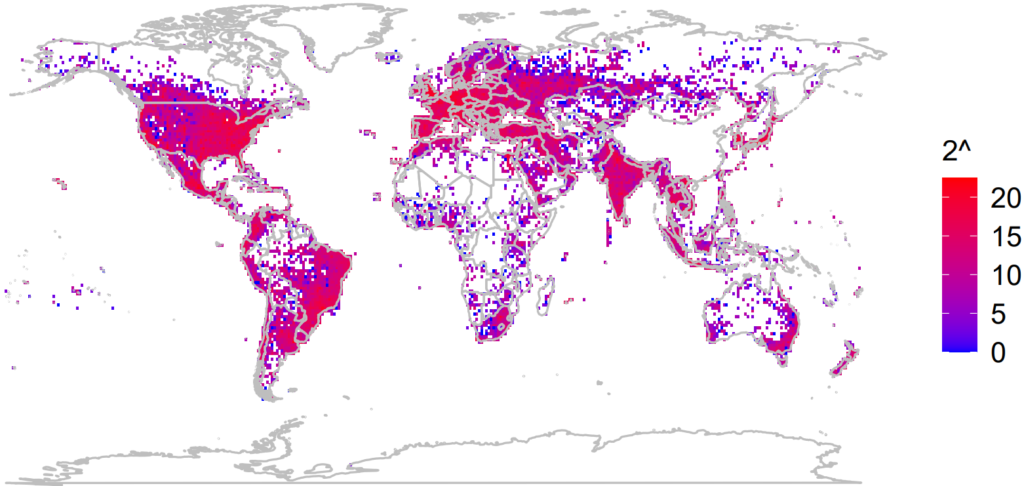
The research, conducted by Erik Rye and Dave Levin, demonstrates how an unprivileged attacker can amass a comprehensive database of Wi-Fi Basic Service Set Identifiers (BSSIDs) locations in just days. By exploiting the limited allocation of MAC address space, the researchers were able to geolocate over 2 billion BSSIDs worldwide within a year.
University of Maryland
Tracking mechanism
Apple's WPS allows mobile devices to learn their location by reporting nearby Wi-Fi access points (APs) MAC addresses (BSSIDs) along with GPS coordinates to a server. This data is then used by other devices to estimate their location without using GPS.
The researchers identified that the system's design allows querying for any MAC address, returning its geolocation if it exists in the database. This loophole can be used for mass surveillance without prior knowledge.
The researchers presented several case studies to illustrate the potential misuse of this vulnerability, including:
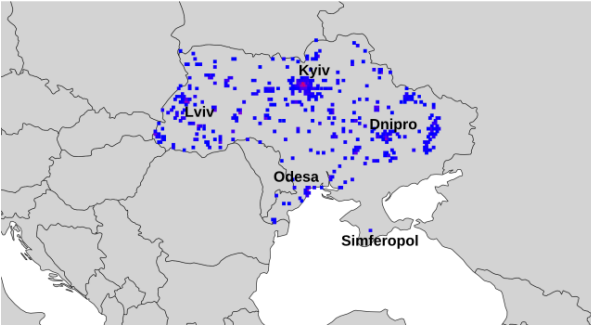
- War Zones: Devices were tracked moving in and out of conflict areas in Ukraine and Gaza, exposing military movements and the locations of displaced individuals.
- Natural Disasters: During the Maui fires, the geolocations of Wi-Fi APs were monitored, demonstrating the impact of the disaster on the infrastructure.
- Targeted Tracking: The vulnerability can be used for stalking or tracking individuals by monitoring the geolocation of their personal devices or APs.
University of Maryland
Safety recommendations
The study concludes with recommendations to mitigate these privacy risks:
- WPS operators should implement rate limits, require API keys, and stop providing unrequested nearby BSSID locations.
- Wi-Fi AP manufacturers are recommended to implement MAC address randomization for APs, similar to client device protections.
- Users should change APs when moving locations and limit the duration of AP usage to avoid them being cataloged in WPS databases.
The findings were responsibly disclosed to Apple and Google, as well as affected manufacturers like SpaceX and GL.iNet. Apple has since introduced an option for users to opt out of the WPS by adding “_nomap” to their SSID. SpaceX has begun rolling out software updates to randomize the BSSID of Starlink routers to protect user privacy.
Maryland University's research highlights the urgent need for improved privacy measures in Wi-Fi-based positioning systems, which are omnipresent in the tech world. The ability to track devices globally through BSSID geolocation poses significant risks, especially for individuals in sensitive or vulnerable situations.







Leave a Reply