
ESET researchers have uncovered a new adversary-in-the-middle (AitM) tool used by the China-linked APT group PlushDaemon, which compromises router devices to silently redirect DNS traffic, enabling the hijacking of software updates and delivery of malware to Windows systems.
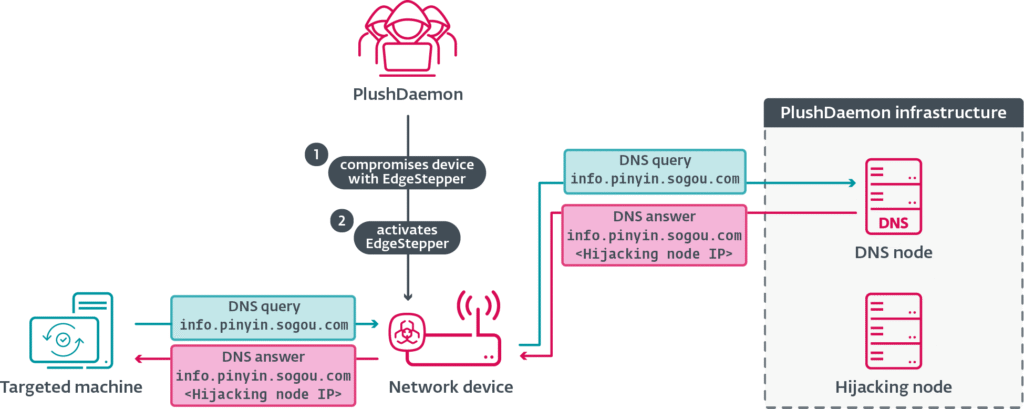
The discovery centers around a previously undocumented network implant dubbed EdgeStepper, found embedded in a suspicious ELF file named bioset. The implant enables PlushDaemon to intercept DNS queries from within compromised networks and redirect them to attacker-controlled servers, setting the stage for covert malware distribution. The implant intercepts outgoing DNS requests to reroute traffic intended for legitimate update infrastructure.
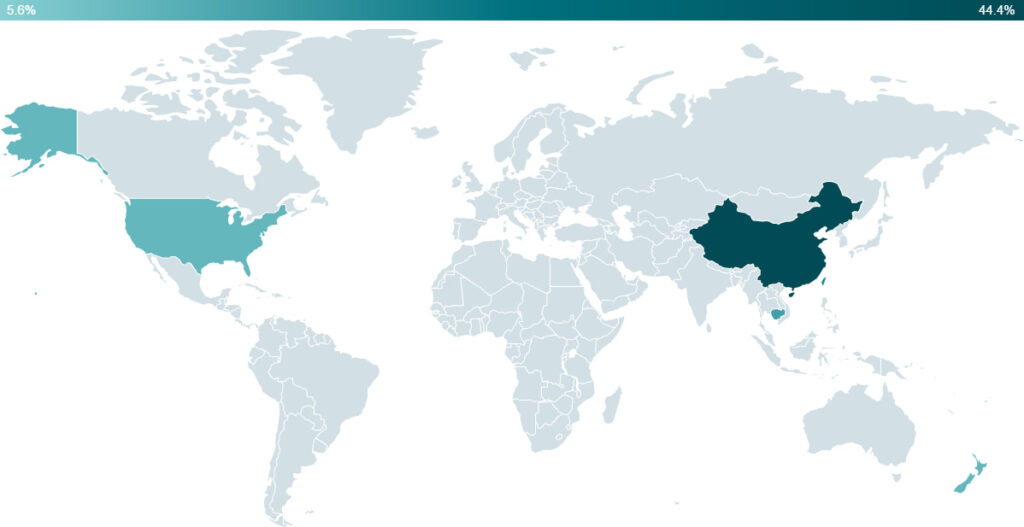
PlushDaemon is a long-standing China-aligned espionage group active since at least 2018. It has targeted individuals and organizations in the United States, Taiwan, China, Hong Kong, New Zealand, Cambodia, and South Korea. The group was involved in a 2023 supply-chain attack against a South Korean VPN service, Ipany VPN. Their operations often focus on intelligence gathering from strategic sectors, including manufacturing, academia, and software development.
ESET
The newly identified tool, EdgeStepper, is internally referred to by its developers as dns_cheat_v2. It’s compiled as a Go-based ELF binary for the MIPS32 architecture, likely designed for deployment on small-footprint network devices. Once installed, EdgeStepper decrypts configuration data using AES-CBC with hardcoded keys, then modifies iptables rules to redirect all DNS traffic (UDP port 53) to its own proxy service, listening on port 1090 by default. DNS queries are then conditionally responded to by malicious DNS nodes, which supply the IP address of attacker-controlled hijacking servers when update-related domains are detected.
ESET
ESET’s analysis revealed that this redirection allows the attackers to impersonate legitimate software update servers. The updating application, unaware of the rerouting, downloads malicious payloads like LittleDaemon, disguised as legitimate DLL files. These initial payloads are served over HTTP, often from subdomains such as ime.sogou.com, whose traffic is hijacked within the network before reaching real servers.
Once deployed, LittleDaemon acts as a first-stage loader. It checks whether the main PlushDaemon backdoor, SlowStepper, is already present. If not, it fetches a second-stage downloader named DaemonicLogistics, decrypts it using XOR-based operations, and executes it in memory. DaemonicLogistics then contacts the attacker’s infrastructure using seemingly benign update URLs, receiving commands and payloads encoded via HTTP status codes. These include instructions to download the full-featured SlowStepper implant or secondary payloads like plugin.exe.
Payload files such as file6.bdat and file2.bdat are delivered with specific magic bytes that signal how they should be processed. The decrypted payloads are written to disk in disguised locations, such as %PROGRAMDATA%\Tencent\QQUpdateMgr\UpdateFiles\logo.gif, as part of the final infection chain.
The infrastructure behind EdgeStepper has been active since at least 2021, with servers previously identified as origins for malicious update packages.
Organizations can defend against attacks like those orchestrated by PlushDaemon by segmenting critical update infrastructure, monitoring DNS traffic for unusual patterns like redirections, and enforcing HTTPS and code signing for all software update mechanisms.







Leave a Reply