A newly discovered Android banking trojan named Sturnus can bypass the encryption protections of secure messaging apps like WhatsApp, Telegram, and Signal by extracting message content directly from the screen after decryption.
The malware, still in its early testing phase, is fully operational and includes a wide array of capabilities ranging from credential theft to complete device takeover.
The new malware was identified by researchers at ThreatFabric, who observed Sturnus in targeted attacks against financial institutions in Southern and Central Europe. The malware supports phishing overlays, accessibility-based keylogging, environmental monitoring, and full remote control via VNC. It operates with high stealth, capable of hiding its presence using black screen overlays and administrator privilege protections that block uninstallation attempts.
Eavesdropping on encrypted messaging apps
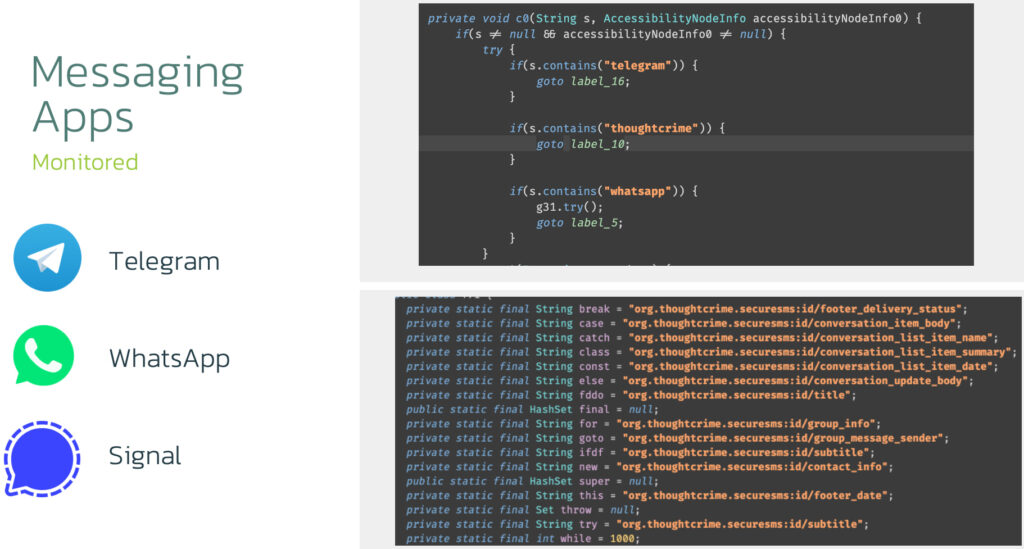
Sturnus' most alarming feature is its capability to capture communications from end-to-end encrypted messaging platforms, an ability that sidesteps the very security mechanisms these apps are known for. It achieves this not by breaking encryption, but by abusing Android's Accessibility Services to monitor screen content after messages are decrypted and displayed.
When a user opens WhatsApp, Telegram, or Signal, the malware detects the app in the foreground and activates its UI-tree collection pipeline. This system allows it to read all visible data on the screen in real time, including sender names, message contents, and timestamps. Because this surveillance occurs locally on the device, after the encryption keys have done their job, it neutralizes the protections offered by protocols like the Signal Protocol, giving attackers unrestricted access to private conversations.
This approach is especially dangerous because it leaves users with no visible warning. The app interfaces appear normal, and there are no indicators of a breach. Unlike traditional spyware, which may require root access or exploit vulnerabilities, Sturnus relies solely on permissions often granted by inattentive users, making it a potent tool for surveillance.
Credential theft and remote control
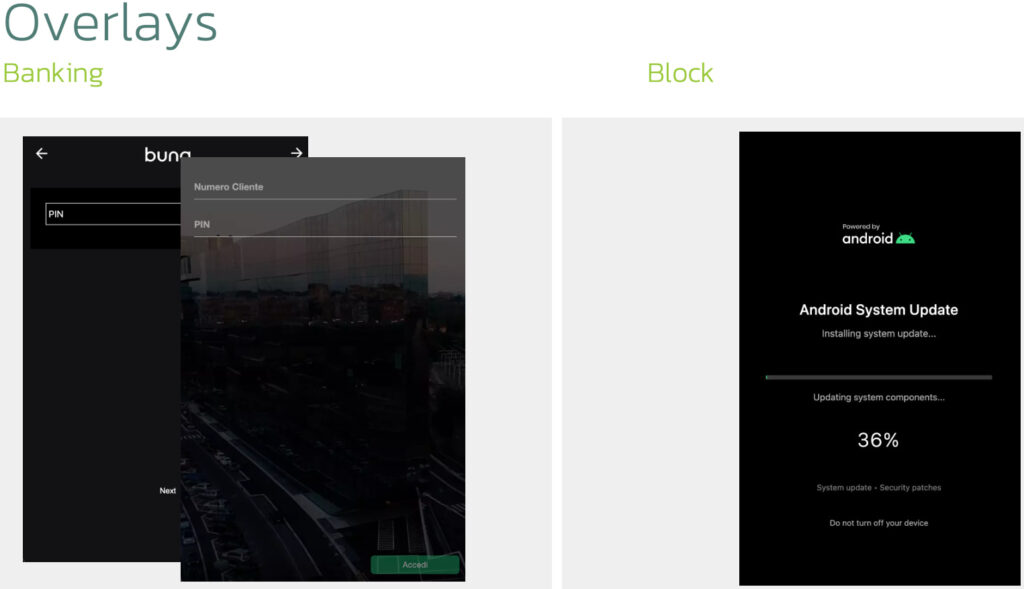
In addition to messaging surveillance, Sturnus carries a full suite of banking malware capabilities. It can display HTML overlays that mimic banking app login pages, enabling attackers to steal credentials. These overlays are stored locally and are tailored to specific financial institutions, suggesting a well-organized campaign.
The malware also captures every user interaction via key Accessibility events, allowing it to reconstruct user behavior in detail, even when screen capture is blocked by Android's security flags.
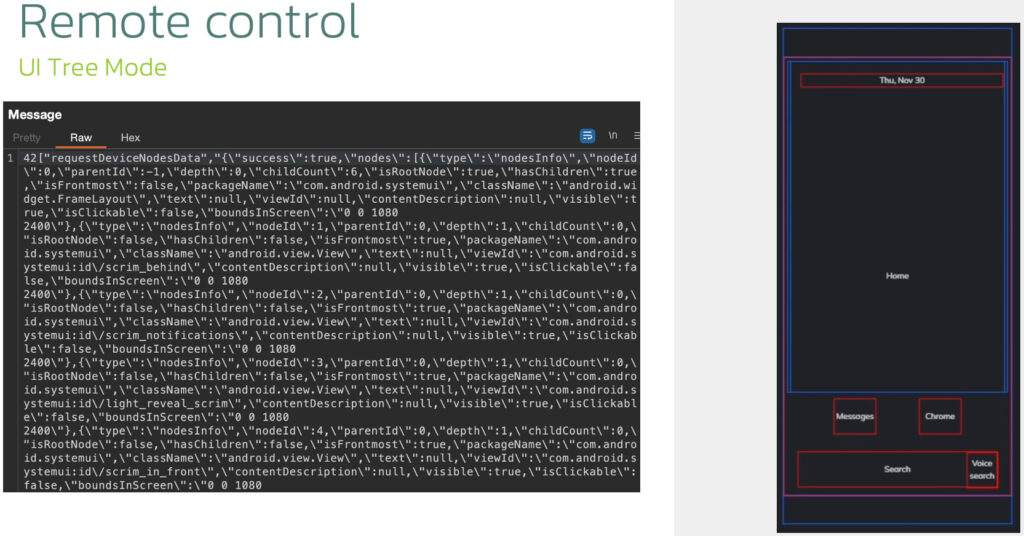
Sturnus provides operators with dual remote control methods, namely real-time screen sharing using Android's display capture API, and a low-bandwidth Accessibility-based interaction mode that maps and controls UI elements. This gives attackers precision control over the device, including the ability to inject text, click buttons, navigate screens, and conduct fraudulent transactions while masking their activity with a black overlay.
To protect against Sturnus, refrain from sideloading APKs from unofficial sources, check installed apps for Accessibility Service permissions, and use Play Protect to scan for and remove documented threats.







Leave a Reply