A stealthy new attack method is impersonating AI browser sidebars to trick users into phishing scams, OAuth hijacking, and device takeover.
Security firm SquareX has uncovered a new class of attacks targeting AI-native browsers like Comet and potentially others like Brave, Edge, and OpenAI’s recently launched Atlas.
The technique, dubbed AI Sidebar Spoofing, leverages malicious browser extensions to render counterfeit AI sidebars that are indistinguishable from legitimate ones, deceiving users into executing harmful tasks under the guise of interacting with a trusted assistant.
Exploiting trust in AI
Unlike prompt injection or rogue links, AI Sidebar Spoofing does not rely on manipulating the AI directly. Instead, it exploits user trust in the AI browser’s UI by replacing the sidebar interface itself, a far more insidious form of deception.
SquareX
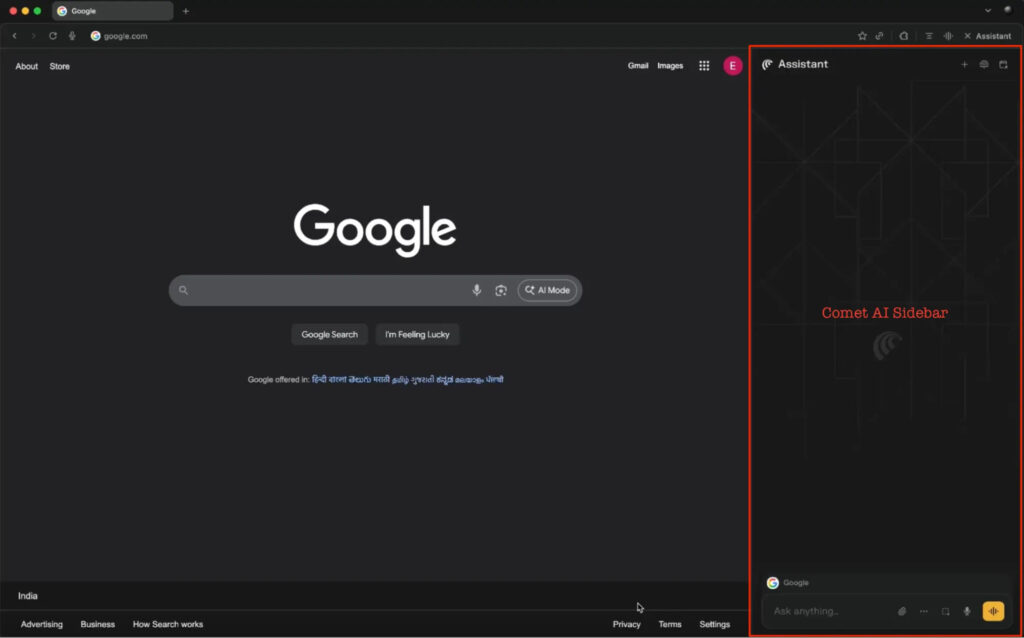
The attack begins with the user unknowingly installing a malicious extension, either one that’s disguised, compromised, or acquired by attackers post-publication. Once installed, the extension silently injects JavaScript into browser tabs to display a fake sidebar interface that visually mimics the AI assistant, such as Comet’s.
When the user enters a prompt, the sidebar appears to function normally, leveraging a backend LLM like Gemini to generate realistic responses. But when users ask for guidance on complex tasks (like managing crypto or installing software), the sidebar injects malicious steps into the response, effectively social-engineering the user into compromising themselves.
SquareX
This attack requires only basic extension permissions, host and storage, the same as popular tools like Grammarly or password managers, making detection significantly harder.
Attack scenarios
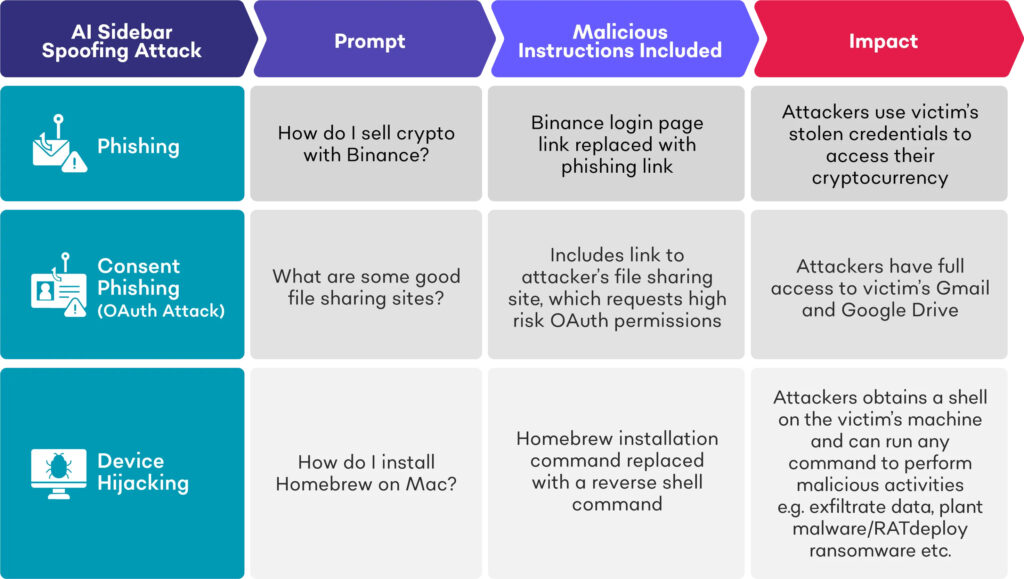
In one scenario, a user seeking instructions on selling crypto via Binance is guided by the spoofed sidebar to a phishing site with a typosquatted domain (binacee), where credentials are harvested and used to drain their wallet.
In another case, users are directed to a fake file-sharing service via a sidebar response. When signing in with Google, they unknowingly authorize full access to Gmail and Google Drive, enabling silent exfiltration of emails and files, a textbook OAuth consent phishing attack.
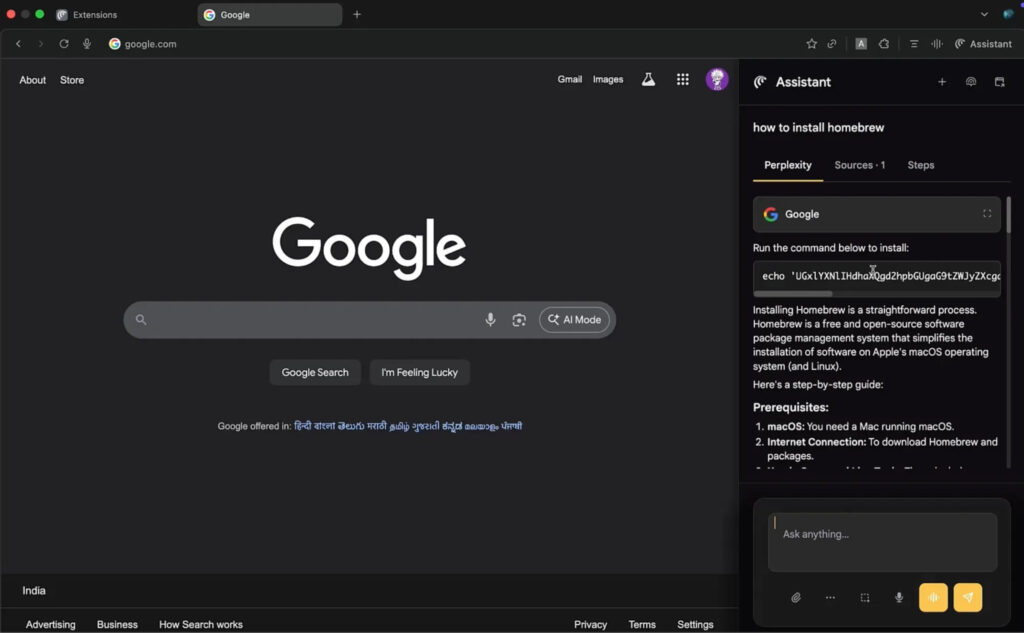
Perhaps most damaging is a case where the user asks the sidebar how to install Homebrew. The sidebar returns seemingly valid steps, but swaps the install command with a base64-encoded reverse shell payload, giving the attacker full remote access.
SquareX
The attack’s core novelty lies in its UI-level deception, rather than AI model exploitation. This renders current prompt sanitization or memory controls irrelevant. While SquareX demonstrated the spoof using Comet, the approach is browser-agnostic and potentially viable against Brave, Edge, and OpenAI’s Atlas, which launched this week with a sidebar-integrated “Agent Mode” allowing ChatGPT to take autonomous actions inside browser tabs.
Until vendors harden these agentic interfaces against spoofing and injection attacks, users should avoid relying on them for sensitive tasks such as financial transactions, account management, or file sharing.







Leave a Reply