
Security researcher Yohanes Nugroho has successfully decrypted files encrypted by the Linux/ESXi variant of Akira ransomware without paying the ransom.
By leveraging GPU-based brute-force techniques, he was able to recover an entire set of VMware files, demonstrating that under certain conditions, Akira’s encryption can be broken.
Nugroho shared his findings and the source code for the decryption tool on GitHub, providing a roadmap for victims who may be able to recover their data. The variant he analyzed has been active since late 2023 and continues to affect organizations in 2024.
His approach relied on the ransomware’s method of using four timestamps — each with nanosecond resolution — to seed its encryption keys. By correlating these timestamps with file modification times and logs, he was able to significantly narrow the brute-force range, making decryption feasible with high-performance GPUs.
Finding a flaw in Akira’s encryption
Akira ransomware encrypts files using a combination of KCipher2 and ChaCha8 encryption, with keys derived from four timestamps (T1-T4). These timestamps are generated at different stages of the encryption process and are used as seeds for a Yarrow256-based random number generator. The ransomware encrypts files in blocks, with the first portion of each block protected using KCipher2 and the rest using ChaCha8. The encryption keys are then encrypted using RSA-4096 and stored at the end of the file.
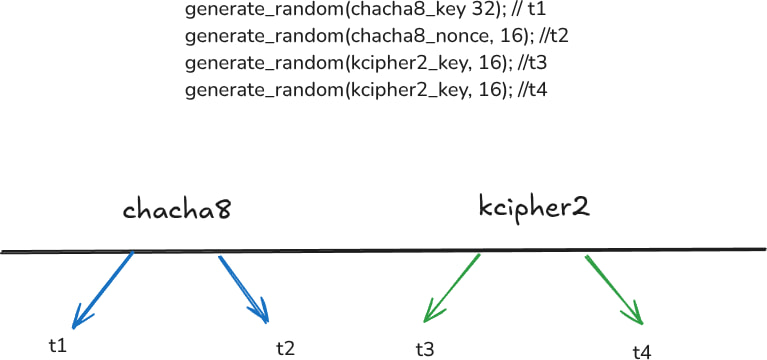
Nugroho’s breakthrough came from recognizing that the ransomware’s seed values were based on the system’s current nanosecond timestamp. While this adds randomness, it also means that if the encryption process is logged or can be estimated, brute-forcing becomes viable. His method involved:
- Extracting timestamps from file modification data and system logs
- Brute-forcing possible timestamp values using GPU acceleration
- Matching computed keys against known plaintext headers from VMware files
Since many VMware file formats have predictable headers (such as flat VMDK and sesparse files), he was able to use these as known plaintexts to test decryption attempts.
TinyHack
Cloud GPUs help overcome performance challenge
Initially, Nugroho attempted CPU-based brute-forcing but found it impractical due to the sheer number of possible timestamp combinations — potentially in the quadrillions. He then moved to GPU acceleration, first testing with an RTX 3060 and later upgrading to an RTX 3090. Further optimizations, including memory management improvements and avoiding unnecessary computation, increased his brute-force speed to 1.5 billion KCipher2 operations per second.
By leveraging cloud GPU services like Runpod and Vast.ai, he was able to significantly reduce costs compared to traditional cloud providers like Google Cloud, which quoted tens of thousands of dollars for the required computing power. Using RTX 4090 GPUs, he estimated that brute-forcing a single second’s worth of possible timestamps (about 1 billion possibilities) would take roughly seven days on a single GPU or just 10 hours using 16 GPUs.
Data recovery process
Nugroho has released a tool that automates much of the brute-force process, but successful recovery still requires technical expertise. To decrypt files, victims must:
- Extract Timestamps: Identify modification times of encrypted files and locate relevant system logs (e.g., ESXi shell logs).
- Obtain Ciphertext and Known Plaintext: VMware file headers can serve as known plaintexts.
- Configure GPU Brute-Force Setup: Rent or use high-performance GPUs and prepare configuration files for brute-forcing.
- Run KCipher2 Brute-Force: Identify the T3 and T4 timestamps using the GPU tool.
- Brute-Force ChaCha8 Keys (If Needed): Larger files may require an additional step to recover the ChaCha8 keys.
- Decrypt Files: Once T1-T4 are recovered, the tool can decrypt the ransomware-encrypted files.
While this method worked in this specific case, Nugroho warns that Akira’s developers will likely modify their encryption approach in response to his findings. This means future versions may not be vulnerable to the same decryption method.







Leave a Reply