
A new study reveals that thousands of Android apps covertly collect location data using Bluetooth and WiFi beacons, allowing continuous tracking and profiling of users without explicit consent.
Researchers found that 86% of analyzed apps collect sensitive data, including device identifiers, GPS coordinates, and WiFi scan results, often circumventing Android’s privacy controls.
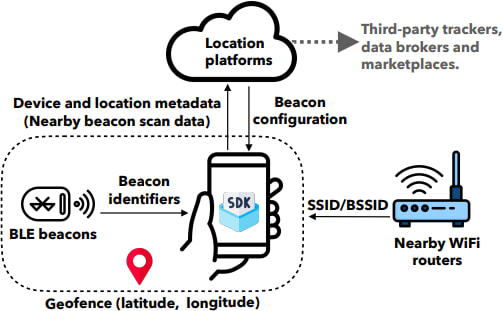
The hidden tracking tools found in these apps come in the form of Software Development Kits (SDKs). An SDK is a bundle of pre-made code that app developers use to add features without building everything from scratch.
However, many SDKs also include data collection features that track users’ behaviors. Even if the app developer isn’t intentionally spying on you, the SDKs they integrate may be quietly collecting your data and sending it to third-party companies — sometimes even selling it to advertisers, marketers, or data brokers.
arxiv.org
How wireless SDKs exploit Android’s permission model
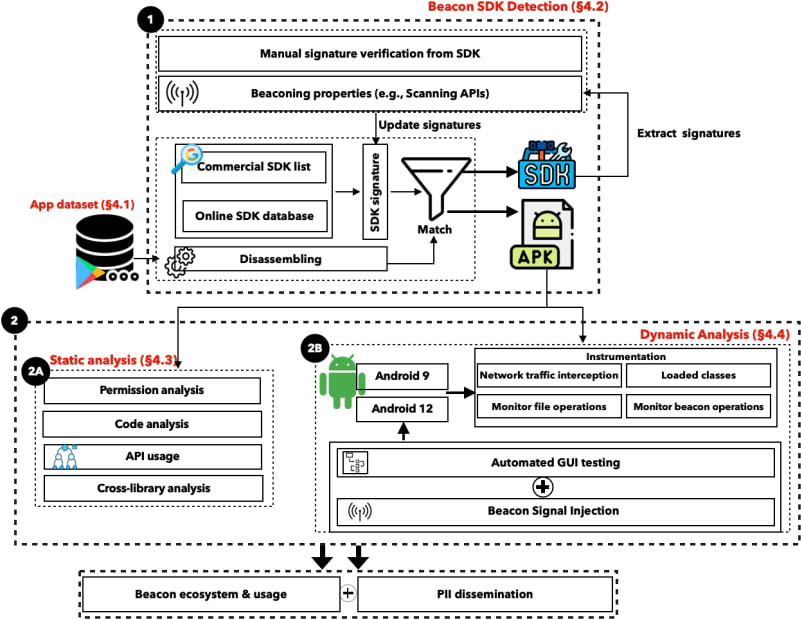
Conducted by researchers from IMDEA Networks, Universidad Carlos III de Madrid, and the University of Calgary, this study systematically analyzed 52 wireless-scanning SDKs across 9,976 Android apps.
arxiv.org
Despite Android’s privacy improvements that restrict direct GPS access, apps still infer user locations by scanning for WiFi access points and BLE beacons, which are tied to physical locations like malls, airports, and stores. The study found that many SDKs perform ID bridging, a technique where persistent and resettable identifiers — such as Android Advertising IDs (AAIDs) and WiFi MAC addresses — are linked together. This enables long-term user tracking, even after users attempt to reset their privacy settings.
Key findings:
- 9,976 apps with wireless-scanning SDKs were analyzed, covering 55 billion installations.
- 86% of apps collected at least one sensitive data type, including GPS, WiFi, and BLE scan results.
- 19% of SDKs engaged in ID bridging, violating privacy expectations and potentially Google Play policies.
- Cross-SDK data sharing was prevalent: 28 SDKs facilitated data exchange between apps, increasing tracking risks.
- Some SDKs exploited Android vulnerabilities in unpatched devices to bypass Bluetooth and WiFi permission restrictions.
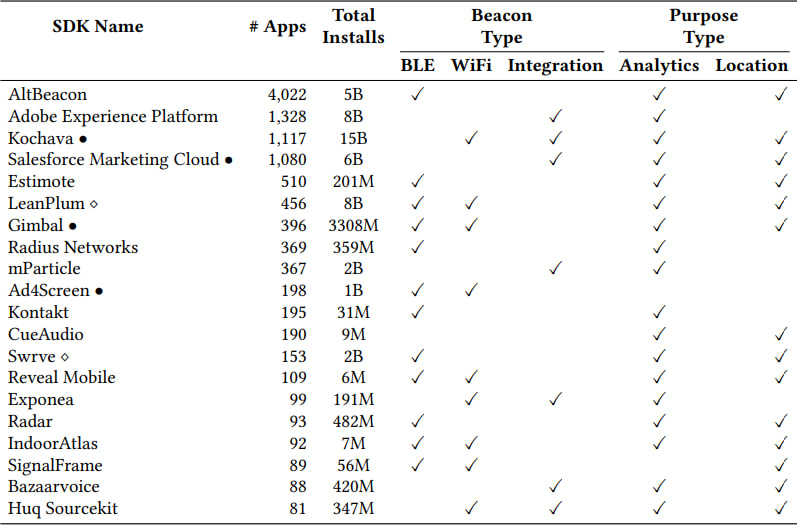
Of the SDKs studied, AltBeacon, Kochava, Salesforce Marketing Cloud, and Adobe Experience Platform were among the most commonly embedded tracking tools. These SDKs not only collect geolocation data but also integrate with other advertising and analytics platforms, amplifying the scale of data aggregation.
arxiv.org
A “shadow location” market
The study underscores how this covert data collection fuels a larger, unregulated location-tracking ecosystem. Companies specializing in advertising, fraud detection, and even government surveillance have been found purchasing location data harvested from mobile apps. Past reports have revealed that firms like Venntel and X-Mode (now Outlogic) sold sensitive location data to law enforcement agencies, raising constitutional and ethical concerns.
This kind of passive tracking poses significant risks to user privacy, enabling the construction of detailed mobility profiles that could reveal work-home locations, religious visits, medical appointments, and political affiliations. The researchers also cited cases where location data was misused to track individuals at sensitive sites such as abortion clinics and military installations.
Given the growing prevalence of covert location tracking, privacy-conscious users should take the following steps:
- Limit Bluetooth and WiFi scanning permissions by turning off Bluetooth and WiFi when not in use.
- Use privacy-focused Android ROMs or custom permissions managers like XPrivacyLua.
- Check app permissions regularly and deny location access to apps that don’t need it.
- Use tracker-blocking tools such as NetGuard or TrackerControl to monitor network traffic from apps.
- Opt out of ad tracking by resetting your Android Advertising ID frequently.
- Use the least required number of apps and avoid installing unnecessary tools.







This has been going on for a very long time, probably at least 10 years now. WeChat is just one of many apps that track your location without having location services enabled.
What is google going to do about this???
❤️
Xprivacylua is 2019 ? Is this a safe app?