
One of the largest fashion and retail outlets in the world has been breached by a high-profile hacking group that goes by the name of ShinyHunters. The hackers exfiltrated data from ABFRL servers and then demanded payment. Now that negotiations have failed, ShinyHunters has published all of the data online, including 5.47 million email addresses. We have examined the data and obtained exclusive commentary from ShinyHunters for this report.
Update 1: Cybersecurity researcher Troy Hunt has now added the data from this breach to the Have I Been Pwned database. (January 14, 2021)
Update 2: ABFRL has finally acknowledged the data breach in an email to customers. (January 17, 2021)
Aditya Birla Fashion and Retail Ltd. (ABFRL) is a large conglomerate retail outlet with 3,212 retail stores throughout India and over 22,000 employees. It is a subsidiary of the Aditya Birla Group, which spans numerous sectors and has annual revenues of $45 Billion.
Earlier today, the high-profile hacking group ShinyHunters leaked all of the data from its hack of ABFRL on an underground hacking forum. ShinyHunters is the same group that has hacked many other large businesses, including Microsoft, Tokopedia, Pixlr, Mashable, Minted, and more.
ShinyHunters explained that they have had access to the ABFRL network for many weeks
What data has been published?
ShinyHunters has now published private data from ABFRL that includes:
- ABFRL employee data (full name, email, birth date, physical address, gender, age, marital status, salary, religion, and more)
- ABFRL customer data and hundreds of thousands of invoices
- ABFRL website source code and server reports
Are you a customer or employee of ABFRL and have been notified of this data breach?
Please contact us here to provide additional details.
Negotiations failed, data posted online for free
The post and data are publicly available right now, and have been downloaded by others, but you need to be a member of the hacking forum to view the content. In the original post, ShinyHunters explained the rationale for releasing the data as follows:
We tried to get in touch with ABFRL. They sent a negotiator but he was just stalling (the offer was more than reasonable for a “US$ 45-Billion conglomerate”).
So we decided to leak everything for you guys including their famous divisions such as Pantaloons.com or Jaypore.com.-ShinyHunters, January 11, 2022
Below is the original source of this leak documenting that we captured on the hacking forum.
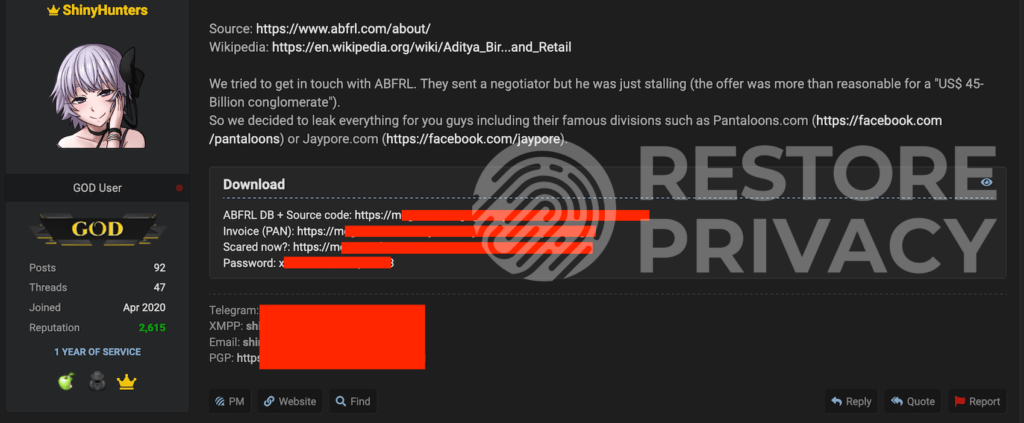
Source: RestorePrivacy.com
The post above does not discuss the exact amount that the hackers requested for payment, or when exactly ABFRL was first breached by the group.
ABFRL data analysis
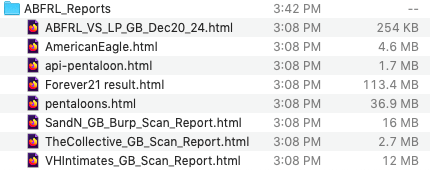
We have now obtained the data from ABFRL for our own analysis. The data is broken down into three large files and available for free.
Based on our initial analysis, we are seeing sensitive corporate data from many clothing brands that fall under the ABFRL umbrella in India. One batch of data that we have analyzed includes server logs and vulnerability reports for the following clothing brand websites in India:
- American Eagle
- Pentaloons
- Forever21
- The Collective
- Van Heusen
- Shantanu and Nikhil
- Planet Fashion
- Simon Carter
- Peter England
Another batch of data we analyzed contains financial and transaction information, with 21 GB of ABFRL invoices, including sensitive payment details, and customer information.
Update: ShinyHunters told us that they have extensive credit card data from ABFRL customers, specifically from Pantaloons.com, and this was communicated to ABFRL staff about two months ago. However, we are told that nothing has been done and it does not appear that anyone was notified about the breach.
ABFRL has not commented on (or denied) the breach
We contacted ABFRL’s press team to provide any comment on this story. So far, neither ABFRL nor the parent company, Aditya Birla Group, have commented on the data breach on any of their websites.
The parent company’s business reach spans many countries around the world. It is a large player in many industries.

We have not yet received any response, but will monitor the situation and update this article with any new information.
Potential impact of data breach for ABFRL employees, customers, and affiliates
With the amount of sensitive data in this release, many people could be impacted.
As we noted above, there is lots of private information that has already been released, including sensitive payment details. This puts ABFRL customers, employees, and affiliates at risk of:
- financial fraud
- identity theft
- phishing attempts
- social engineering attacks
- hacked accounts
- social security scams
As always, we recommend closely monitoring your bank statements, credit cards, financial information, email, and all online accounts for fraudulent activity.
Business model: Exfiltrate data, then demand ransom payment (without encryption)
Many people are aware of ransomware and the business model that goes with it. This involves hacking a server or network, encrypting the files, and then demanding a payout from the victim. This has been a popular attack for years as it encrypts files and prevents access with everything being encrypted with a private key.
However, we are now seeing a trend that does not involve encryption. In this new business model, a threat actor simply exfiltrates as much data as possible, and then demands a payment from the victim, with the threat of releasing all data should the negotiations fail.
Because the release of this data could be very expensive for a business, many are willing to negotiate a payment to make the problem go away and have the data deleted. This is particularly the case as we see class action lawsuits for data breaches and other long-term costs associated with networks and servers being hacked.
In short, it is often cheaper to pay a hacker to not publicly release the data than pay for the implications of the breach. Additionally, many hacking and ransomware groups will offer to assist the victim in patching security vulnerabilities that resulted in the hack.
ABFRL is ShinyHunters’ first big leak of 2022
As we noted above, ShinyHunters is a prolific and well-known hacking group. The hack of ABFRL marks the group’s first major release of 2022.
You can see other victims of ShinyHunters on the group’s Wikipedia page here. The group’s previous exploits include:
- Microsoft – 500 GB of Microsoft source code stolen and sold online
- Mashable – 5.22 GB of company and staff data
- Tokopedia – 91 million user accounts
- Pixlr – 1.9 million user accounts
- 123RF – 8.3 million user accounts
- Wattpad – 270 million user records
- Pluto TV – 3.2 million Pluto TV user records
- Animal Jam – 46 million accounts leaked
- WedMeGood – 41.5 GB of user data
- BigBasket – 20 million user accounts
- Dave.com – 7 million user accounts
- Couchsurfing.com – Data from 17 million users
- Dunzo – 11 GB of company data
- Nitro PDF – 77 million user records
- Bhinneka – 1 million user accounts
- Minted – 5 million accounts leaked
- ProctorU – 444,267 accounts
- Bonobos – Full backup database with 7 million customers and 1.8 million registered users
- Swvl – 4 million users
- Mathway – 25 million records
- Wishbone app – 40 million user records
Note: This list is not exhaustive.
We will continue to monitor the situation with the ABFRL hack and update this article as more information becomes available.







Can you please write an article that explains what SOCKS are? Should I use them on top of VPN?
No, you do not need to be using a SOCKS proxy, unless you have some specific need to for accessing services. From the Perfect Privacy website:
So as you can see, there is no additional encryption, security, or privacy benefit to a SOCKS proxy. However, you may want to use a SOCKS proxy if you are trying to access specific services (or servers), which may be blocking the VPN server’s IP addresses. So it is really about access and a specific use case where you would need a proxy to gain access.
Aside from Perfect Privacy, NordVPN also offers SOCKS proxies with any VPN subscription (with no additional charges).
I see thx
Nice to see that companies show some balls and stand up to these parasites.
Hi Sven,
Great article and investigation.
It is always so disappointing when a company won’t do the right thing and notify the victims.
There really needs to be an international agreement on protecting employees and customers;
Cyber-crime is boarder-less, and there isn’t a country in the world that would welcome their citizens being exploited by criminals. Why can’t we come to an international agreement on this? (rhetorical)
Have they dumped the credit card data in what you have downloaded or is it just the personal information?
I would have guessed credit card data would have a salable value and could be leveraged easily?
You note that there is a trend not to encrypt with ransomware.
The last I heard (and I don’t follow too closely) was that there was a trend to not only encrypt but to also exfiltrate;
Where the analysis was that exfiltration was secondary to the encryption, and served to add further leverage over the victimised organisation.
Can you offer any insight into why the modus operandi may have changed?
Regards,
BoBeX
There’s definitely still ransomware attacks going on all over the world where systems get encrypted and data is exfiltrated. But threat actors are increasingly just taking the data and demanding a payout (or extortion) to delete the data. In other words, they don’t need to encrypt files, because they have enough leverage (usually) by just threatening to release the data that was breached.
Edit: I found an article on cyber threat strategies that explains this in more detail.
You are wrong, bobex. The Shiny group did it first with Medlife and Upstox, then some hackers thought it would be a profitable way to make money. Unfortunately they are not as well known as ShinyHunters so ransomware extortion is currently the best approach.