
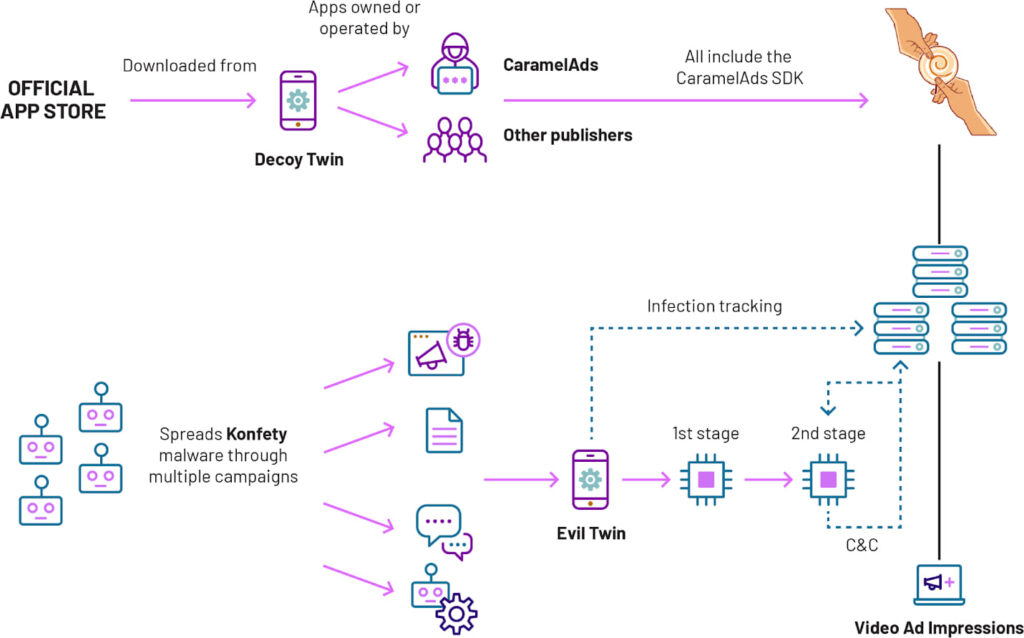
HUMAN's Satori Threat Intelligence and Research Team has disrupted a sophisticated mobile advertising fraud campaign named Konfety. This operation involved using “evil twin” apps, malicious versions of legitimate apps that conducted extensive ad fraud activities.
HUMAN exposed how Konfety exploited the CaramelAds SDK, a mobile advertising software, to carry out fraudulent activities. The decoy twin apps, available on the Google Play Store, appeared harmless, while their evil twins, distributed through malvertising campaigns, performed the actual fraud.
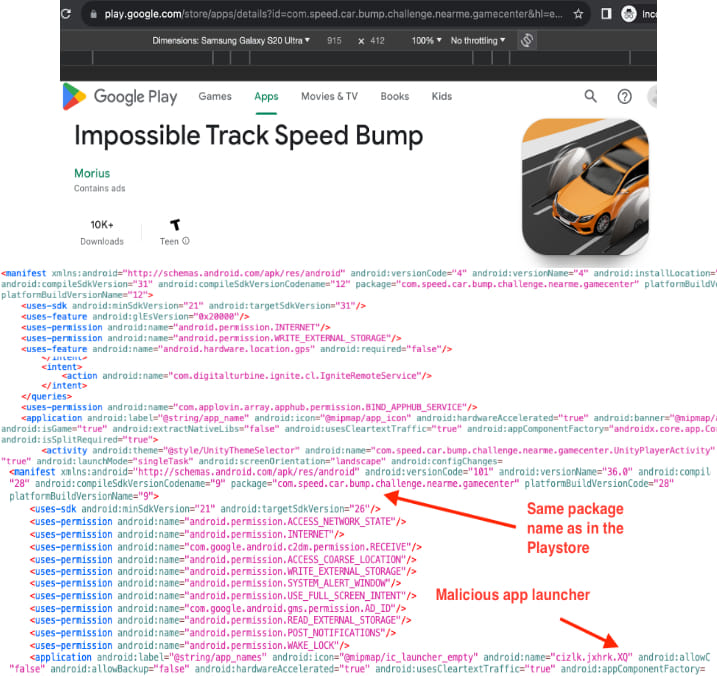
Konfety utilized CaramelAds SDK to render ads, sideload additional code, and communicate with command-and-control (C2) servers. These malicious twins impersonated the decoy apps by using identical app IDs and advertising publisher IDs, deceiving users and ad networks. HUMAN's researchers identified over 250 apps on the Google Play Store with the CaramelAds SDK, each with a corresponding evil twin. At its peak, the Konfety campaign generated up to 10 billion ad requests per day.
HUMAN
Google has implemented measures to protect users, such as Google Play Protect, which warns and disables apps identified as evil twins. Despite this, the evil twin apps continued to spread through third-party sources, using dynamic code loading to avoid detection.
HUMAN's Satori team observed that the CaramelAds SDK, although not inherently malicious, was exploited in various ways, including:
- UserAgent string manipulation: The SDK could alter the device's UserAgent string to appear as different devices.
- Malicious URL opening: The SDK allowed the server to open URLs in the device browser, potentially leading to malicious sites.
- Lack of validation: The SDK did not verify if the device or ads were legitimate.
HUMAN
The Konfety operation's reach was expanded through a malvertising campaign, utilizing a domain generation algorithm (DGA) to create numerous malicious domains. These domains redirected users to download malicious APK files, which then mimicked legitimate apps to conduct fraud.
The evil twin apps performed several malicious activities such as:
- Rendering out-of-context full-screen ads, inflating ad impressions and revenue.
- Downloading additional malicious code based on device conditions.
- Tracking user browser history and redirecting traffic through malicious search toolbars.
Users looking to steer clear from adware fraud on Android should ensure that Google Play Protect is enabled on their devices and avoid downloading apps and APKs from outside the Google Play store.







Leave a Reply