
AhnLab Security Intelligence Center (ASEC) and the National Cyber Security Center (NCSC) have identified a zero-day vulnerability, CVE-2024-38178, in the now-defunct Internet Explorer (IE) browser, exploited in a cyber espionage campaign named “Operation Code on Toast.”
This vulnerability was leveraged by the North Korean threat actor TA-RedAnt (also known as APT37), which targeted users through malicious advertisements in toast notification popups. Despite Microsoft discontinuing IE in 2022, this flaw impacted applications still using the browser's engine and, by extension, a large number of people.
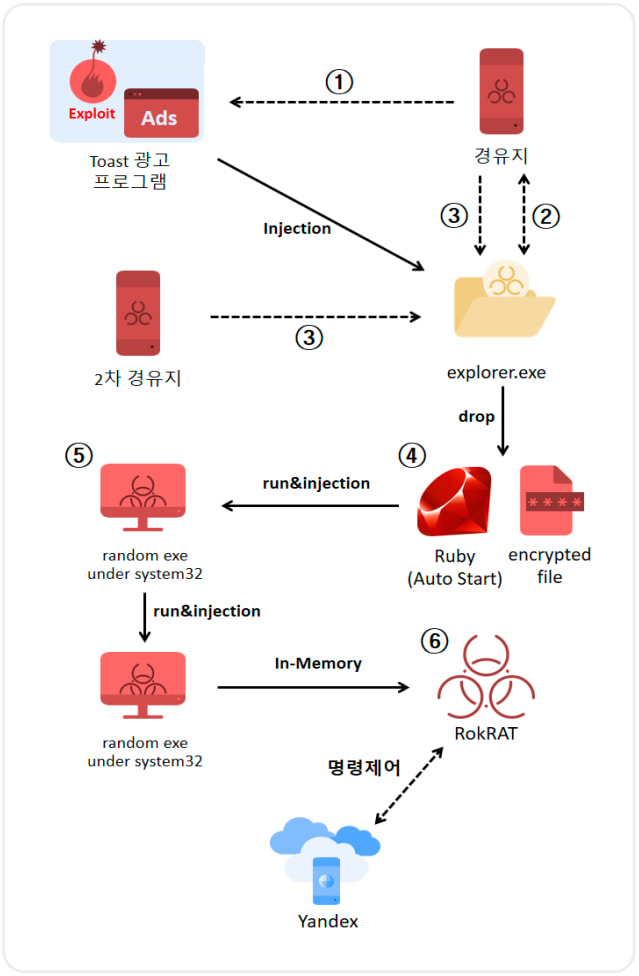
In May 2024, TA-RedAnt infiltrated a Korean online advertising agency’s servers, injecting malicious JavaScript code into advertisements delivered via toast ad programs. These ads, installed with various free software, utilized IE's outdated jscript9.dll engine to render WebView content. When users viewed ads through the compromised toast programs, the vulnerability triggered a zero-click attack, allowing the delivery of malware without any user interaction.
The vulnerability arose from a “type confusion” error in IE's JavaScript engine, where data was mishandled during optimization, enabling attackers to execute remote commands on compromised systems. Once infected, the toast programs installed malware capable of executing remote commands and performing additional malicious tasks, including data theft and system control.
ASEC
TA-RedAnt has a history of exploiting IE vulnerabilities to target individuals of interest, such as North Korean defectors and researchers. Past campaigns dating back to 2021 used similar techniques, often involving spear-phishing emails and malware-laden files. This latest operation underscores the continued risk posed by obsolete software components in current systems.
ASEC and NCSC reported the flaw to Microsoft in August 2024. Shortly after, Microsoft issued a security patch for the flaw, giving it a CVSS score of 7.5. The vulnerability was marked as actively exploited, and organizations were urged to apply this update immediately.
Despite the end of IE support, this case highlights the importance of regularly updating all software, especially those relying on deprecated technology. Ideally, users relying on IE either directly or indirectly (through other software) should consider replacing their tools with newer software as it now constitutes a security liability.
More information about ‘Operation Code on Toast’ has been made available in this paper, unfortunately only available in Korean at this time.







Leave a Reply