
Safari’s inadequate fullscreen mode indicators can be exploited in advanced Browser-in-the-Middle (BitM) attacks, allowing threat actors to steal user credentials without raising suspicion.
While not a technical vulnerability, this design oversight enables attackers to combine legitimate web functionalities with social engineering to create highly convincing phishing setups.
The discovery comes from SquareX’s “Year of Browser Bugs” research project, which investigates how architectural aspects of browsers can be abused by attackers. Unlike many reported vulnerabilities, this issue doesn’t stem from a code flaw in Safari, but rather from its lack of clear visual cues when fullscreen mode is activated. According to SquareX, Apple responded to the disclosure by confirming that Safari’s Fullscreen API behavior, accompanied only by a subtle swipe animation, is working as designed and will not be changed.
BitM attacks, which were first formally described by researchers at the University of Salento in 2021, use remote desktop tools like noVNC to create an attacker-controlled browser session inside a victim’s window. Typically, such attacks are detectable because the parent browser window still reveals the true URL, but when combined with the Fullscreen API, attackers can cover the entire browser surface, effectively hiding any visual indicators that might alert users to a phishing attempt.
SquareX
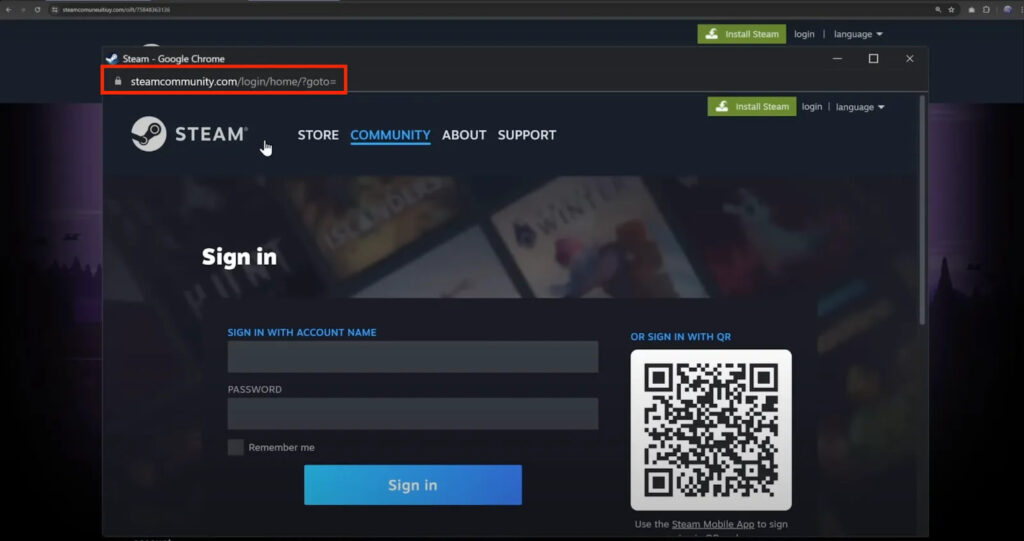
Attackers lure victims using social engineering tactics, such as fake giveaways or malvertising. Victims land on a phishing site impersonating a trusted service, like Figma or Steam, and are prompted to click a login button. This interaction satisfies the Fullscreen API’s requirement for user activation, allowing the attacker’s remote-controlled window to take over the entire screen. On Safari, where no persistent or prominent fullscreen notification is shown, the user remains unaware that they are entering credentials into a fullscreen overlay, not the real site.
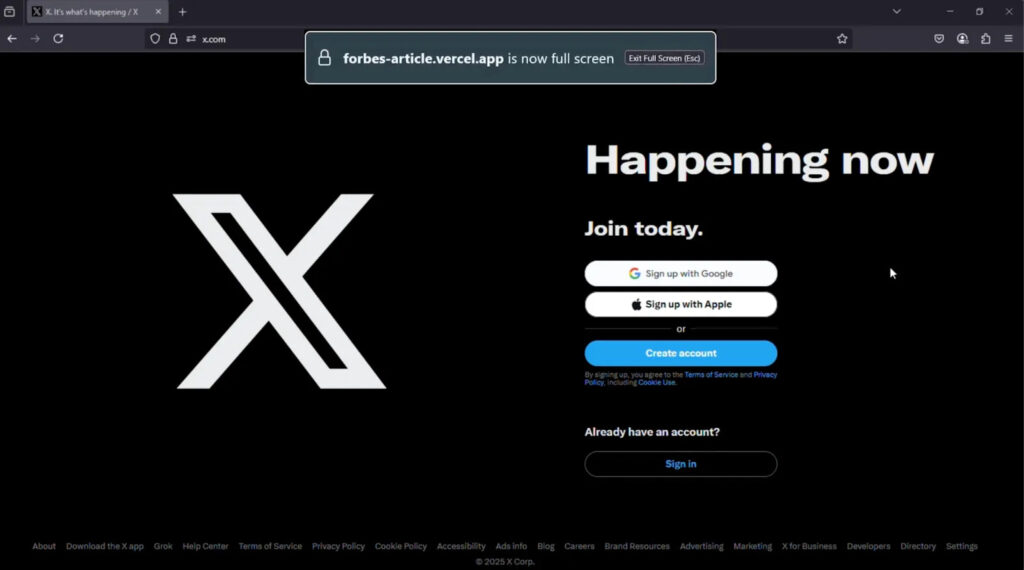
SquareX
Safari’s behavior contrasts with Chromium-based browsers like Chrome and Edge, which show brief fullscreen warnings, and Firefox, which displays domain-specific alerts, although all three browsers have relatively subtle indicators that can be easily missed or visually blended into dark-mode themes. SquareX emphasizes that the Safari case is particularly concerning because of the near absence of cues, making the attack nearly invisible to users.
To defend against these advanced phishing tactics, users should remain vigilant when interacting with login screens, especially when redirected from ads, QR codes, or social media promotions. Enterprises should consider deploying browser-native security tools that can monitor in-browser activities directly, as traditional network- and endpoint-level solutions are blind to attacks that abuse legitimate browser features.






Leave a Reply