
WhatsApp announced a new “Strict Account Settings” mode, a lockdown-style feature designed to shield high-risk users such as journalists, activists, and public figures from advanced cyberattacks.
On the same day, the platform also announced a significant behind-the-scenes security enhancement: a global rollout of Rust-based code across its media handling systems, replacing vulnerable C++ components to mitigate memory-safety flaws.
The timing of these announcements is notable. Just hours earlier, WhatsApp found itself on the defensive after a lawsuit filed in a San Francisco court alleged that Meta employees could access supposedly end-to-end encrypted messages through internal tools. WhatsApp has dismissed the claims as baseless and fiction-driven, pointing to the lack of technical proof and reaffirming its longstanding use of the Signal Protocol to secure the messages of over 3 billion users.
Lockdown mode for high-risk users
The newly introduced “Strict Account Settings” feature offers users an optional, high-security configuration that dramatically reduces potential attack vectors. Once enabled, it automatically:
- Blocks media and document attachments from unknown contacts.
- Silences calls from unfamiliar numbers.
- Applies additional restrictive controls that limit how the app functions, prioritizing security over usability.
This feature is intended for individuals who face a higher risk of targeted surveillance or intrusion, such as investigative journalists, human rights defenders, or political dissidents. It will be gradually rolled out in the coming weeks and can be accessed via Settings > Privacy > Advanced within the WhatsApp app. More details on how to activate this new feature are available here.
This development follows years of WhatsApp bolstering its privacy protections with end-to-end encrypted backups, secure calling enhancements, and the recent introduction of key transparency systems.
Replacing C++ with Rust
In a separate but equally critical move, WhatsApp has announced that it has completed a full-scale transition of its media handling libraries from C++ to Rust, a memory-safe programming language increasingly favored in security-critical environments.
This effort focused on replacing the “wamedia” library, which handles formatting and parsing media files such as MP4s. Originally introduced as a mitigation against the infamous Stagefright vulnerability on Android in 2015, wamedia has evolved into a key component of WhatsApp’s defense against malicious media payloads. Attackers often craft images, videos, or PDFs to exploit OS or app-level bugs. Because media parsers operate on untrusted input and run automatically, ensuring memory safety is crucial.
WhatsApp’s security team wrote a parallel Rust implementation of wamedia, subjecting it to differential fuzzing and extensive testing to guarantee functional parity with the original C++ version. The new codebase, which cut the number of lines by nearly half, has shown improved memory efficiency and performance across platforms.
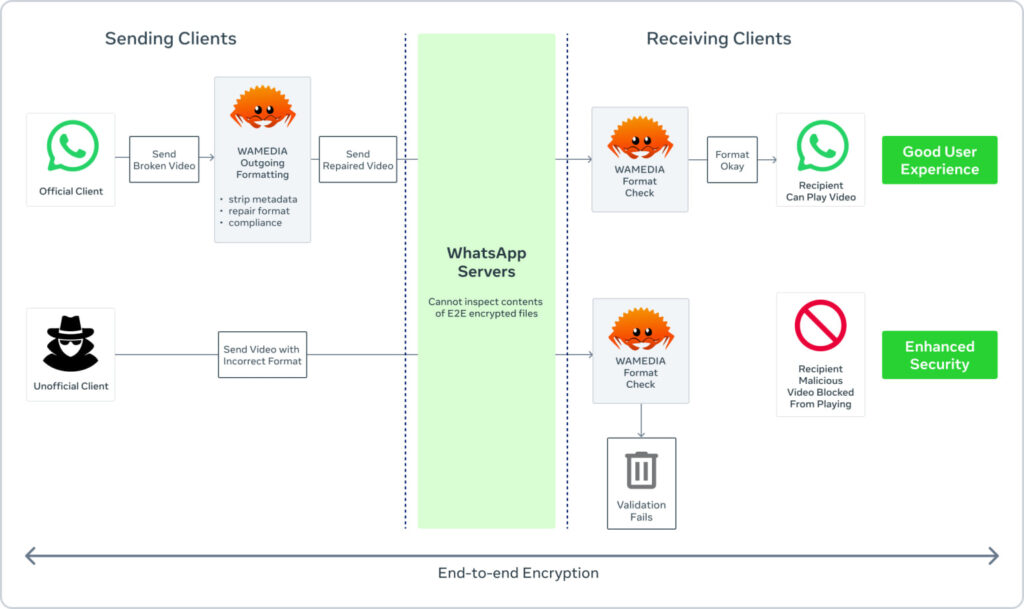
The rollout of this Rust-based media stack now spans Android, iOS, macOS, web clients, wearables, and other endpoints, making it the largest known global deployment of Rust in end-user software. This new architecture supports a proprietary scanning system called “Kaleidoscope,” which inspects file structure compliance, detects spoofed MIME types, and flags high-risk formats such as executables and embedded PDFs.
While both announcements represent years of engineering effort, the decision to publish them now seems strategic, as the lawsuit filed by users in Australia, Mexico, and South Africa has reignited public debate over Meta’s trustworthiness and WhatsApp’s encryption guarantees.






Leave a Reply