
A new variant of the “Shai Hulud” malware has been discovered in a sweeping supply-chain attack targeting npm packages maintained by Zapier, ENS Domains, Postman, PostHog, and several others.
The campaign, detected early Monday by Aikido's security researcher Charlie Eriksen, marks a significant escalation in a threat actor's ongoing operation that first surfaced in mid-September.
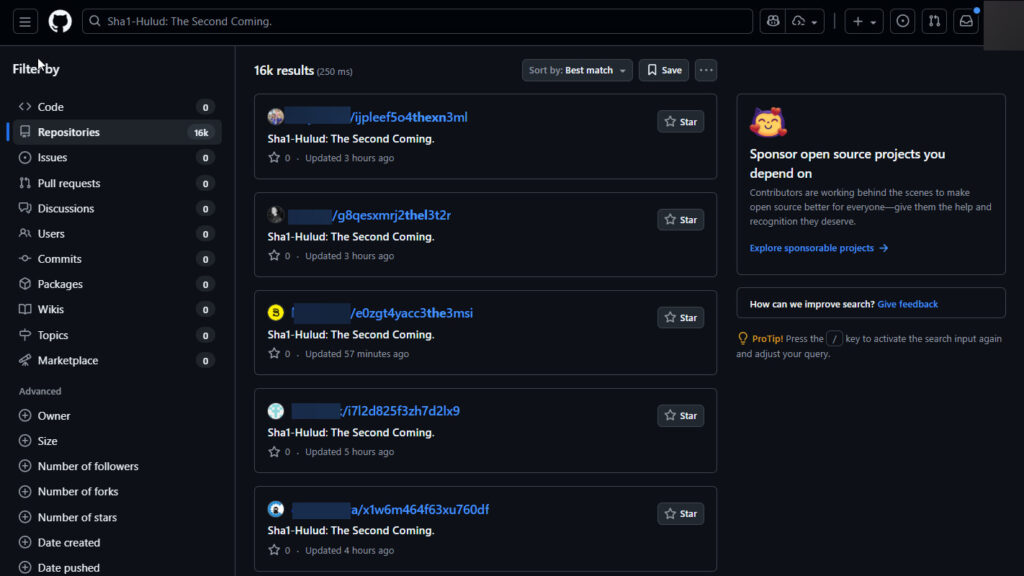
Eriksen identified the breach after spotting malware indicators in numerous npm packages submitted to a triage system within a short time frame. Upon analysis, these packages were confirmed to be laced with an updated version of Shai Hulud, an obfuscated JavaScript infostealer designed to harvest developer secrets. This latest iteration not only exfiltrates sensitive credentials but also publicly leaks them by uploading stolen data to randomly named GitHub repositories, each marked with the ominous description: “Sha1-Hulud: The Second Coming.”
Aikido
The compromise affects a wide range of software projects, many of which have deep integration with developer tooling, CI/CD environments, and infrastructure automation. Among the most impacted are:
- Zapier – a widely used automation platform that connects web applications. Numerous internal packages, including zapier-platform-core, zapier-platform-cli, and zapier-sdk, were published in compromised versions between 0.15.5 and 0.15.7.
- ENS Domains – a key infrastructure provider in the Ethereum ecosystem responsible for readable blockchain addresses, also saw dozens of packages compromised, including ensjs, ens-contracts, and react-ens-address.
- Postman – a dominant API platform, had internal packages such as pm-bin-linux-x64 and postman-collection-fork affected.
- PostHog – a product analytics platform with self-hosting capabilities, had core telemetry packages like plugin-server and rrweb infected.
Numerous smaller open-source projects and packages, spanning developers such as Trigo and OrbitGT, as well as several unaffiliated libraries, were also ensnared in the breach.
The threat actor's tactic mirrors the mid-September campaign involving the TinyColor package, where malware was surreptitiously injected into popular npm libraries. In that attack, discovered by Socket, the malware siphoned developer secrets including cloud credentials, GitHub tokens, and CI/CD secrets. However, unlike the earlier breach, this wave escalates the impact by immediately publishing the stolen data to GitHub, significantly increasing the risk of credential exposure and misuse by opportunistic third parties.
Early estimates suggest over 16,000 GitHub repositories may have already been seeded with leaked secrets from compromised systems, raising alarm across the software supply chain. The infection method again relies on developers installing or updating affected packages, either directly or through transitive dependencies. Once executed, the malware activates post-installation scripts to harvest secrets and initiate the exfiltration routine.
Developers using any of the affected packages who have updated since yesterday are strongly advised to downgrade to known clean releases, rotate all exposed credentials, and audit CI/CD pipelines for indicators of compromise.
Update 1: The campaign has been described in greater detail in reports by Koi Security, Wiz, and Socket, and is now believed to have impacted over 800 packages on npm, and published over 27,000 GitHub repositories with stolen secrets.
Koi Security also identified a data destruction mechanism that activates when the malware fails to steal secrets, wiping the developer's home directory.







Leave a Reply