
Security researchers at iVerify have uncovered alarming evidence of a growing underground market where advanced Android malware is available for rent, enabling even low-skilled attackers to launch sophisticated mobile surveillance and fraud campaigns.
The emergence of platforms like PhantomOS and Nebula is democratizing access to dangerous mobile malware, echoing the early evolution of ransomware-as-a-service.
These malware-as-a-service (MaaS) operations are offering turnkey attack kits for as little as $300 per month, complete with capabilities like two-factor authentication (2FA) interception, remote access, GPS tracking, phishing overlays, and evasion from security tools like Google Play Protect. In some cases, cybercriminals don't even need to write a line of code; they simply select their targets and pay a subscription fee.
The PhantomOS malware is being marketed as a high-end MaaS platform tailored to fraud operations. Subscribers receive a custom APK loaded with malicious features such as remote silent app installs, SMS/OTP interception, and UI overlays that impersonate legitimate apps like Coinbase or HSBC. The operator handles backend infrastructure, including private servers and Telegram-based control bots, allowing attackers to manage infected devices via simple chat commands.
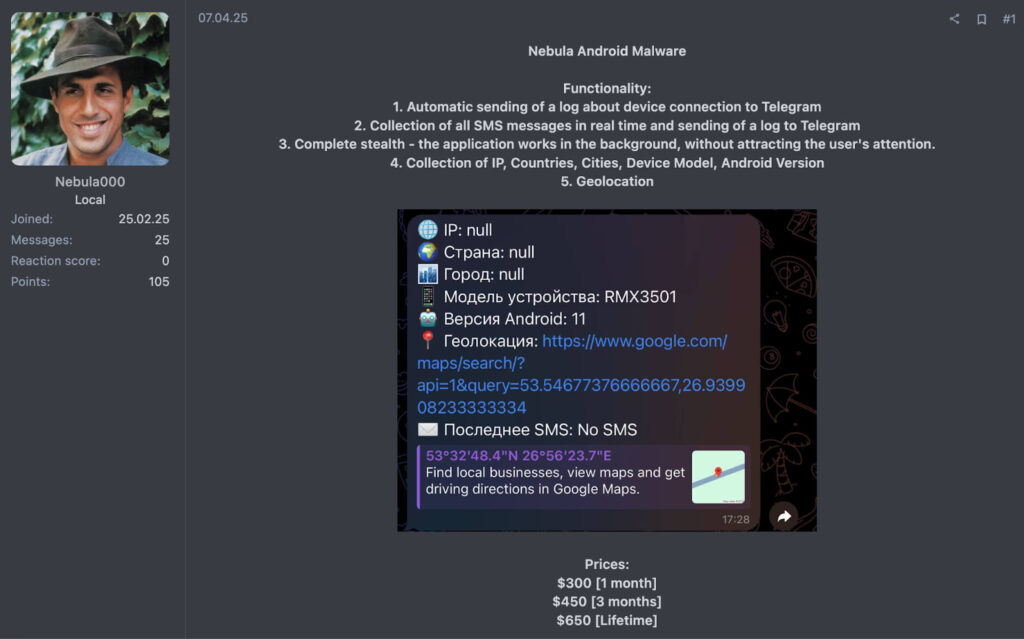
Nebula, another Android MaaS variant, takes a mass-market approach. It advertises “complete stealth” and automation of data theft operations, sending call logs, SMS messages, and location data to attackers through Telegram. With monthly pricing starting around $300 and discounted long-term packages, Nebula illustrates how malware deployment is being packaged and sold like a software subscription.
These offerings are designed to be fully undetectable (FUD), a key selling point among underground vendors. To maintain invisibility, many MaaS operators include or integrate with crypting services that obfuscate malware payloads, ensuring they bypass detection by antivirus engines and Play Protect. Some services rotate cryptographic packers regularly, updating malware signatures to remain stealthy in an ongoing cat-and-mouse game with security tools.
iVerify also noted that social engineering remains common for attackers, with many trojans leveraging phishing overlays that mimic banking and payment app login screens. However, more technical methods are also being sold, including exploit kits that scan for misconfigured Android Debug Bridge (ADB) interfaces or leverage known vulnerabilities to silently deploy malware. These tools, priced between $600 and $750, automate infection at scale, creating botnets from exposed Android devices with little effort.
Adding another layer of commercialization, the MaaS ecosystem now includes marketplaces for pre-infected devices. Sellers like “Valhalla” offer thousands of Android “installs” filtered by geography, allowing buyers to instantly gain access to a fleet of compromised devices for further exploitation. Pricing varies by region, with U.S. or Western European devices commanding premium rates due to their higher financial potential.

The ecosystem has grown to the point where cybercriminals can assemble an end-to-end operation, malware, distribution infrastructure, and infected devices for a few thousand dollars. Tools like the Hydra Android botnet, priced at up to $3,500 with full control and monitoring features, provide functionality such as remote VNC access, SMS interception, screen locking, and even ransomware deployment.
iVerify warns that the accessibility of these tools significantly lowers the barrier for launching complex mobile threats. Android users should verify apps before installing, apply the latest Android security updates, avoid downloading APKs from outside Google Play, and run Play Protect scans regularly.







Leave a Reply